If you like the world of hacking, we are sure that you will have knowledge of the PenTesting technique (Penetration Testing) . Today in this article we are going to talk about essential tools and commands to start performing a PenTesting on local networks. In almost all cases, you will be able to obtain valuable information on the desired objective in just a few seconds. This guide is intended to serve as a «checklist», especially for those who are taking their first steps and, in passing, we recommend which programs to use.

Advanced IP Scanner
One of the most recommended ways to start finding targets is by running footprinting commands, which allow you to obtain a kind of “fingerprint” of that target to get more information about it. There are DNS footprinting type records that can help us obtain records that resolve the domain associated with our target:
- A – It is a record that serves to point the domain name to the IP address of the hosting server.
- MX – These records are used to detect activity of email exchanges.
- NS – They are used to identify the DNS servers where the domains are registered.
- SRV – These records help us distinguish the service hosted by specific servers.
- PTR – With the help of IP address, you can get the domain or domains associated with it.
- SOA – Consists of information related to the DNS server about its DNS zone and other DNS records.
- CNAME – Makes the domain name to another domain name.
Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting. It is free, compatible with Windows 10 and does not require complicated installation and use processes. Just run and go. It performs a complete scan of all devices connected to the network, gives you permission to manage them (example: remote power on / off) and even gives you an overview of all shared folders. You can access the program’s website and download it as soon as possible.
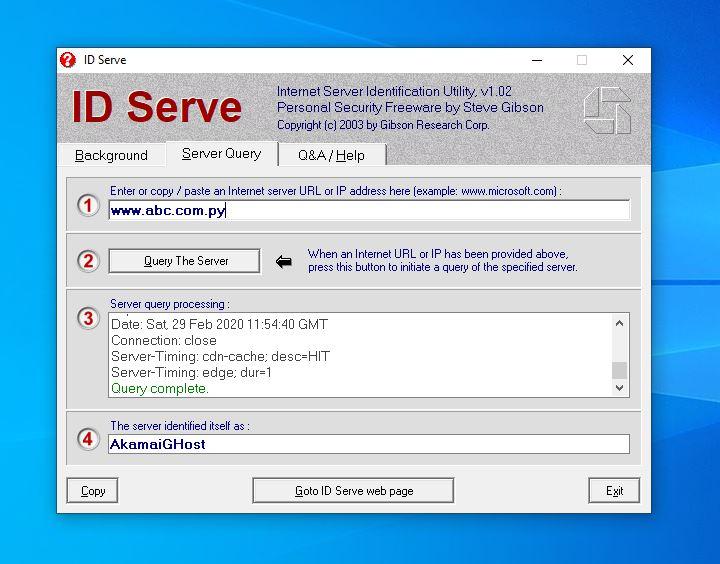
IDServe
With the “Banner Grabbing / OS Fingerprinting” step, it is possible to determine the target’s operating system. Once it is possible to obtain the information related to its version, for example, we are going to need to find the vulnerabilities to exploit them later. Thus, you can already try to gain control over the operating system. What tools would we need? It can be Telnet, NMap or IDServe.
Let’s talk about IDServe , which is one of the lightest we can find. It is free, compatible with Windows 10 and does not require further installation steps. It is a matter of downloading, running and using the program.
