The SSH protocol today is essential to securely manage servers, routers, switches and other types of devices, such as Wi-Fi controllers or APs. This protocol is one of the most used because it uses symmetric and asymmetric cryptography to provide confidentiality, authentication and integrity to the transmitted data. Today in this article we are going to talk about how to protect an SSH server with external tools, and we will also explain how to perform a complete security audit.
Monitor SSH server logs to detect attacks
SSHGuard is a program that will allow us to monitor the logs of our SSH server, to detect possible brute force attacks against the users that we are allowed to connect to our server. For a good administration of the information systems of an organization, it is very important to monitor the logs of different services, and thanks to SSHGuard, we will be able to monitor them to later detect attacks and block attackers using the firewall of the operating system itself.

This software will be in charge of monitoring the logs in different formats, specifically, it is capable of recognizing these logs in different formats:
- macOS
- metalog
- multilog
- raw log files
- syslog
- syslog-ng
- systemd journal
SSHGuard not only allows you to protect our SSH server, but it is also prepared to scan, detect and protect other essential services on any computer system. At first it was only OpenSSH compatible, but it has evolved and now we have all these services:
- OpenSSH (SSH Server)
- Sendmail (Mail Server)
- Exim (Mail Server)
- Dovecot (Mail Server)
- Cucipop (Mail Server)
- UWimap (Mail Server)
- vsftpd (FTP / FTPES Server)
- proftpd (FTP / FTPES Server)
- pure-ftpd (FTP / FTPES Server)
- FreeBSD ftpd (FTP / FTPES Server)
When SSHGuard reads the logs of the different system services, and detects some kind of attack, it will automatically block it using the operating system firewall. Logically, depending on the operating system we will have a specific firewall installed, currently SSHGuard is compatible with the following firewalls of systems based on Unix and Linux:
- FirewallD
- ipfw
- IPFILTER
- netfilter / iptables
- netfilter / ipset
- Pf
- tcpd’s hosts.allow
- IBM AIX’s firewall
Other interesting options are that we can create a blacklist of IP addresses automatically, in addition, it is also capable of monitoring several log files simultaneously. If you use the IPv6 protocol on your professional or home network, you are in luck because SSHGuard has full support for the IPv6 protocol.
Installation and commissioning of SSHGuard
This great tool to protect our SSH server, is available in the main software repositories of Linux distributions like Debian, ArchLinux, Ubuntu, OpenSUSE, and also in the FreeBSD Unix-based operating system. The installation must be done through the package manager of your distribution, if it does not exist, you can always download the software and compile it yourself, you can access the official website of SSHGuard to access its download.
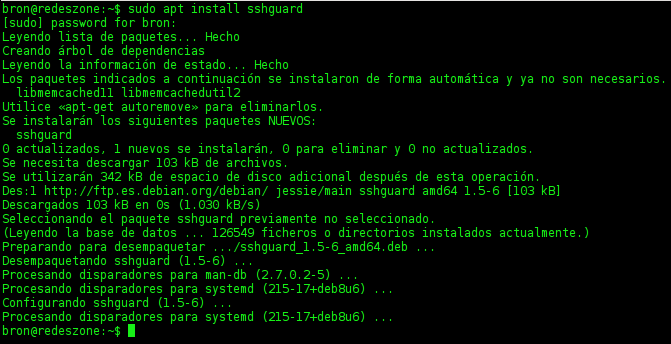
To start SSHGuard the first thing you should do is configure the log system on your server. If you do not know how to do it, there is a magnificent documentation on the official website of the software . Then you will have to configure certain parameters in the firewall, so that SSHGuard is able to block the IP addresses of possible attackers that we have completely automatically and without the intervention of the network or system administrator.
Check the security of your SSH server
If we have configured our SSH server with maximum security , as we have explained in this article, you should have no problem, however, it never hurts to check the security of your server with external tools.
Rebex SSH Check
The free and online tool Rebex SSH Check will perform a quick scan of the key exchange algorithms, symmetric encryption algorithms, key algorithm, as well as the MAC algorithms that we currently have configured on our SSH server. If we use any algorithm that is not currently considered safe, it will tell us, so that we can later configure the SSH server correctly and remove this algorithm from the “allowed” ones.
The first thing we will have to do is enter the official website, we will see that it asks for both our IP address or domain, as well as the port where the SSH server is listening. When we have entered the data from our SSH server, click on the “TEST” button.
