Without fear of error, we can say that we spend more time with our mobile than with our family or friends. Android is the most popular operating system, present on a wide variety of mobile phones from manufacturers from various countries. We use applications of all kinds, whether for work or personal purposes.
The Google operating system has several functionalities that allow our mobile to be more secure. Below, we share with you the best tips to make Android as safe as possible, in addition, they are very easy to configure so any of us can do it.

Review the security of the associated Google account
Security review
In a matter of seconds, you can carry out a brief, but precise, review of the security of your mobile. It consists of three essential sections: the authorized Android devices you use, recent activity that is relevant to the security of the device, and the login and recovery options. It is recommended to carry out this review whenever possible, and it can even be easily done through the official Google website, it is not necessary to do it from the Android smartphone.
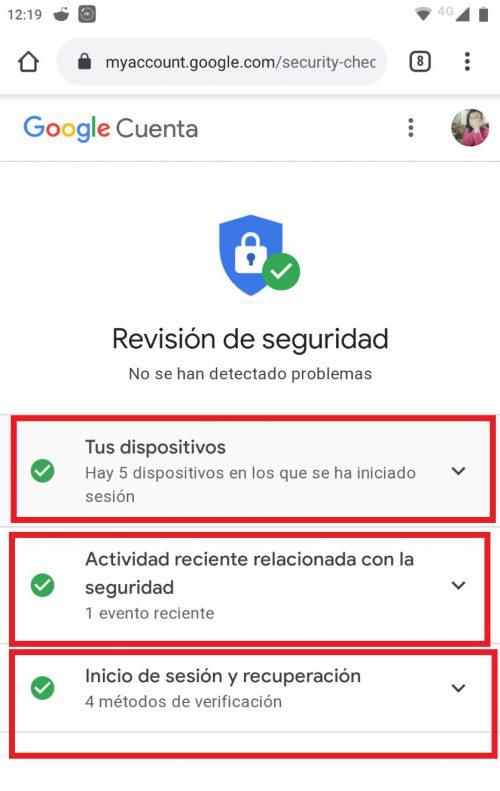
On devices , you can see which are those who are logged in to your Google account. You will have basic information such as what device it is and the operating system it uses. Therefore, you can review any recent activity related to account security. So if you have recently logged in to your old devices or a new one, it will appear there. It is essential that you delete the devices that you are no longer using, in order to minimize the access to your account if this device is used again.
Finally, in Login and recovery , you can take a look at all the recovery options of your account in the event that it is violated by situations such as login attempts or if you have detected a login that you don’t recognize.
Any activity that can be considered irregular can be detected through this review. If there is nothing to worry about, the check will appear in green. The yellow icon is if there is any potential suspicious activity and the red, then, would imply already dangerous activities that would compromise your account.
Google account activity control
One of the considerations that many Android users do not take into account is that they can have control over what they share with Google, specifically over the activity of the Google account itself. Let us remember that thanks to a single account we can access several of the services we use on a daily basis such as the search engine and YouTube.
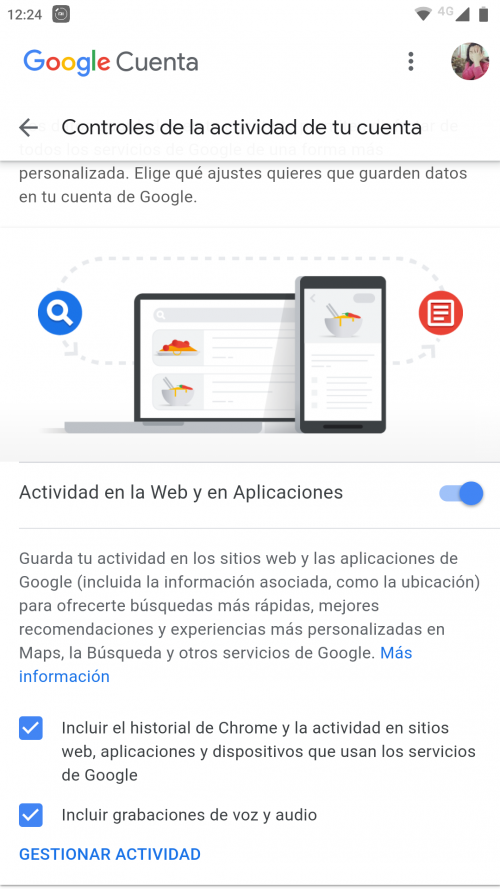
This activity control can take a little more than 15 to 20 minutes and can be accessed from the web. It may seem like a long time, but it is useful and necessary that you can limit everything you share to Google. What risks could exist? Remember that you have the right, and at the same time the obligation, to preserve the privacy of your account activity. Also, by default, with Google you share absolutely everything . Accordingly, adjust your experience of using service applications to make them even more personalized.
