The PGP (Pretty Good Privacy) protocol is a program developed by Phil Zimmermann to protect information distributed over the Internet, making use of public key cryptography, either using RSA or EC, to facilitate data encryption and also the authentication of information thanks to digital signatures. OpenPGP is the most widely used mail encryption standard in the world, it is defined by the IETF as a standard, OpenPGP is a derivation of the original PGP. Today in this article we are going to teach you how to send encrypted and authenticated emails with digital signature using OpenPGP in Thunderbird.
How does OpenPGP work to send emails safely?
OpenPGP is a hybrid cryptosystem, it uses both symmetric and asymmetric cryptography, with the aim of having the best of both technologies. We must remember that symmetric encryption is much faster than asymmetric encryption, but the latter allows us to solve the problem of distribution of encryption / decryption keys in a secure way. Thanks to this hybrid cryptosystem, we can ensure that both the information sent and the encryption / decryption key are safe. The symmetric encryption used by OpenPGP is AES-256, and regarding asymmetric encryption, we can make use of RSA or EC.

Other features of OpenPGP are that it provides compression, to reduce cryptanalysis attacks. These types of attacks consist of looking for patterns with the plaintext and the encryption to try to break the encryption of the data. Compression is done before the content is encrypted, thus reducing patterns in the clear text. Asymmetric encryption keys are kept protected by a password , to prevent other users from using it without permission. Of course, as in any public cable scheme, we will have a private key (which must not be shared) and a public key (which must be shared).
The OpenPGP operating process is based on:
- Sender will create a key pair (public and private), and send the public key to the receiver, and could even upload said key to a public key repository. The private key should never leave the issuer.
- The receiver will also create a key pair (public and private), and send the public key to the sender, and could even upload said key to a public key repository. The private key should never leave the receiver.
Once the sender has their key pair and the receiver’s public key, and the receiver has their key pair and the sender’s public key, they can begin to communicate with each other. The communication process would be like this:
- The sender will send an email encrypted with the receiver’s public key, so that the receiver is able to decrypt the message with his own private key. Normally, the sender also attaches his public key in case the receiver does not have it in his repository.
- The receiver, if he wants to reply to this email, will send an email encrypted with the public key of the sender that he has just received, so that the sender is able to decrypt the information with his own private key (that of the sender). Normally, the receiver also reattaches its public key, in case the sender does not have it in its repository.
With these actions, the confidentiality of the information is achieved, since everything will be encrypted, and without the corresponding private key it cannot be decrypted.
If we want to give this same communication scheme authenticity, to ensure that the sender is who he says he is, and the receiver is who he says he is, we must use the digital signature. The digital signature process would be as follows:
- The sender will send an email signed with his own private key, so that the receiver can verify the signature with the sender’s public key (which he already has in his possession).
- The receiver will send an email signed with his own private key, so that the sender can verify the signature with the receiver’s public key (which he already has in his possession).
This authentication process is in addition to the data encryption process, but it is highly recommended to always do it to verify that the emails received are legitimate. Thanks to confidentiality and authenticity, we can send emails in a totally secure and private way.
Currently the latest version of Mozilla Thunderbird makes use of OpenPGP without the need for any additional plugin, the old versions needed a plugin to be able to work correctly, and also needed a public / private key generation program, now this is not necessary, because it comes integrated into the Thunderbird program itself.
Download and install Thunderbird and mail configuration
To download Thunderbird , we have to go to the official website and click on ” Free Download “, we must remember that this email manager is completely free. On the main screen we can find the main features, the main configurations that we can make and why it is one of the best options for managing personal or company email.
This program has a large number of add-ons that allow us to have additional security, and additional functions or features of high added value. For example, we can download extensions to check spelling, to check the mail server’s DKIM, to customize in detail the graphical user interface of Thunderbird and much more.
Before, we had to download a plug-in to have OpenPGP in our Thunderbird, however, with the latest versions the incorporation of OpenPGP is default, therefore, we will not have to add any additional extension.
The installation of Mozilla Thunderbird is exactly the same as always, we run the installer, choose the “Standard” installation, put the location of the program and click on “Install”. In the last menu, we will confirm that it has been installed correctly, and click on “Finish” to run Thunderbird now and start with the configuration.
