Cybercriminals are always on the lookout and looking for victims for profit. Sometimes they simply exploit vulnerabilities in programs that we have on our computers. Others, however, prepare malicious software attacks using the most sophisticated and innovative techniques. They do not do this for the love of art, they seek to make their work profitable and increase their personal assets. The objective of these cybercriminals is to steal our data to obtain economic profits. In this tutorial, we will explain how hackers make money by conducting ransomware attacks, phishing, and more.
When we think of the most common ways a cybercriminal can make money, the first three that come to mind are usually malware, phishing, and ransomware. While it is true that they constitute a good part of a cybercriminal’s income, it is no less true that they have other interesting options. Throughout the tutorial, we will mention the three ways mentioned above, and explain some of the less talked about ones, such as Cryptojacking.

Ransomware and its consequences
One of the favorite ways hackers get money is by using ransomware attacks. The moment we receive an attack of this type, malicious software proceeds to encrypt all our data on the PC on which it is running. Furthermore, there is also the possibility that all data that is shared on the local network is encrypted. For this reason, it is not enough to protect our computer, we must also check all the equipment in the office or at home.

The best way to get back to normal would be by deleting and restoring the affected computers using our backup copies. In this article we recommend that you practice a good backup policy that may consist of:
- The periodic storage of our essential files.
- A storage of the copy on a medium different from that of the origin. An example could be an external hard drive that needs to be put away. If we do not do this, a hardware failure of the source media would cause total data loss. Therefore, having a copy at two or more sites is a good idea.
- If the data is stored on another computer, it must have up-to-date software and be properly protected.
The other option to recover data is to use a decryption key to be able to unlock files and data. The disadvantage it has is that to obtain that key we have to pay a ransom. Thus, one of the main sources where hackers make money is with ransomware campaigns.
The consequences they generate is that they interrupt our commercial operations with the addition that we can even lose data. Also, if we talk about the workplace, we are going to face downtime, loss of productivity, income and reputation. Not to mention that our confidential business information could be publicly disclosed or sold to the highest bidder.
Evolution of ransomware attacks and what to do if we experience one
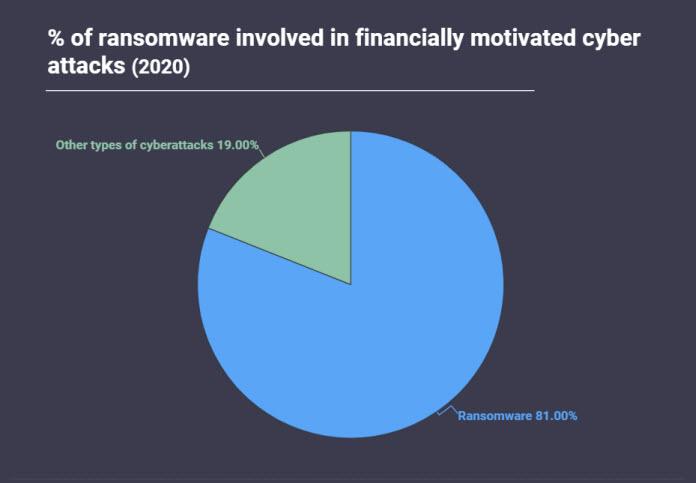
Without a doubt, attacks of this type have seen a considerable increase. According to a study by Atlas VPN security experts, 63% of all attacks in 2020 were financially motivated. Of this percentage of 63%, whose main purpose is economic, 81% were ransomware attacks.
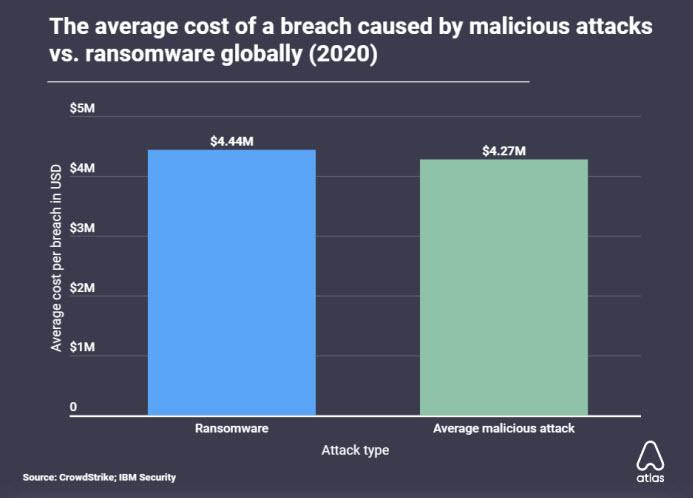
An average malicious software attack costs companies $ 4.27 million per attack. However, with a ransomware attack, you get 4% more, averaging $ 4.44 million per attack.
One thing to keep in mind is that paying a ransom does not always mean that we are going to recover the data. Sometimes the ransomware decryption doesn’t work, or you lose some of your data. Another thing you should know is that, although the files are well decrypted, it is also likely that it is still infected by malware, Trojans and keyloggers. In this sense, our equipment may not be secure, so we can remain in the hands of cybercriminals.
Without a doubt, ransomware attacks have become one of the main threats that hackers use to make money. The best way to avoid this is by reporting and having an incident response plan where backup will be an important factor.
Malware in general
Some cybercriminals, to steal our information, use different types of malware. Some malwares of this type are those that register the keystroke, those that specialize in stealing information and the banking ones. Usually, this malicious software seeks to obtain information on:
- Credit cards
- The login credentials of our accounts
- Autofill data from browsers
Infection with malware generally occurs thanks to email attachments, malicious advertising, and pirted software.
Phishing and tips to protect ourselves
Another resource where hackers make money is using Phishing attacks. These types of attacks generally aim to obtain the login credentials of our accounts. As a hook, we have a message that masquerades as a legitimate company or organization, such as Microsoft, Facebook, Twitter, Instagram etc. This message that we usually receive contains a link that directs us to an attacker’s web page or to a malicious file.

