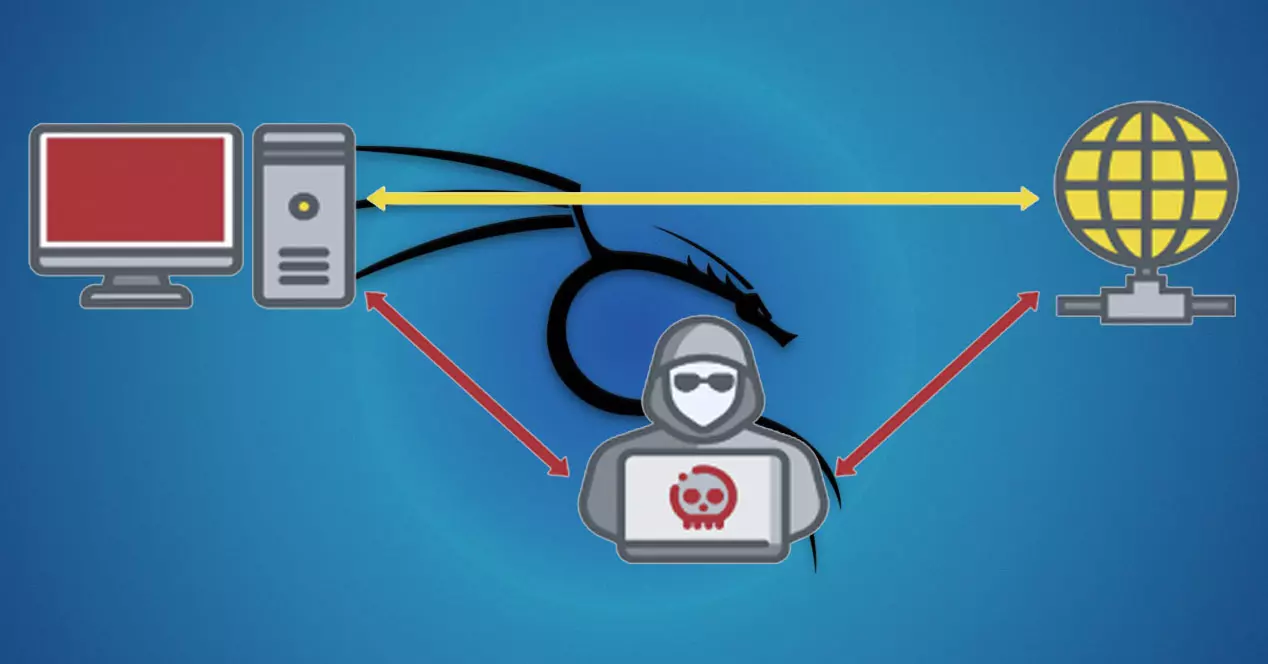
ARP Poisoning attacks or also known as ARP Spoofing, are one of the best known and most dangerous Man in the Middle attacks that we can find in wired and wireless networks. If a cybercriminal carries out this attack correctly, they will be able to intercept all communications between the victim and the Internet connection, in addition, with somewhat more advanced techniques, they could even modify traffic on the fly and even “lift” the security of the HTTPS protocol to make it HTTP and violate our security. Today in this article we are going to explain what an ARP Poisoning attack does, how it is done with the popular Kali Linux distribution and how we can protect ourselves from this network attack.
What is the ARP protocol?
The ARP (Address Resolution Protocol) protocol is one of the fundamental protocols in IPv4 networks, without this protocol we could not obtain an IP address by DHCP or communicate with other computers, even if we have put a private IP address on our computer. The ARP protocol allows network communications to reach their destination correctly, its objective is to translate IP addresses (logical addresses) into a MAC address (physical addresses) and vice versa. The ARP protocol is responsible for forming a table with the IP-MAC pair, and that the different computers on the local network can communicate with each other without problems, in addition, it also ensures that the computers can communicate with the router to access the Internet Since the router will also have a LAN IP address and a MAC address, where the different PCs and devices will send their frames to be managed by the router.