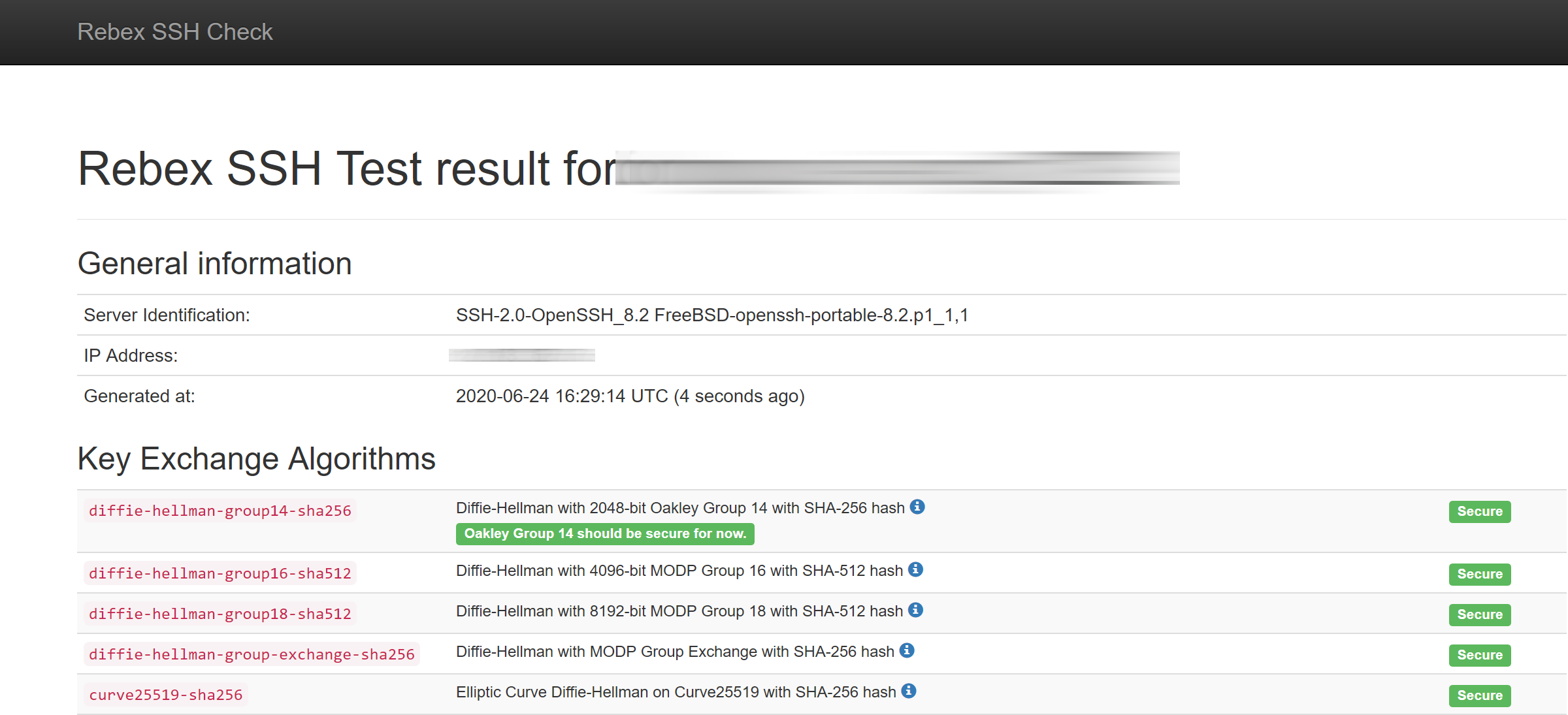
The process of checking the security of the SSH server takes about 10 seconds, and it will inform us of all the algorithms that we can use, and whether or not they are safe. For example, in our case with the XigmaNAS SSH server with the default values, we obtain that the security is outstanding, since it makes use of all the secure symmetric and asymmetric encryption algorithms, discarding the vast majority of the old ones.
