Today, any type of network demands greater controls and implementations of security measures. From the most elementary to the most elaborate according to the case. This time, we will talk about the popular Wireshark tool and the SSH protocol . The latter is one of the protagonists of traffic on those networks that support remote access to other machines, ensuring the encryption of all traffic generated in them. We will show you how to prevent this traffic encryption protocol from becoming a big problem for your network.
What is the SSH protocol?
The acronym for SSH responds to Secure Shell. It is designed to allow remote access in a confidential and authenticated way to a computer. It has similarities in relation to its predecessor, Telnet, which allows a user to access that computer or machine remotely via the command line. However, the most important thing that distinguishes SSH from Telnet is that all session traffic is 100% encrypted.

The use of the SSH protocol is highly recommended in case of need for communication with other computers, switches, routers, servers or any host. It has the assigned port number 22 TCP, although it could be changed to any port on the SSH server.
Some of the most popular applications that implement this protocol are PuTTY and WinSCP . Both are compatible with the Windows operating system. On the other hand, there is OpenSSH that is available for OpenBSD, Linux, Solaris, FreeBSD, AIX and others.
Wireshark: the network analysis guru
It is one of the most popular and recommended network protocol analysis applications. It allows you to have complete control over what happens on the network to which you are connected at a very detailed level. It can be used in both the private and corporate environment. Even the various educational institutions and the government can take advantage of this tool that has no cost.
It is a solution that exists since 1998 and thanks to the contribution of experts around the world, it is still in force and available to anyone who wishes to use it. It is characterized by being very practical when carrying out analyzes about what is happening in our network and what security policies or measures to apply for safer performance.
What can you do with Wireshark? According to its documentation on the official site, we cite some of the activities you can carry out. In case you have doubts, you can check your own site which has documentation and support:
- Deep protocol inspection
- Information capture at the time for further analysis
- VoIP analysis
- Possibility of reading and modifying information capture files such as tcpdump, Microsoft Network Monitor, NetScreen snoop and more.
- Access to live viewing of information from the protocols of Ethernet, Bluetooth, USB, IEEE 802-11 (Wi-Fi), Frame Relay etc.
- Export of information to XML, PostScript, CSV and plain text formats.
One of the most interesting and important uses for which you can use Wireshark is for the incident response related to SSH traffic . Recall that this is a very powerful protocol especially for the encryption with which it has by default. You can have remote access and of course it is encrypted to any device that has the SSH server function enabled.
You can perform Credential-Stuffing attacks, scanning machines that are running on vulnerable SSH servers and setting up reverse shells . We will emphasize the first two below.
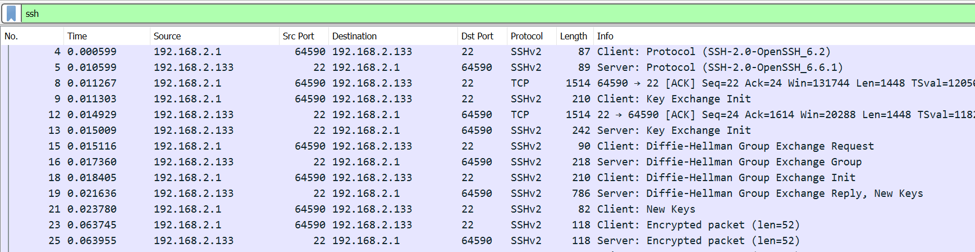
Credential-Stuffing attacks
Considering that SSH requires user authentication, an attacker who has access to a machine running an SSH server can carry out attacks of this type without major problems. But what about the passwords of the different credentials? Unfortunately, most people tend to use passwords that are very easy to guess or worse, always opt for the same password for all their accounts. This makes the credential stuffing attacks happen, in most cases, completely unnoticed.
From good to first it is not easy to differentiate the attempts of access via SSH successful from the unsuccessful ones in Wireshark. However, there are some features that will help us reveal which records are successful:
- Flow length (of the session): if it were a successful SSH session, it will be longer than a failed one.
- Package size: SSH servers have established responses for successful or failed authentication. It is possible to observe the size of the SSH packets and infer that the larger ones constitute successful sessions.
- Package time: Those packages that require user interaction, if authentication was successful, will have more time than those that are automated. The latter refers to packets with shorter life time due to failed authentications.
In addition, we recommend you check the number of login attempts, if you see an irregular number it is because there is a possibility of having been victims of a Credential-Stuffing attack.
Remote access scans
One of the biggest drawbacks and risks generated by the rise of emerging technologies such as the Internet of Things is that enabled devices have SSH enabled in the first instance. Normally, their associated systems usually use credentials by default or with some minimal modification. Why is this a risk? Anyone who has knowledge about those passwords or the ability to guess users and passwords can easily access the machines remotely.
That’s right, even SSH can count on its particular security holes. However, it is possible to have control of these machines that act as insecure SSH servers. Knowing that legitimate SSH requests and traffic should originate from the internal network itself. Therefore, they are reliable IP addresses.
Filtering Wireshark requests and internal SSH traffic, in addition to that coming from external IP addresses, will help identify suspicious situations. It can be understood that, in most cases, SSH traffic from unknown IP addresses to our internal network can signal that the network has been compromised.
The latter does not mean precisely that everything that may come from outside the network is suspicious or dangerous. Once an attacker gets remote access to a machine, SSH becomes an ideal ally to carry out other types of attacks and quickly expand to other machines, performing more than one attack at a time if desired. How is it possible to detect this? With Wireshark, by analyzing all SSH traffic, you can set both usual and unusual access patterns. An unusual pattern case may be that there is evidence of a high level of traffic from a single machine. Another case of an unusual pattern may be that a machine makes requests to other systems that it normally would not.
Both at the level of your local network and a corporate network, SSH can become a great ally and in turn, a great enemy. What results in very close monitoring and special control if we are responsible for managing a corporate network. Controlling and even blocking SSH traffic on the network turns out to be a good idea, as well as communications and general traffic that occurs within the network must be monitored for any abnormality.
We recommend you read our complete tutorial on how to configure an SSH server with maximum security.