Nessus
The next step is the vulnerability scan, it allows to identify any type of hole within the operating system of the chosen target. Some of the tools that can support us with this step are: GIFLanguard, Nessus , Ratina CS and SAINT. With emphasis on Nessus , this tool allows us to obtain the following information:
- Data collection
- Host identification
- Port scanning
- Selection of extensions
- General data reporting
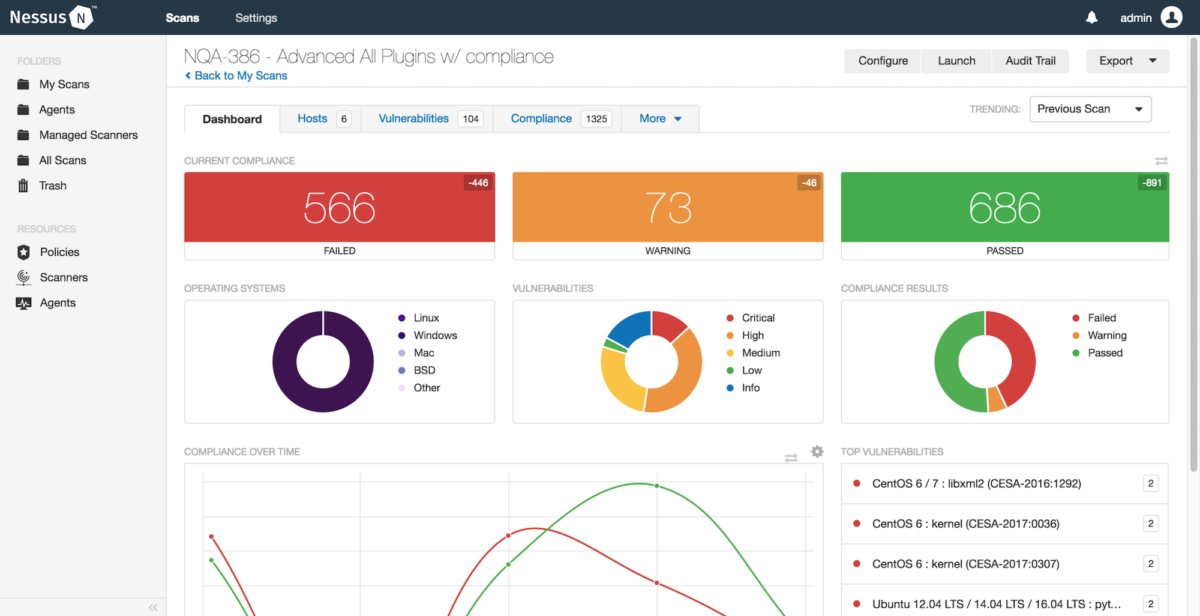
Using a dashboard like the one we see above, it is possible to have a complete overview of the vulnerabilities that would be affecting the services that are running on the network. Including the level of impact of each of them. In this way, we will be able to know how to take actions against these vulnerabilities.
LANState
On the one hand, the drawing of the network diagram allows you to have a logical overview of the network of the organization to which the chosen objective belongs. Likewise, this panorama displays information related to the logical connection routes to the target host on the network. Through LANState you can visualize the state of the network in a graphic map that is easy to understand, as well as quite detailed. For this to be possible, make scans of the network you are going to monitor, identify the hosts and verify the topology with which you are working.