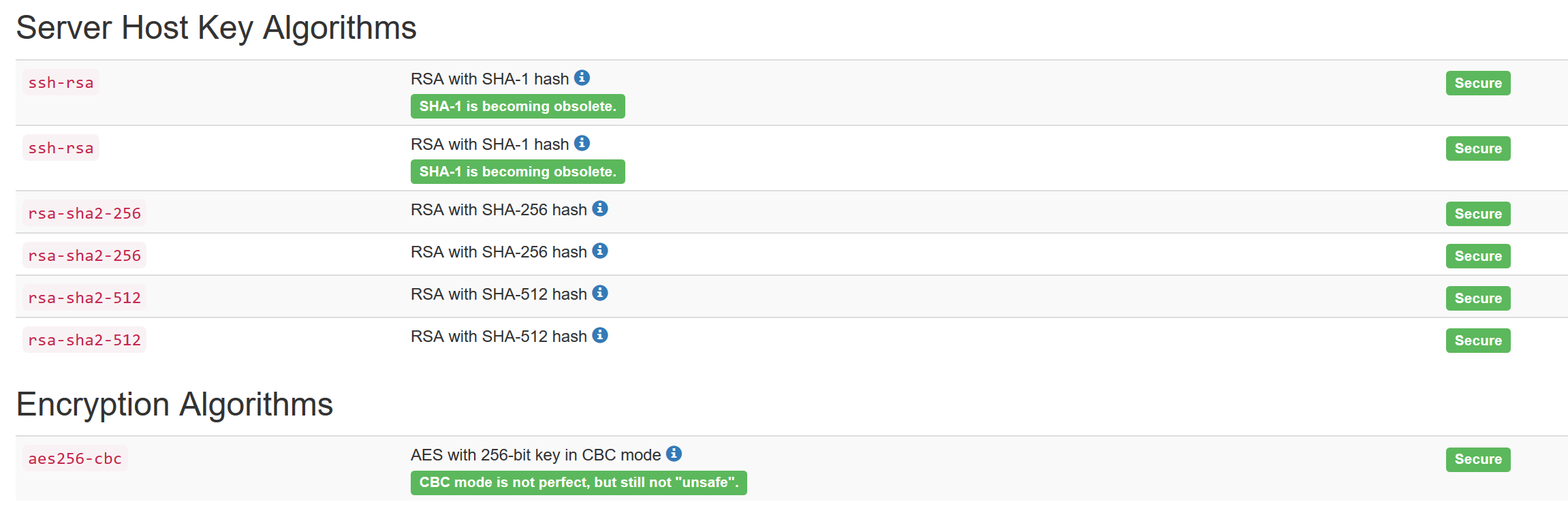
This tool is also capable of checking the server key algorithms, as you can see, it informs us that the one used with SHA-1 is “safe” but it already informs us that it is obsolete, and that it is recommended to always use SHA2- 256 or higher, so in the configuration file we could remove this algorithm.
We will also have the symmetric encryption algorithms available, we only get one because we have it defined in the configuration file. This tool is also very useful to verify that the security settings are indeed what we want.
Finally, it also indicates the MAC algorithms that we have available on the SSH server, some of them as you can see are considered as insecure, so it is advisable to remove their support as soon as possible:
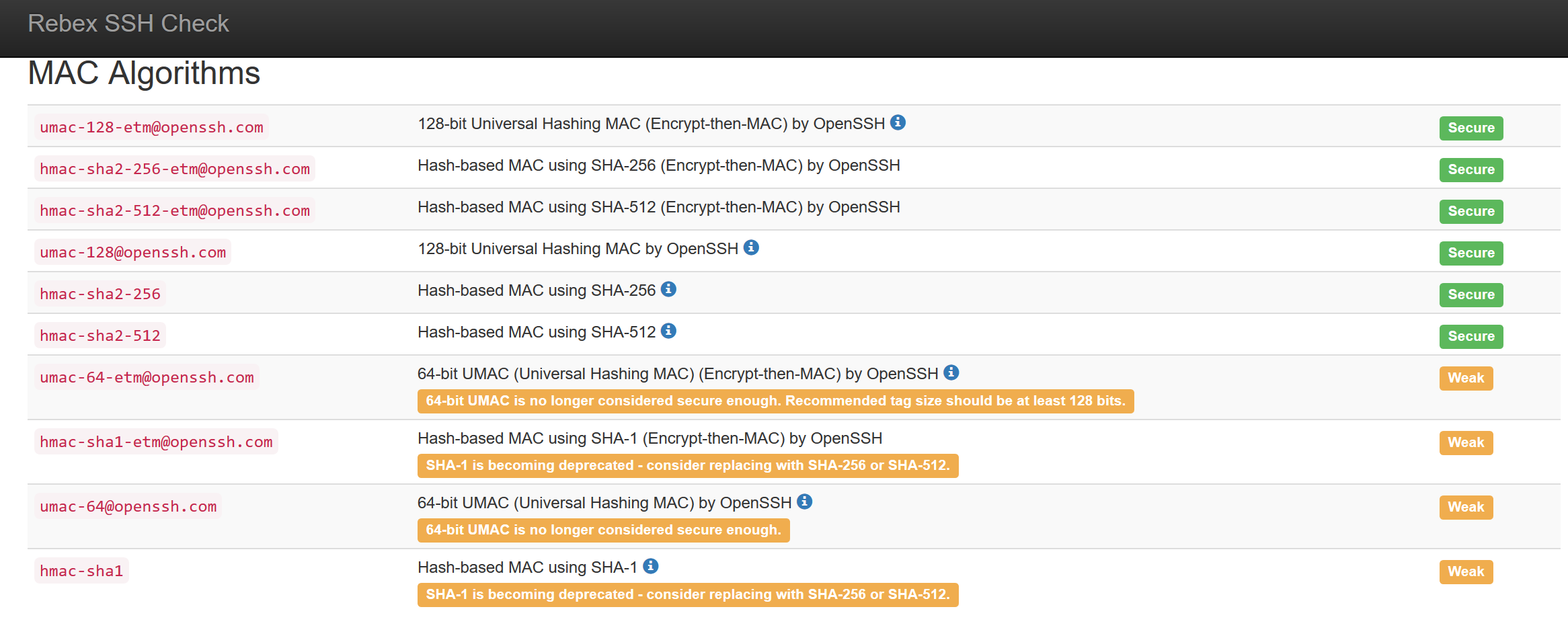
Other data that this service is capable of providing us with is, if we use any type of compression, and if we use it, it will tell us what type of compression we have activated in the server configuration file. Finally, it will also inform us about the public key of the server, including the MD5 fingerprint, SHA2-256 and even the public key that we use:
 As you have seen, thanks to this great completely free online tool, we can easily and quickly check the security of our SSH server.