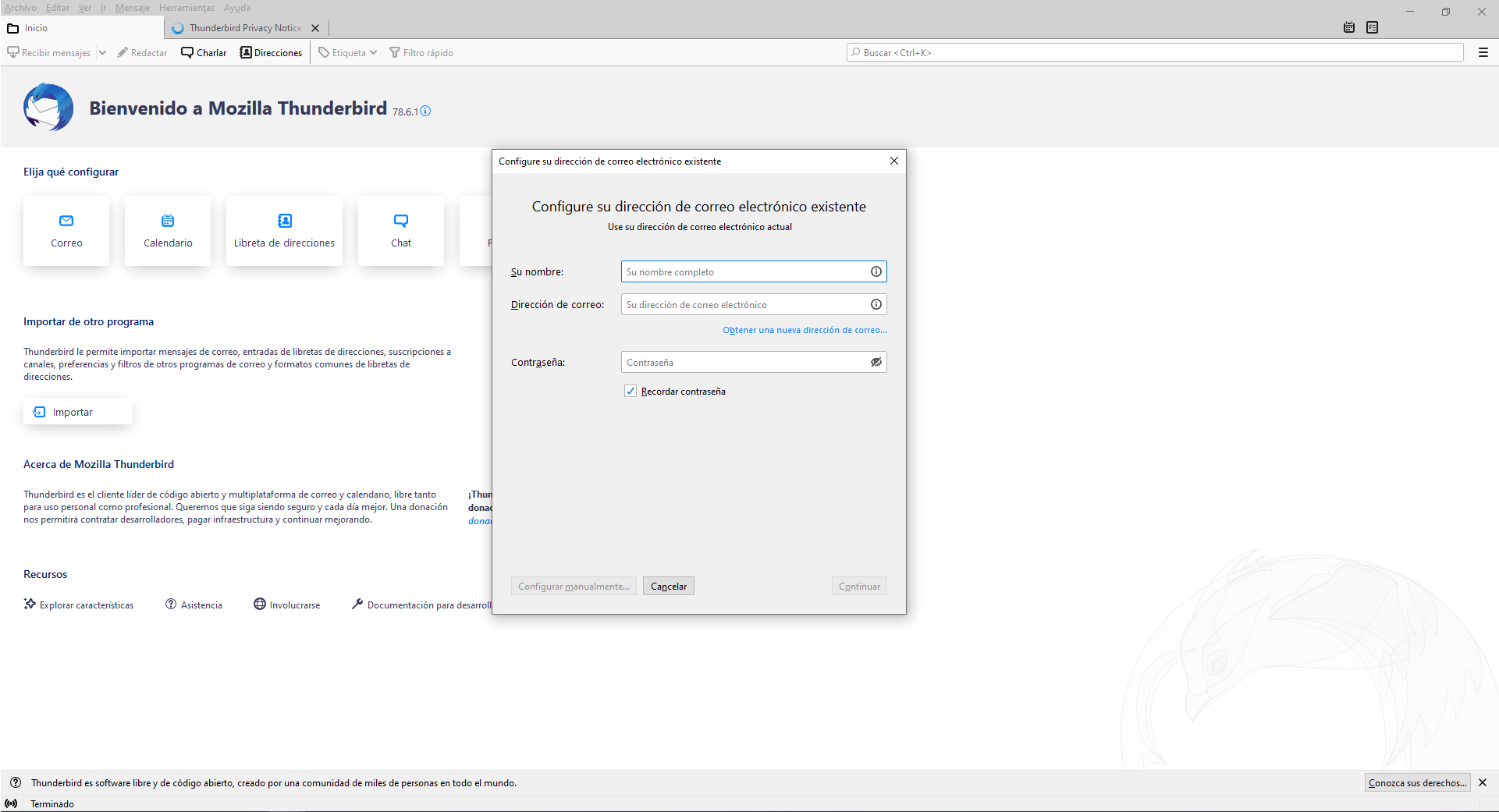
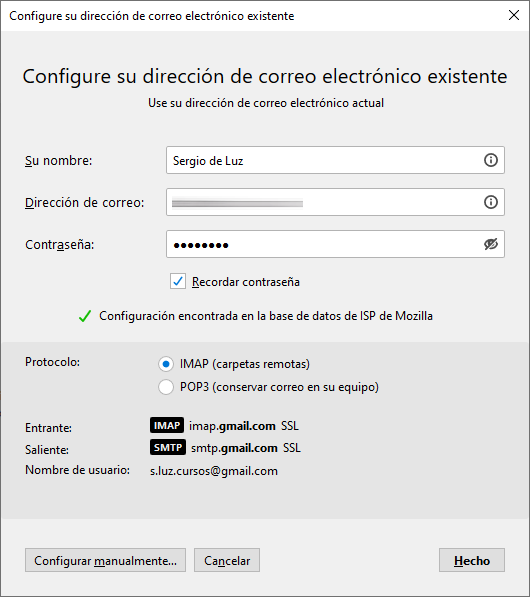
The first thing we will have to do in Mozilla Thunderbird to be able to use it is to register an email address. This email can be from Gmail, Yahoo, Microsoft Outlook, or whatever other mail server you are using. If the mail that we put is in the Thunderbird database, the configuration of the IMAP and SMTP protocol is automatic, otherwise, we will have to indicate it “manually” by putting the ports and different options available in the mail client .