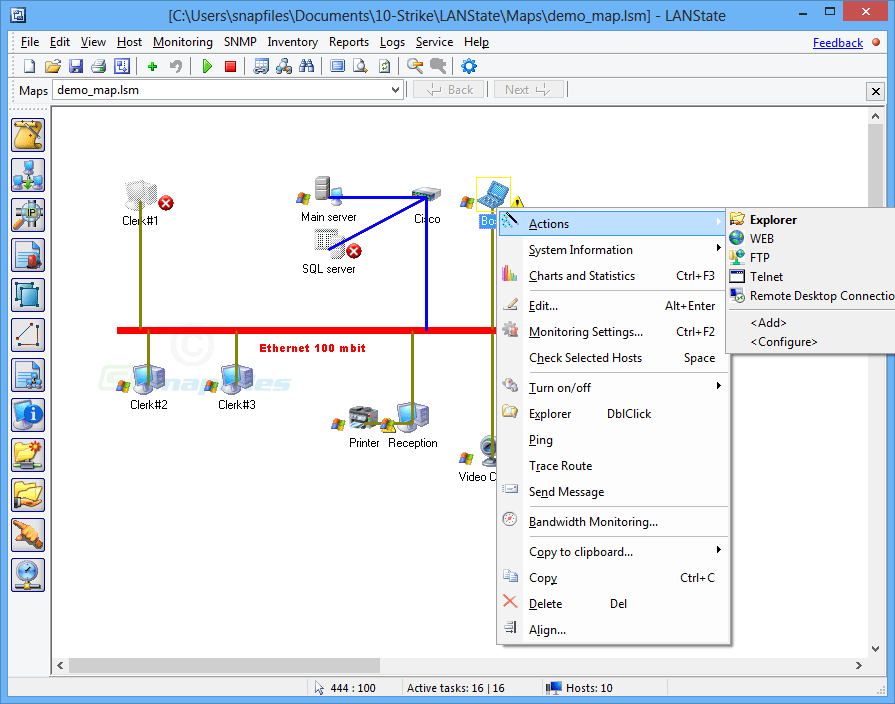
All the information will be available through a dashboard focused on monitoring the participating network devices: switches, routers, UPS, door sensors, and much more. Also check their voltage and temperature. Proactive and preventive actions can be configured through email, SMS, and even sound notifications. This, in order to make known about security flaws that occur within the network.
Access the download of this program, which has a 30-day trial period, then you must pay for the subscription. It is compatible with Windows.
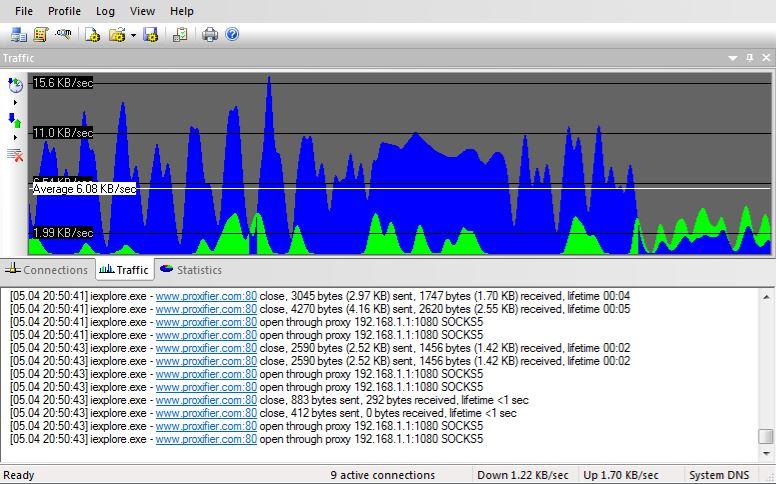
Proxifier
Now, we need to filter out unwanted content and most importantly, hide our location and any type of information that can identify us. Proxy servers serve this purpose.
Proxifier is one of the most complete solutions available for both Windows and MacOS. Redirect connections from any type of web application through a proxy server. Be it browser, email, databases, games and more. On the other hand, it controls access to network resources and routes all connections through a simple entry point. All this has the purpose of improving the quality of the Internet connection, should we need it. This, through faster and safer routes , because encrypted channels are used. It is one of the lightest and most speed-friendly alternatives.
You can download the application, which has a free 31-day trial, and then you should pay for the subscription according to the provider’s conditions.
Are you looking for free alternatives? In this article we have published a complete list of free VPNs , which do the same function as these proxies, but routing all network traffic. However, keep in mind that many of them have limitations in terms of the amount of traffic in MB / GB that you can generate or speed limitation. If the use you have is specific for this purpose, you will have no major problems in using it.
Documentation of what was found
The final and most important step is the documentation of the entire process. We recommend that you make a first document that consists of rules that must be signed by all parties involved in PenTesting. In addition to that, it details all the preliminary information regarding what is going to be done, established times, among other points. On the other hand, there is the document detailing the scope of the PenTesting. It specifies what to test, what not and other important considerations.