The screenshot we see above shows us the activity section on the web, in it we can activate or deactivate options such as inclusion of the history of Chrome so that it is used by organizations that use Google services. In Manage Activity , there are even more options that you can activate or deactivate.
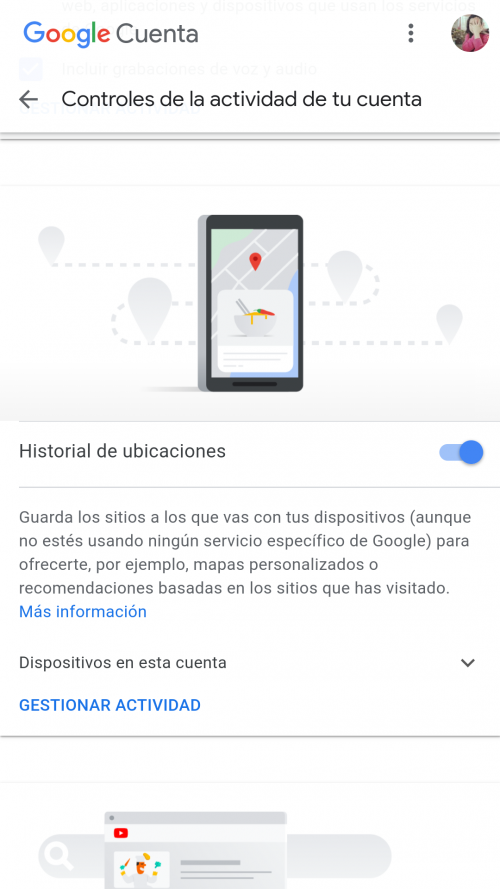
The way of managing this control is practically the same in all the sections. Below, we see the section on Location History where you can manage how your location information is used among the different Google’s own services, such as those of third parties.
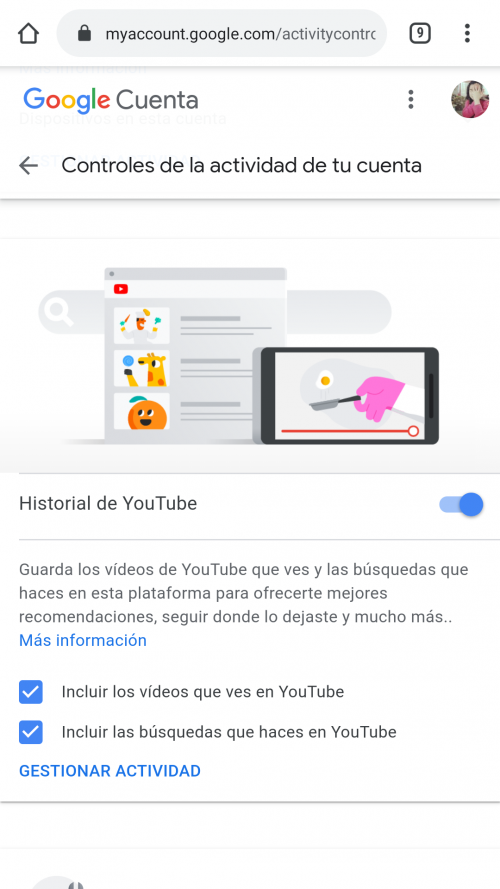
The following corresponds to the management of information regarding your activity on YouTube .
Finally, you get to the ad management section. The latter is very important since here you can regulate what you share with Google so that the information of your activity is not manipulated in order to offer you advertising aimed at your preferences for consumption or use of products and services.