In this case, we are faced with a clear case of company identity theft. Thus, the victim will believe that he is on the official website of said company when in reality, it is a fraudulent page. The objective of a Phishing attack is for the user to log in normally, entering the username and password of their account, which will end up in the hands of the cybercriminal.
Some strategies that we can use to avoid being a victim of a Phishing attack are:
- Don’t log in from email links.
- Nor should we open or download attachments from unknown sources.
- We have to do an analysis of the grammar and the aspect of the message. In the event that the text has spelling mistakes, and looks like a translation from other languages, be wary.
Another way at the individual level would be to protect our accounts with multi-factor authentication . On a business level, Phishing awareness courses can be a good starting point. In them, workers learn to distinguish these types of attacks, and to know how they should act in the event that they receive them.
Cryptojacking: another common option for cybercriminals
As a consequence of the increase in value that cryptocurrencies are experiencing, a new way has appeared in recent years where hackers take money. This is none other than Cryptojacking, or malicious cryptocurrency mining, in which a third-party computing device is used to extract digital currencies. This problem affects both PCs, smartphones or computer networks. In this case it is not used to obtain user data but to mine cryptocurrencies.

The problem affects different operating systems like Windows, Linux and Android. In the affected computers, it will also cause:
- Loss of resources, since part of it is going to be used for mining cryptocurrencies.
- Higher energy expenditure, obviously as we are performing more tasks we will spend a little more light or battery.
- Wear and tear of the hardware for something that we are not using, and that one day may take its toll.
Therefore, hackers make money with cryptocurrencies, they do not waste energy or wear out their equipment.
Other ways cybercriminals use to make money
We have already discussed the most common ones, but other sources of income for cybercriminals should also be noted, since they can take advantage of stolen data to:
- The purchase of articles on-line.
- Withdraw money from your bank account.
- Apply for credit cards.
- Selling login credentials for gaming, video, or music platform accounts.
Ultimately, hackers make money in many different ways. In that sense, we must be vigilant and protect our computers by keeping them updated along with the appropriate protection software.