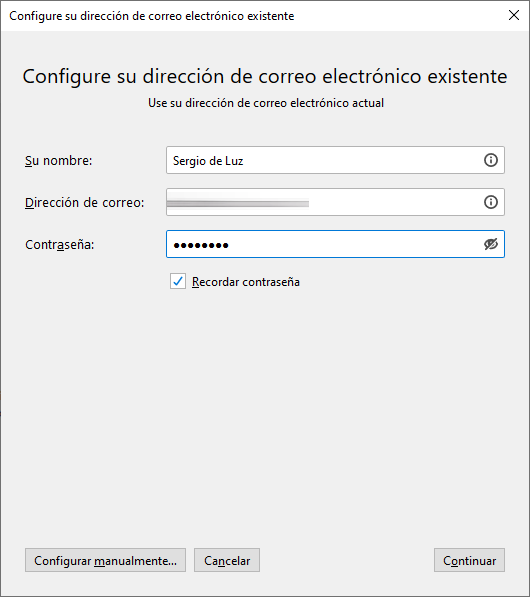
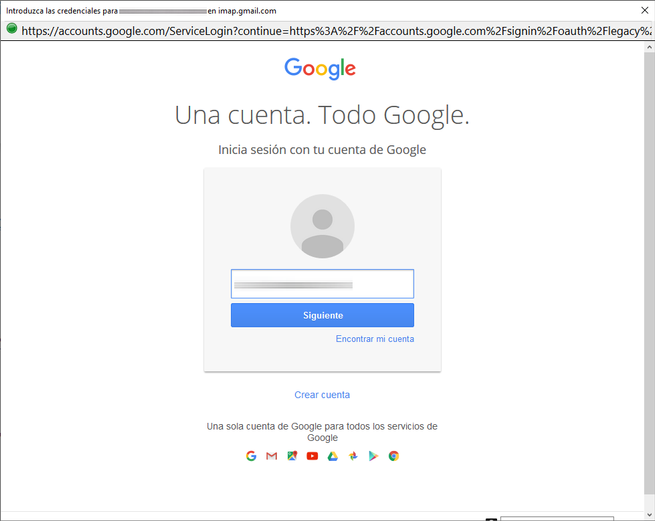
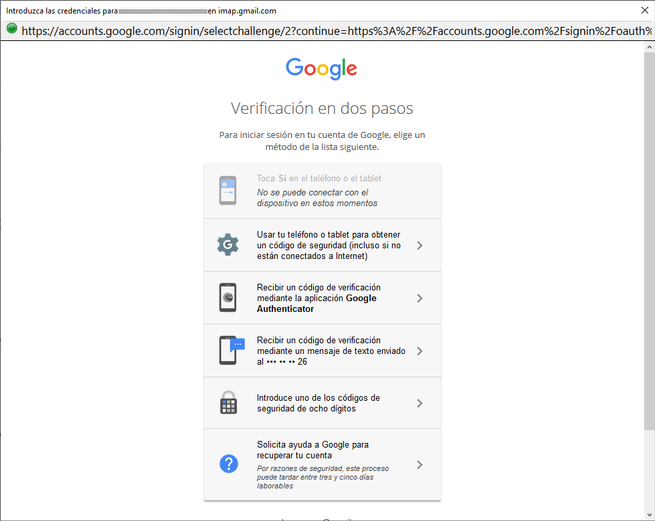
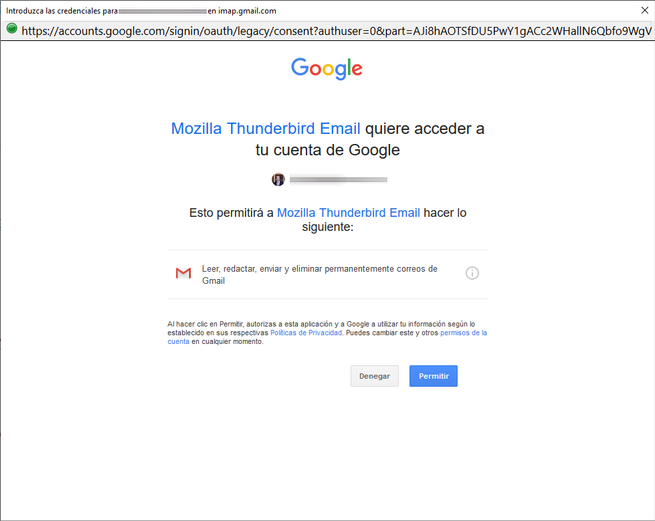
In our case, we have configured a Gmail email account, to be able to register it, we put our name and surname, the Gmail account with its corresponding password and click on «Continue». Thunderbird will automatically detect Gmail’s IMAP and SMTP, and it will launch the browser for web authentication and give Gmail permissions so that Thunderbird can manage email. If you have two-step authentication it will work without problems, some mail clients do not allow the use of two-step authentication because it is not supported.
Once we have configured the mail, we can see in the inbox, drafts, sent emails, spam and all of our email account. As you can see, the authentication and configuration of Gmail in Thunderbird is correct and works perfectly, now we can try to send a normal email to verify that everything is working correctly.