Set up emergency contacts
Chances are, you don’t need them at all times. However, you should carry out preventive activities, especially if it concerns your own safety. You can set up an emergency contact, which can be anyone you trust . Once you have configured it, it will be possible to contact you in a few steps in case of any eventuality from the lock screen.
The emergency contact can be very useful, for example, if you ever lose your mobile. If someone outside you finds it, you can contact the emergency contact to notify them that you have the lost mobile, all without having to unlock the screen. To make it even easier, you can add a message that appears on the locked screen and says to notify the emergency contact.
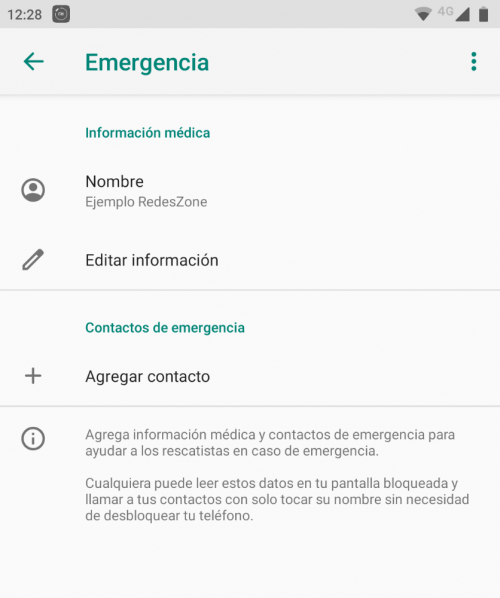
When creating the contact, be sure to indicate the most important data, especially the mobile number. In this way, anyone who finds a foreign device can increase the chances of contacting the owner and returning it to them. On the other hand, emergency contact also helps you communicate with someone much more quickly in a risky situation.
Limit the content of the locked screen
Nowadays, notifications provide us with multiple facilities. One of them is to see much of the content of one or more messages without having to open the notification at the time. However, the information you display is likely to be personal, professional, or simply sensitive information in general.
Let there be no doubt that there are still people who can take advantage of this, and be able to collect information about you, with the aim of being able to attack both your physical security, and the security of your data that is on the network or your devices. These people could be near you in a cafe, supermarket or anywhere else. Consequently, we recommend that you limit what can be displayed in notifications if the screen is locked.
You must go to Settings> Security and Location> Locked Screen Preferences
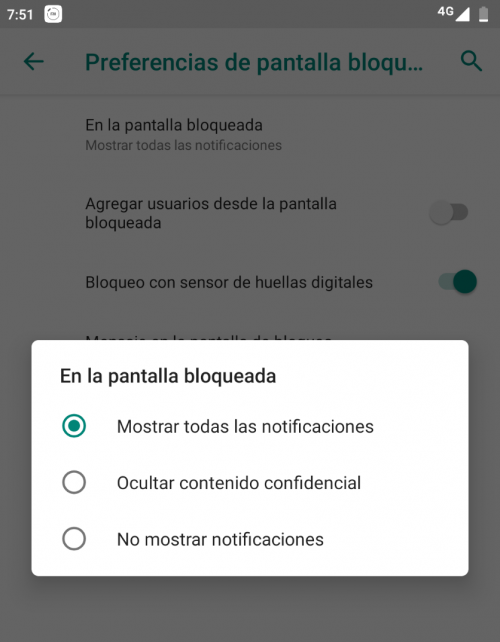
As we see above, there are three options: show all notifications and their content. The second is to hide confidential content (it will show that there is a notification, but not its content) and, lastly, the option that does not show any notification. This last option would be the most recommended, especially if you deal with many people daily, or if your device is used to being in a place where there are, precisely, many people who can see the screen
Manage app permissions
When we download applications from the Play Store , in many cases a pop-up window appears detailing the permissions that will be required for them to work. Some of the common permissions are the camera, contacts, device storage, microphone and others. However, many applications request permissions that are not strictly necessary for their function. Remember that the more permissions we grant to applications, the more at risk we put the privacy of our data.
In Settings, we are going to look for the App Permissions section, in which we will have a view of all the permissions that our mobile can grant.

For more simplified management, app permissions are managed by the permissions themselves. As we see in the screenshot below, each permission groups all the applications that use it, or that could have that permission.
