Tor Browser is one of the best options we have to browse the Internet safely and anonymously. There are browsers like Opera that have a built-in VPN , but with Tor we have the possibility to access the Deep Web, and to use an unbreakable anonymization system. Or at least when no bugs or vulnerabilities are found.
This has been alerted by FingerprintJS , developer of a library used for fraud prevention. The company claims that it has identified a new fingerprinting technique capable of generating highly consistent identifiers across web browsers, including through Tor Browser. The company claims that they use fingerprinting, not through vulnerabilities like this one, but through what JavaScript allows “legally”. Therefore, they have made this vulnerability known to the public so that it can be fixed.

Fingerprinting, more dangerous with this technique
Fingerprinting consists of modeling the way a user uses the browser based on how they move the mouse, the resolution they use, the websites they visit, the content they read, the apps they have installed, etc. These techniques are increasingly refined, and allow a company to model people through different web browsers and devices, even when that person is browsing incognito or without accessing their personal accounts.
With this, if you use Chrome to view some websites, and Tor to view others anonymously, it is possible that someone can identify you through the way you browse, deaninomize you to track you on the Internet, and even identify you. This technique has been baptized by the company as “scheme flooding”, referring to the URL schemes used to open links such as “skype: //” to open them with the program associated with them in the operating system.
With this, an attacker can find out which apps the user has installed. For example, a website can check a list of 32 popular applications to see if they are installed on the system. On the web https://schemeflood.com/ we can check how unique our ID is based on the URL schemes that we have opened in the browser. In my case, I have recently opened Skype and Spotify, making my identifier 98.78% unique. The tab must be active for the attack to take place.
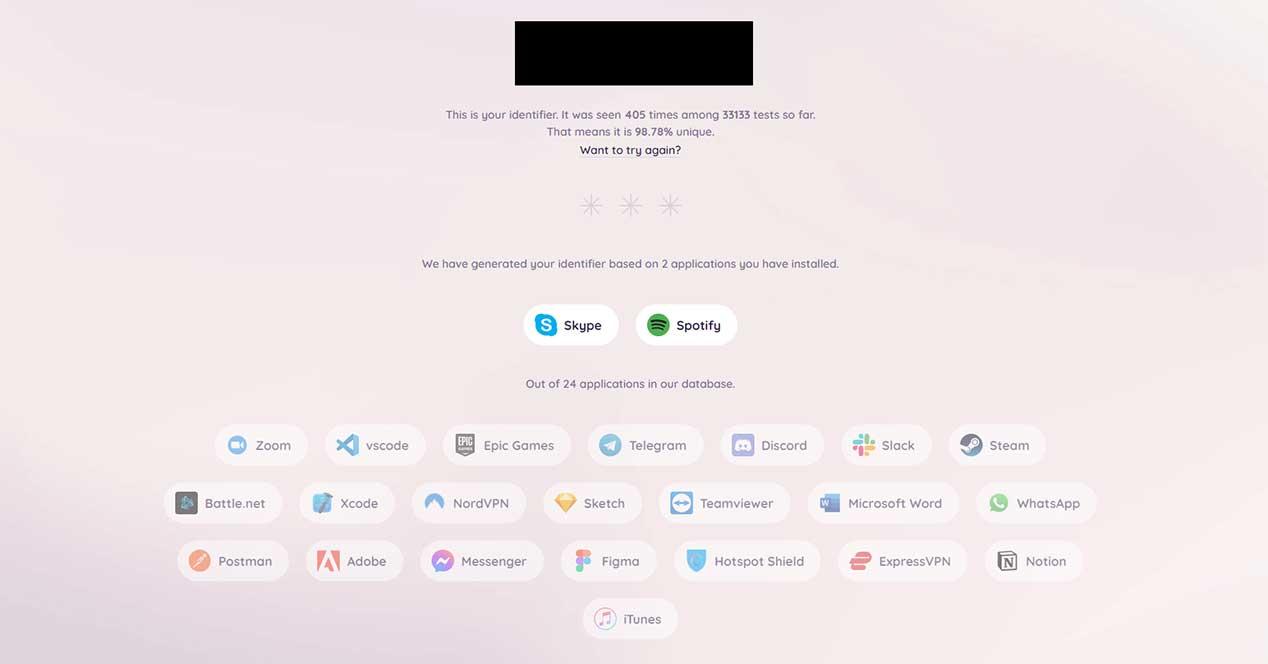
Browser developers are warned
The website performs the verification in the same way that any other website can do it. The script aborts if the app is present, or throws an error if the app is not. With this, the installed apps are gradually displayed. In some browsers it can give errors, in addition to other factors such as slow hardware, the use of virtual machines, etc.
The fault in this case lies with the browsers, which should not allow the use of this type of technique. Most extensions force the user to interact with them, but others such as those that the Mail app or a PDF opens directly to us do not require interaction, leading to abuse.
The Chromium team is currently thinking about how to fix these types of attacks, since they can be used together with a lot of other user information to create unique identifiers with a very low margin of error.