Once we make sure that the configuration is correct, we will create the keys with OpenPGP and exchange them with the receiver, in order to send fully encrypted and authenticated emails with security.
OpenPGP Configuration: Key Creation and Exchange
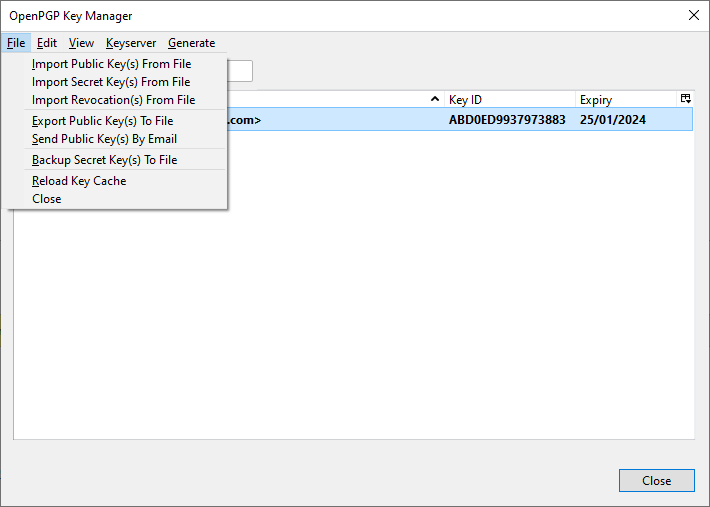
The first thing we have to do to be able to send emails encrypted with OpenPGP, or to receive them, is to create the public / private key pair. To do this, we go to the ” Tools / OpenPGP Key Manager ” section. In this section we have to go to the “Generate” option to generate new OpenPGP keys. If you already have your PGP keys, you can import them by clicking on “File”.
In this generate section, we can create the keys for one or more identities (email addresses). The normal thing is that these keys expire after 3 years, but we can configure more time less time. Regarding the encryption algorithm used, we can choose between RSA (3072 bits or 3096 bits) and ECC, depending on which one we want to use, we will choose one or the other.
