At the time, the functionality of unlocking our mobile with the fingerprint was extremely innovative, especially for how practical it is. We not only use the footprint to unlock devices, but also to unlock applications, especially financial services, banking and payment services applications, they use this functionality to increase the security (and the ease of authenticating ourselves) of the transactions that are made. However, are they really as safe as they promise?
Let’s do a little history first. We have to go back to the first years of the 2000s. Despite the fact that the first mobiles were launched in the last century, more than ever at that time they were a novelty. It is valid to affirm that PDAs (Personal Digital Assistant) are the forerunners of smartphones, better known as smartphones . The golden age of PDAs was precisely in those 2000s. The HP iPAQ 5455 is known for being the first mobile phone with the functionality of unlocking with a fingerprint using the biometric sensor. Likewise, it was the first laptop-type device (Pocket PC) to have Bluetooth and Wi-Fi connectivity. However, it wasn’t until the year the iPhone 5S was released that fingerprint unlocking became quite popular.

Strengths and weaknesses of biometric authentication
Authentication through biometrics allows us to authenticate ourselves against systems or applications with the “something that we are”, that is, a part of our body. For example, biometrics can be our eyes, the iris of the eye, fingerprint, voice, facial features, and even handwritten signature and hand geometry. Over time, the hardware needed for biometrics is cheaper, but still quite expensive, cheap and reliable biometric methods are necessary. A reliable biometric authentication should fulfill some characteristics:
- Universal: anyone can use it.
- Differentiator: 100% certainty that we are who we say we are, that it has no false positives or false negatives.
- Permanent: that the traits that are measured do not change over time, for example, our fingerprint may change over time if our work consists of construction issues.
- Accessible: easy to collect the required data, not having to “train” the biometric software too much.
- Biometric errors: Fraud rate vs. insult rate, this aspect is essential to have a good biometric system. The fraud rate is false positives, that is, someone who impersonates us authenticates in the system, and automatically “passes” as legitimate. The insult rate is the opposite, we try to authenticate ourselves in the system, and it indicates that we are not who we say we are.
One of the safest combinations is to enter a system through a combination of “something we are”, “something we know” and “something we have”. The “something we are” means using biometrics, the “something we know” are the typical passwords we use in most services, and the “something we have” can be identification cards, or our smartphone to authenticate us with a TOTP code. If we use only one of the methods, the system is not entirely safe, it is always recommended to have at least a combination of two (two-factor authentication).

How the unlock of the mobile works with the fingerprint
We must always keep in mind that this is part of the use cases of biometric sensors. Basically, there are three types: optical, capacitive, and ultrasound. If we are citing each of them in order, we will notice that they were progressively improving in terms of security, having less fraud rate and less insult rate, in this way, we will have neither false positives nor false negatives.
Optical sensors
This type of sensor manages to generate an image of our fingerprint thanks to a glass surface that is illuminated by an LED diode. Through this illuminated glass, and within its possibilities, it generates that image of our fingerprint that allows us to lock and unlock both devices and applications.
What does not favor this technique, which is already out of date and is known to be insecure, is that it is extremely susceptible to moisture, dirt and any detail that could make it difficult to generate the print. Also, that makes the process of locking and unlocking difficult. Another factor against it is that it cannot be used correctly by older people. The reason is that the skin is not elastic enough, this even allows false recognition when it comes to locking and / or unlocking.
One of the reasons why this type of sensor is not safe is that it is easy to trick the fingerprint sensor. For example, with photographs of the footprint. Remember that this sensor only creates an image of our footprint, so it is relatively easy to violate it.
Capacitive sensors
They use multiple capacitors that store energy according to the shape of the footprint. Remember that no footprint is equal to the other, not at all. What do these capacitors do? They are responsible for forming a fingerprint with the highest possible level of detail. This type of sensor is popular on multiple smartphones. In particular, I use a Motorola brand smartphone that has this type of sensor. I can register one or multiple fingerprints to lock and unlock the mobile. When registering one, instructions appear on the screen that tell me to put my finger down until the representative image of the fingerprint is completely colored.