As you have seen, thanks to this great completely free online tool, we can easily and quickly check the security of our SSH server.
ssh-audit
ssh-audit is a totally free tool, written in Python and that will be in charge of scanning the configuration of our SSH server, this time, we do not have an online tool, but we will have to run it on the server itself where we want to check the SSH security. ssh-audit will tell us if the different configurations that we have applied are safe, insecure, or have any weakness, ideal for later making changes to said SSH server.
Some of the main features of this free tool is that it will allow us to detect the login banner, if we are using an insecure protocol like SSH1, and even if we are using zlib library compression. You will also be able to verify the key exchange algorithms, the host’s public key, symmetric encryption when communication has already been established, and also the information authentication messages.
When ssh-audit has analyzed all these parameters in a fully automated way, it will produce a complete report indicating when a certain option is available, if it has been removed, disabled, if it is insecure, weak or if it is safe. Depending on the severity of the configuration made, we can see different colors in the warnings.
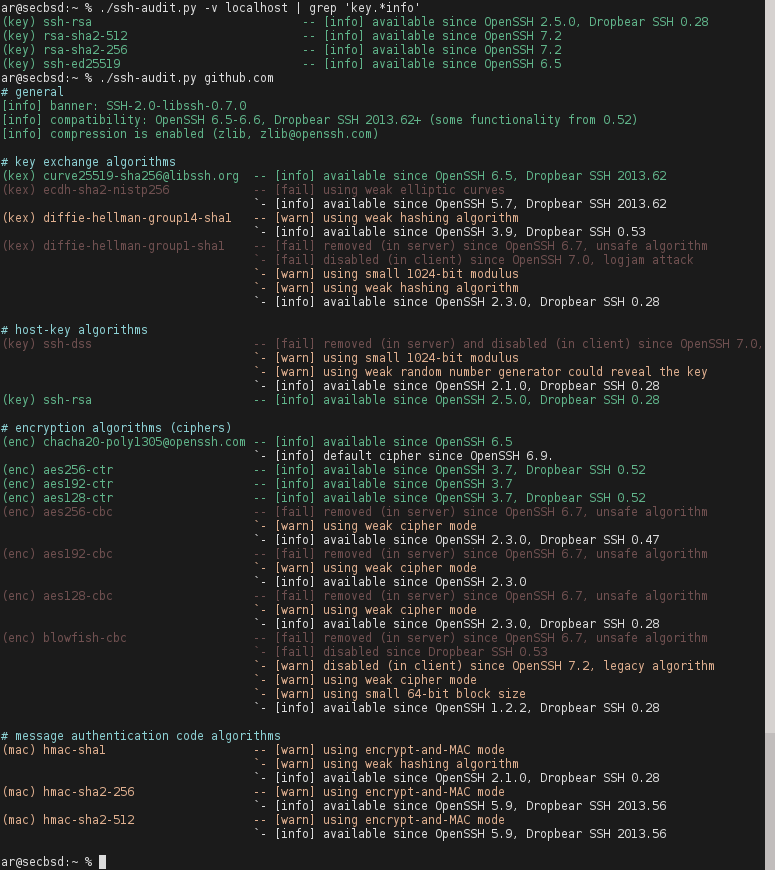
This tool will also show us the version of SSH used, in addition, it is compatible with OpenSSH and Dropbear, the two most used SSH servers in operating systems and in devices such as routers, switches, etc. This tool is more advanced than the previous one, since it will provide us with more information.
To use it, all we have to do is download the .py file from the official ssh-audit GitHub , then we will run it like any other Python tool as follows:
python ssh-audit.py [-nv] host[:port]
The argument -n will disable the different colors in the output of all the information, and the -v will show us absolutely all the information that the tool gives us.
As you have seen, protecting with external tools and checking the security of your SSH server is very easy. Although SSH is a secure protocol, it is always necessary to configure it correctly to avoid problems or attacks.