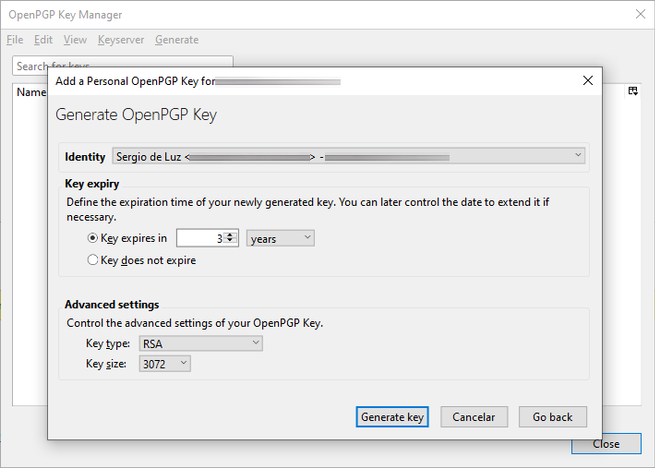
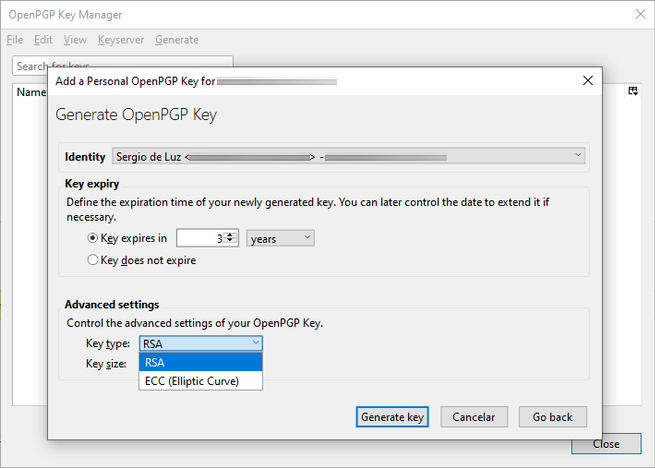
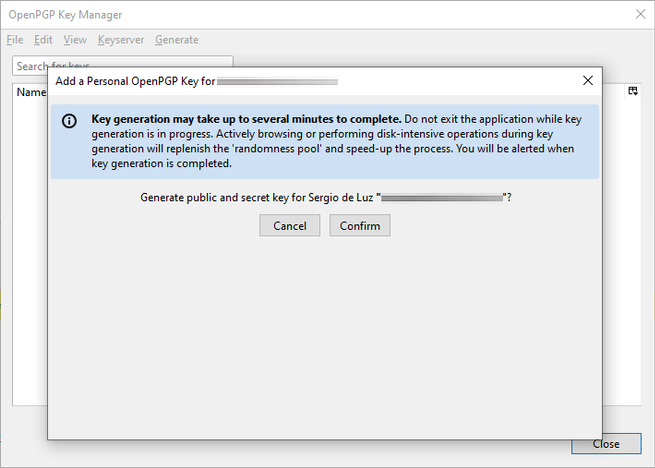
Once we have decided, we click on «Generate key» and we will get a message indicating that it may take a few minutes to create the cryptographic keys, depending on the PC we have it may take more or less time.
Once you have created them, it will appear in the “OpenPGP Key manager” list, indicating the Key ID and also the expiration date. If we right-click on the key, we can copy the public key to the clipboard, export the keys to a file, send the public key by email (which we will later do), revoke the keys, delete them and see all the properties of the key.
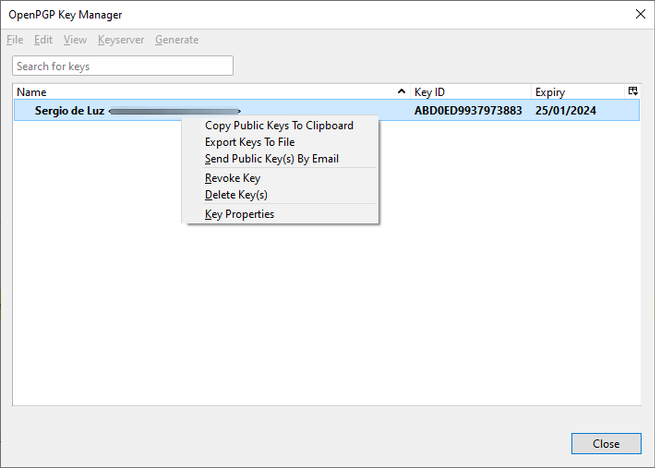
If we click on the “Send public Key by email” option, Thunderbird will automatically create a new email and attach the public key with an .asc extension, as you can see in the following screenshot. This email must be sent unencrypted, since we do not currently have the recipient’s public key, so we will not be able to encrypt it.