Example: the Storage permission has 82 applications that could have permission to access it. However, you have only authorized 32 applications.
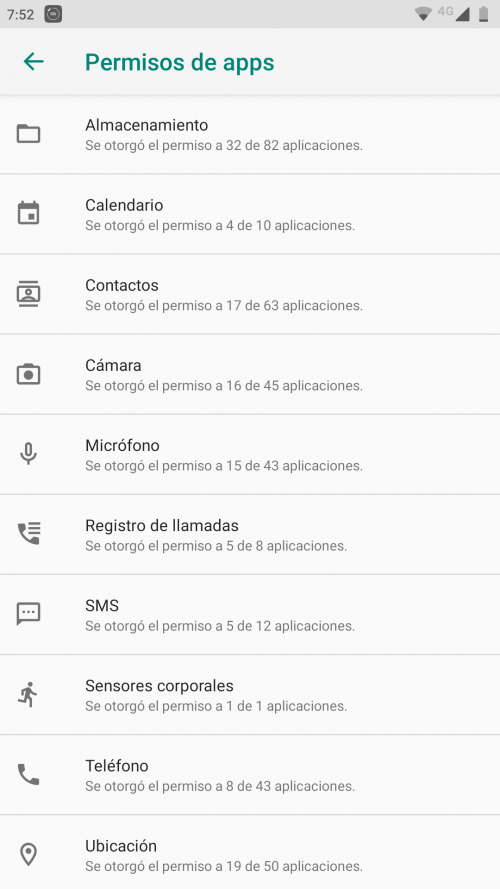
Then you must enter each permission and you will see the details of the applications. Next to each one, there is a toggle that will allow you to enable or disable the permission.

You must keep in mind that, in addition to protecting the security and privacy of your data. Not granting so many permissions to the applications also implies great battery savings .
The location of the device is one of the permissions that is requested by multiple applications such as Maps , Facebook , Instagram and many more. Since the default location service has some battery consumption, it is better to grant permission to the applications that are really necessary.
Set up Google Smart Lock
This is a functionality that allows you to reduce the occasions when you must unlock your device. As listed in the description below, allow you to keep it unlocked in situations that you consider to be completely safe.
To take advantage of Smart Lock safely, we will discuss what each option consists of. Thus, you will choose the safest option . Since using all the options or some that might not be convenient, you would expose your mobile unnecessarily.
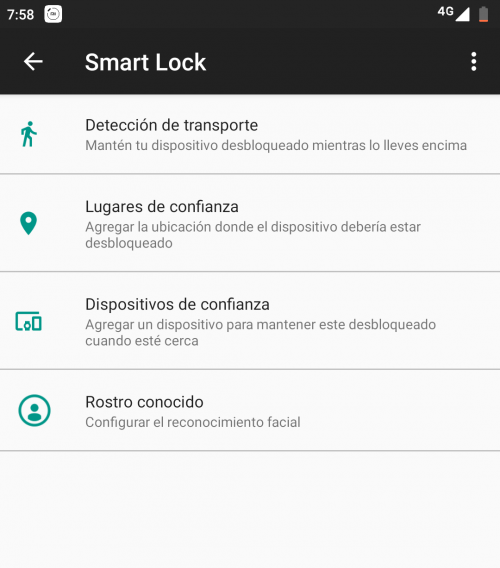
- Transport detection: the mobile will be unlocked only when you have it at hand. This can be convenient if you spend a good part of your time with your mobile in trusted locations such as the office or home.
- Trusted places: Your device will not require unlocking if you are in certain places. Automatically, Android notifies you with the suggestion to use Smart Lock with this modality if you spend a lot of time in one place. Like your home, office, relative’s house, etc.
To configure it manually, you must select the Trusted Places option and in a few steps you can add your current location or whatever you consider.
- Trusted devices: today, connect your mobile via Bluetooth to devices such as hands-free or speakers in our home. You can configure so that certain devices with which you connect frequently, can be trusted. Thus, the mobile will remain disconnected while you are connected by Bluetooth with these devices.
- Known Face – Allows you to configure facial recognition so you can unlock the device. It is the most widely known system: if the face is not recognized, it goes by the following unlock method (PIN, password, etc.).