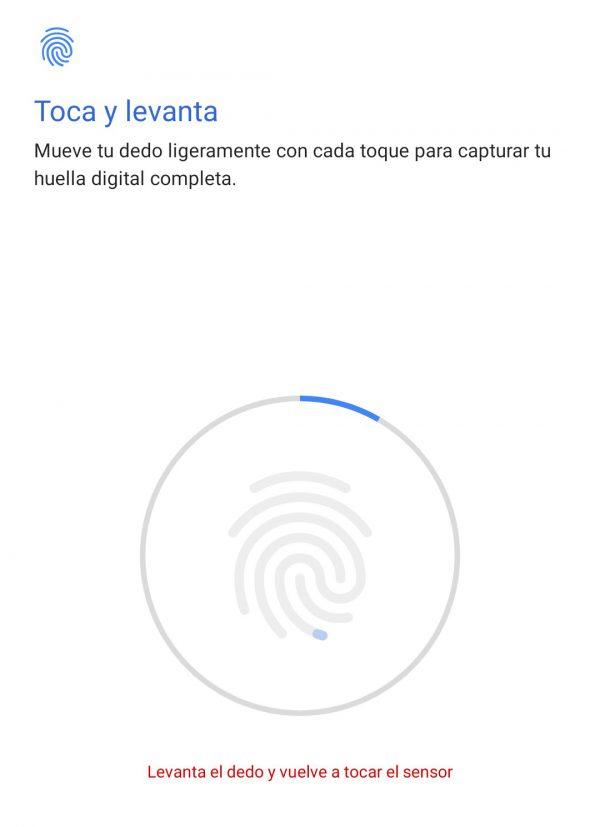
What does this mean? I put my finger down once, a group of capacitors manages to collect and store energy charge to form the fingerprint. I put my finger again, another group of capacitors does the same. And so on, until the process of creating the footprint is completed. There are many capacitors that start when we generate our footprints.
Fortunately, the capacitive sensor is quite reliable and safe , however, this can represent quite a considerable extra cost. At the time, the smartphones that were launched on the market with this functionality, were presented with a much higher cost than those that did not have it. Of course, a few years ago, this was not available on too many devices. Today, it is practically mandatory that our smartphone has a fingerprint sensor.
Optical sensors
These are already more modern sensors and with an extra layer of security. They consist of a sender and a receiver. Let’s see what each one does:
- Emitter: it sends ultrasounds outside, that is to say to the sensor where we will place our finger to create the fingerprint.
- Receiver: records ultrasound to create a three-dimensional fingerprint, which practically emulates each person’s own fingerprint.
Once the fingerprint is already created, it goes through an encryption process. Which leads to the generation of a key that secures the fingerprint and it participates in the authentication process. The latter refers to the moment when the user wants to unlock their mobile.
We can say that one of the advantages of this type of sensor is that it is possible to authenticate our fingerprint even if there is a minimum trace of cream or any other type of dirt. However, we must always keep in mind that hygiene is something mandatory in these times. It is necessary to keep both our hands and devices very clean so that we can avoid potential illnesses.
Mobile fingerprint sensors: even with various vulnerabilities
At first with the first smartphones with a fingerprint reader, they found serious security problems that will allow them to evade this type of authentication quickly and easily. In any biometric system, increasing security means that the insult rate is higher, and decreasing security means that the fraud rate is higher. Manufacturers must work hard and have optimal security, so that the fraud rate and insult rate is minimal.
There have been smartphones with ultrasonic fingerprint sensor, whose location under the screen, presented security problems because the fraud rate was too high. So much so, that some banks in the United Kingdom disabled authentication to their banking services if a certain model of smartphone is used. However, the other bank directly disabled the possibility of authenticating with the fingerprint. This vulnerability was evidenced when it was shown that it was possible to bypass the security mechanisms just by placing a screen protector and then put your finger on the reader. The result is that the device is unlocked, even if our fingerprint is not registered with the mobile.
Subsequent software updates fixed the issue. However, there is no doubt that 100% reliance on fingerprint lock / unlock is not recommended. What remains to be done in these cases? Complement the security of our smartphones and applications with complementary authentication methods such as Multi-Factor Authentication . If you use applications such as mobile banking, if it supports multi-factor authentication, you must configure it as soon as possible.