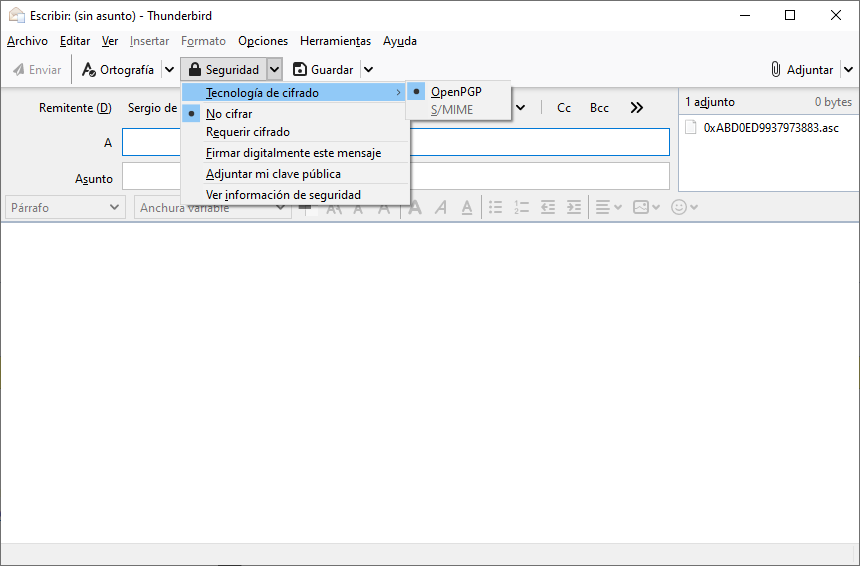
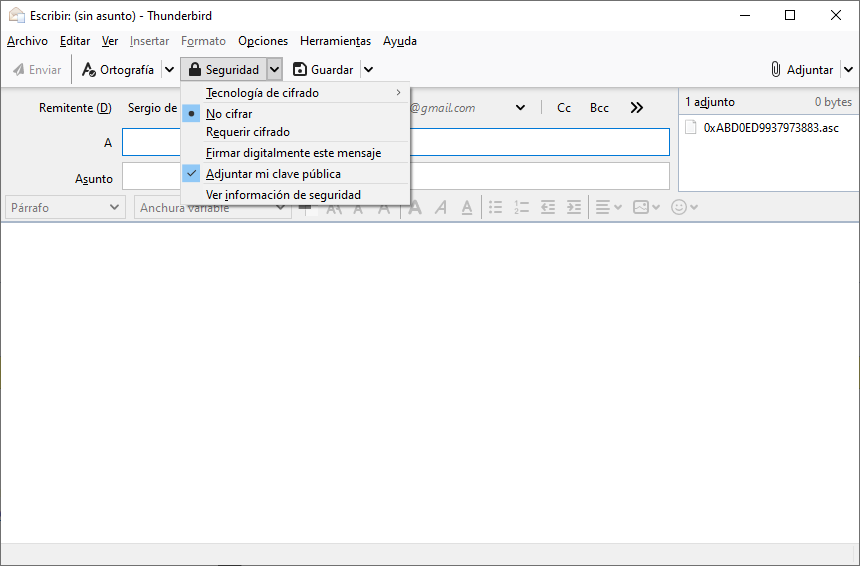
We can also do the same option if we write a new email and click on the ” Security / Attach my public key ” section, when you send the email, the key will be attached automatically and without the need to do anything else on our part, since will take the public key of the email sender.
At the moment we only have our own key, in order to send emails to others we must receive their public keys, and then import them into the OpenPGP Manager, this is very simple, we will simply have to go to ” Tools / OpenPGP Key Manager ” and click on the first option: Import public key from file . When we receive an email with the public key attached, Thunderbird will automatically detect it and we will have a button that says “import” and it will do everything automatically. If we have a folder with many public keys because we have used OpenPGP before, then we can import them all at once from this important menu.
To send an encrypted email, we will simply have to compose a new email, click on the ” Security ” section and choose ” Require encryption “. It is also highly recommended to choose the option ” Digitally sign this message ” so that the recipient can check our identity with the public key that he has. Finally, it is also recommended to add our public key again, in case the recipient does not have that public key.