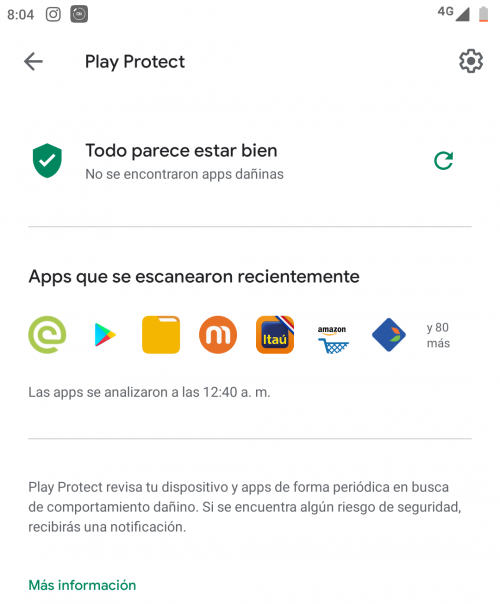
Manage Google Play Protect
It is a functionality included in the Google Play services of Android. Specifically, for the Play Store . Whenever we download an application from that store, we should see a green shield icon like the one shown in the screenshot below. This means that we have the data that the application that we are going to download is safe.
On the other hand, Play Protect makes a daily scan of the applications that are already installed on your mobile in order to detect some type of vulnerability or suspicious activity. However, you can perform this scan manually either from Settings or the Play Store itself.
Enable and manage Find my Device
It is almost impossible to avoid the fact that at some point we can lose our mobile or that we are victims of theft or theft. Therefore, Android has the functionality of ” Find my Device “. It is highly recommended to have this activated to avoid any kind of setback. Now, let’s see the two options to access the functionality: web and application .
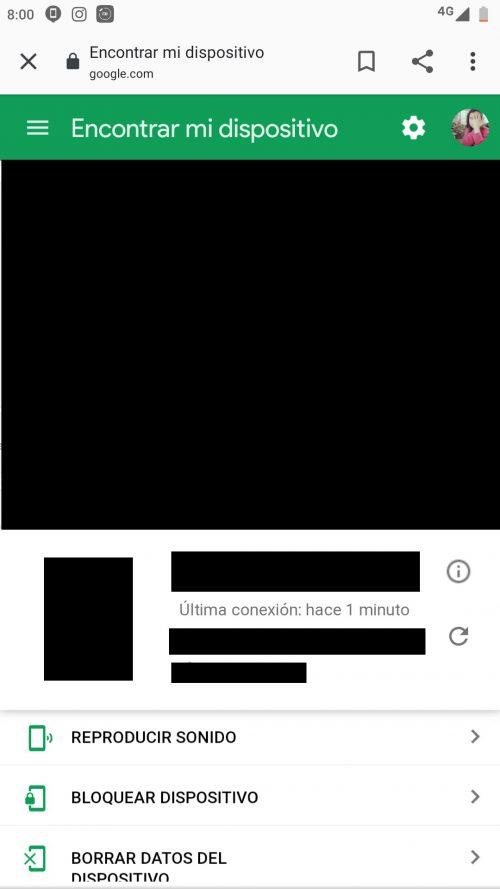
Google “Find My Device” and you will be taken to a page like this that will display your device’s current location information. It will show you what is the brand and model, how many minutes or hours was the last connection, the battery percentage and more. In the event that you cannot find your device, or if it was stolen or stolen, you can access this page.
If found, you can choose the options to play sound , if for example you lost it somewhere in the house. You can also lock the device so that it cannot be used by anyone. Finally, you can erase the data on the device so that it is not manipulated by the person who can count on your mobile.
If you prefer, you can download the Find My Device application from the Play Store at no cost. The interface and features are practically identical.

We are sure that with these security measures, you can use your Android mobile with more tranquility, security and privacy. As we have discussed, it will not take too long and the few minutes you have invested will make a difference. The Android system, over the years, has reinforced its security features to make it much more robust against potential cyberattacks.
Some features are not fully disseminated, so at the time you prefer, we suggest “take a journey” through the world of your mobile settings. You can find many more features apart from those mentioned, so you can customize and ensure a great Android experience.