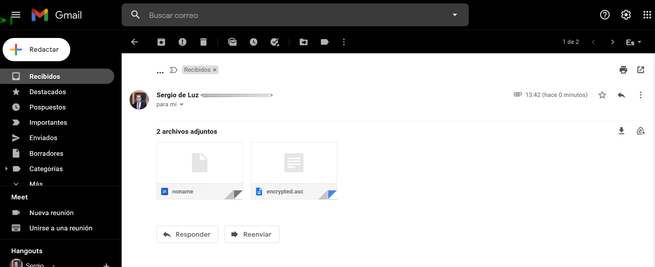
For example, we have sent an email to ourselves, and only we can decrypt it. If we access Gmail we can see that all the content is encrypted, and therefore, Google not even we (without decrypting it) can read absolutely nothing.
If we open this same email through Thunderbird, we can see it perfectly since it will be decrypted:
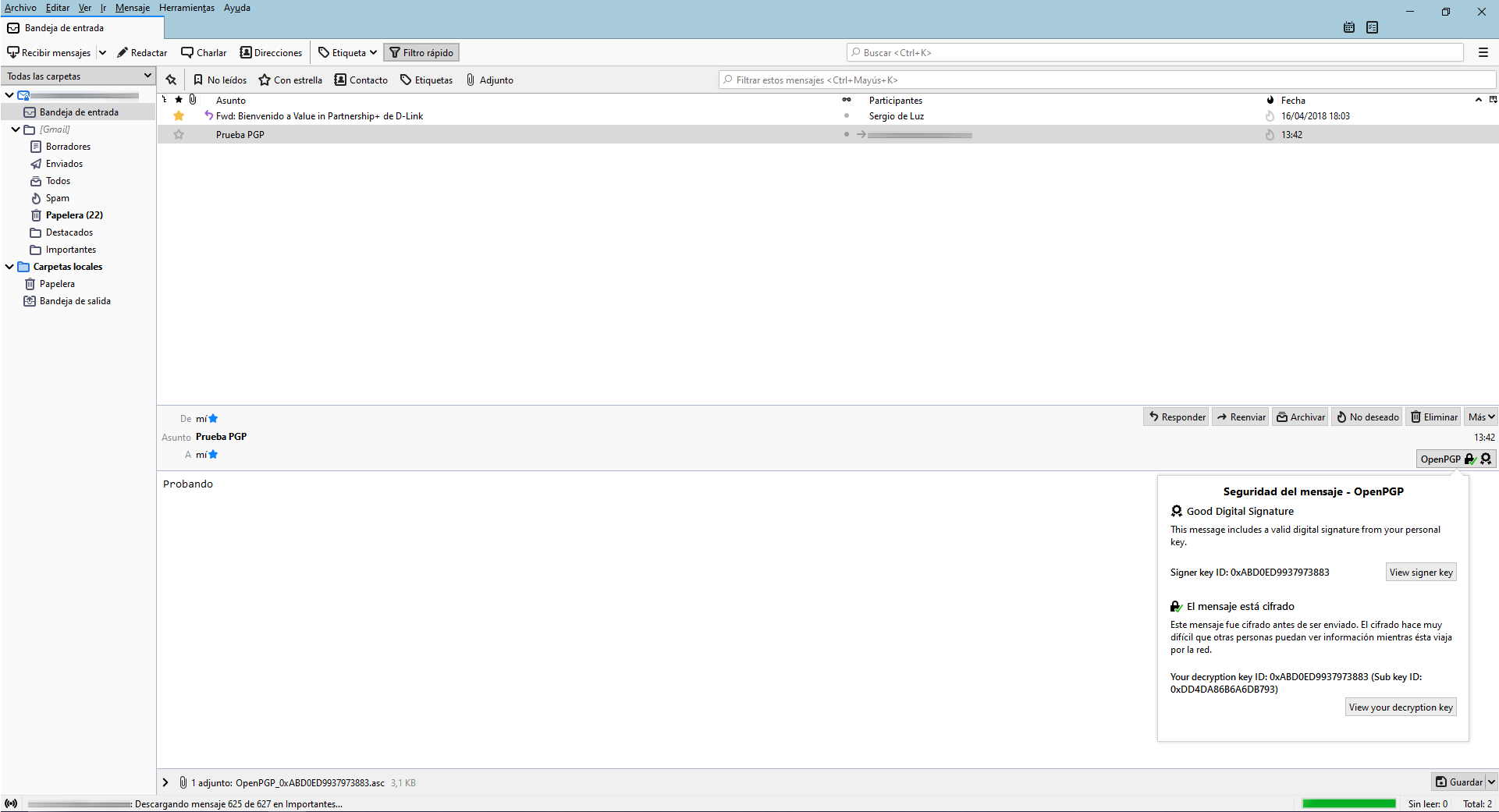
At the bottom right we can see that the digital signature is correct and the message is encrypted before being sent, if we click on “View signer key” or “View your description Key” we can see all the information of the public / private key that we just created.
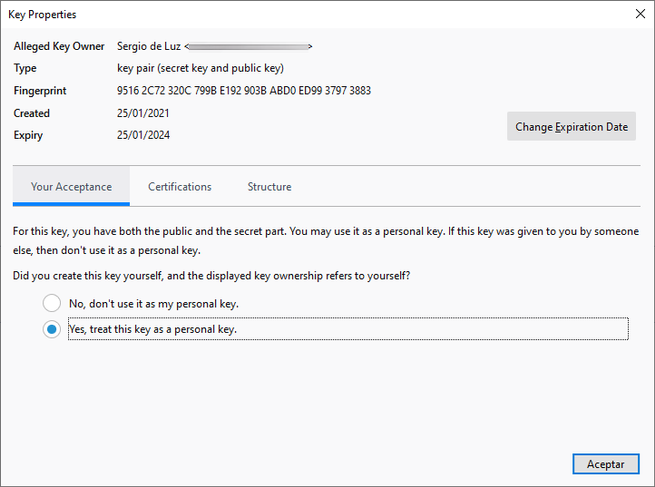
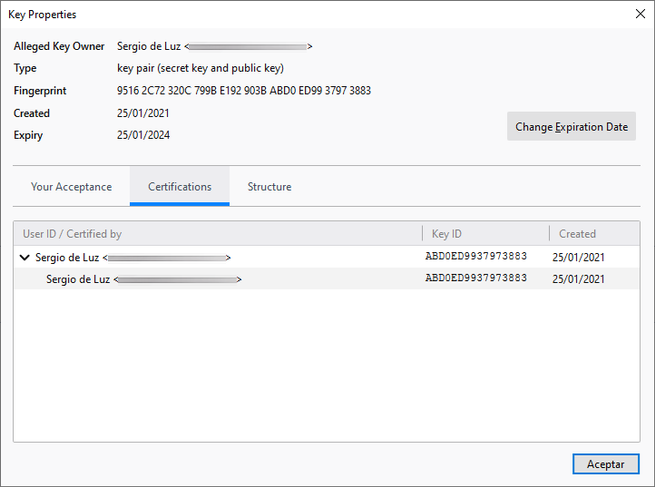
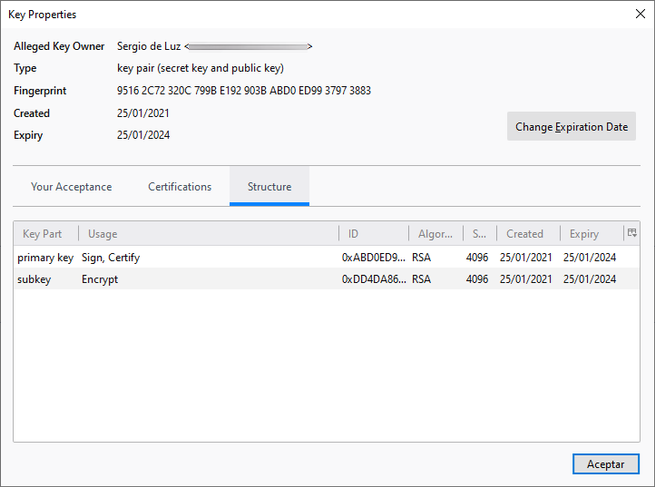
As you have seen, it is really easy and fast to send encrypted and digitally signed messages with OpenPGP in Thunderbird, it is no longer necessary to install plugins and create cryptographic keys in an external program, everything can be done perfectly in the same OpenPGP Key menu Manager. Remember that, in order to send the encrypted emails to a specific recipient, it is necessary to encrypt them with the recipient’s public key, if we do not have this public key, the information will not be encrypted, but we can sign it digitally.
We hope that with this tutorial you can send emails safely and privately using Thunderbird and integrated OpenPGP.