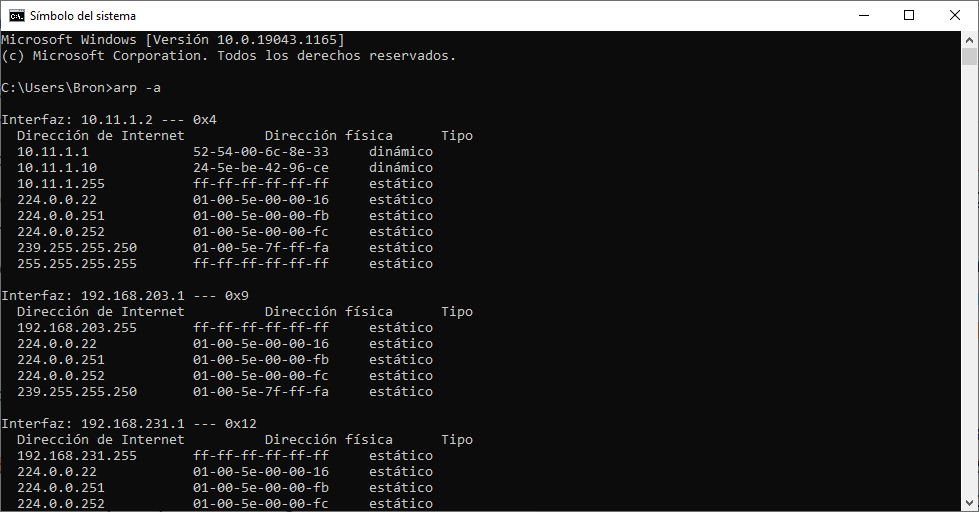
The ARP protocol only exists in IPv4 networks, in IPv6 networks this same work is carried out by ICMPv6, which incorporates more functions than in IPv4. We ourselves can see the ARP table of our computer to see all the computers on the local network with which there is currently communication, if we open a console and put the following command:
arp -a
In the following image you can see the private IP addresses (Internet addresses) and also the MAC addresses of all the devices (Physical Address). We can see all the ARP tables of the different network cards that we have, a very important detail is that we can remove or put IP-MAC pairs from this ARP table manually.
All computers keep this ARP table as a cache, so it will be temporarily renewed or as new computers appear with which we want to communicate, that is, it is a dynamic table and it changes depending on the communications that we are going to make. In this way, if a certain computer does not know the MAC of an IP address, it will have to send an ARP request packet, requesting the corresponding MAC address from other computers.
One of the most important entries in the ARP table is the one displayed by the router, usually the first IP address on the subnet. ARP Poisoning attacks are specifically focused on this entry, and now we will explain why. The ARP protocol was not designed with the aim of being secure, so it does not verify at any time that the response to an ARP request really comes from a legitimate host, anyone could impersonate another host easily and quickly, performing an ARP Poisoning attack.
What is the ARP Poisoning attack?
The ARP Poisoning attack consists of poisoning the ARP table of a victim, making it believe that the router is the attacker, with the aim that the victim forwards all its traffic to this attacker to perform a sniffing of each and every one of the connections that perform. In this way, a victim device could unknowingly send all its network traffic to this attacker, and carry out two different types of attacks:
- DoS attack : if the attacker does not forward the connections to the router to go to the Internet, we will be doing a denial of service to the victim, that is, we will be leaving him without an Internet connection.
- Man in the Middle attack : if the attacker forwards the connections to the router to go to the Internet, we will be doing a MitM attack, obtaining all its network traffic for further study, in addition, the information sent or received could also be modified on the fly the victim, in fact, one of the most dangerous attacks is SSL Stripping, whereby an attacker is able to “lift” HTTPS traffic and convert it to HTTP to spy on all communications. The attacker will be able to continue routing all communications and obtain all the information, which is the most normal thing, in fact, he will be able to steal the victim’s cookies and impersonate him without the need to steal user accounts and passwords.
In order to perform an ARP Poisoning attack , it is necessary to meet certain requirements:
- The attacker must be within the same network as the victim, same wired network or same WiFi network.
- You must scan the entire local network in search of the victim’s IP address, to later launch the attack.
- You must make use of different tools, in order to create a fake ARP packet and send it to the victim. Two well-known tools to carry out this task are Arpspoof and BetterCap, from the latter you have a complete tutorial in this article.
- Once the fake ARP packets are sent to the victim, they will believe that we are the router. But for the communication to be bidirectional it is also necessary to make the router believe that we are the victim, therefore, we will have to launch two ARP Poisoning attacks, one on the victim and the other on the router.
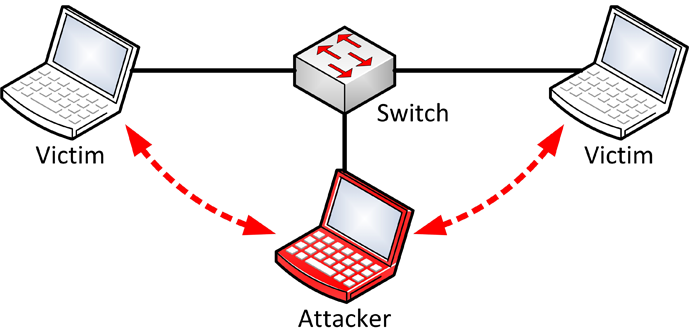
Once both the victim and the router have received the fake ARP packets, they will communicate with the attacker directly instead of with each other, and right now the attacker will be in the middle of the communication. Now the attacker
How to do an ARP Poisoning attack with Kali Linux
The first thing we must do, in the list of applications, is look for section « 9. Sniffing and Spoofing «, since that is where we will find the necessary tools to carry out this computer attack. Next, we will open « Ettercap-graphical » and we will see a window similar to the following one.
Now we will have to enter the super user password, that is, the “root” password, by default the password is “kali”.
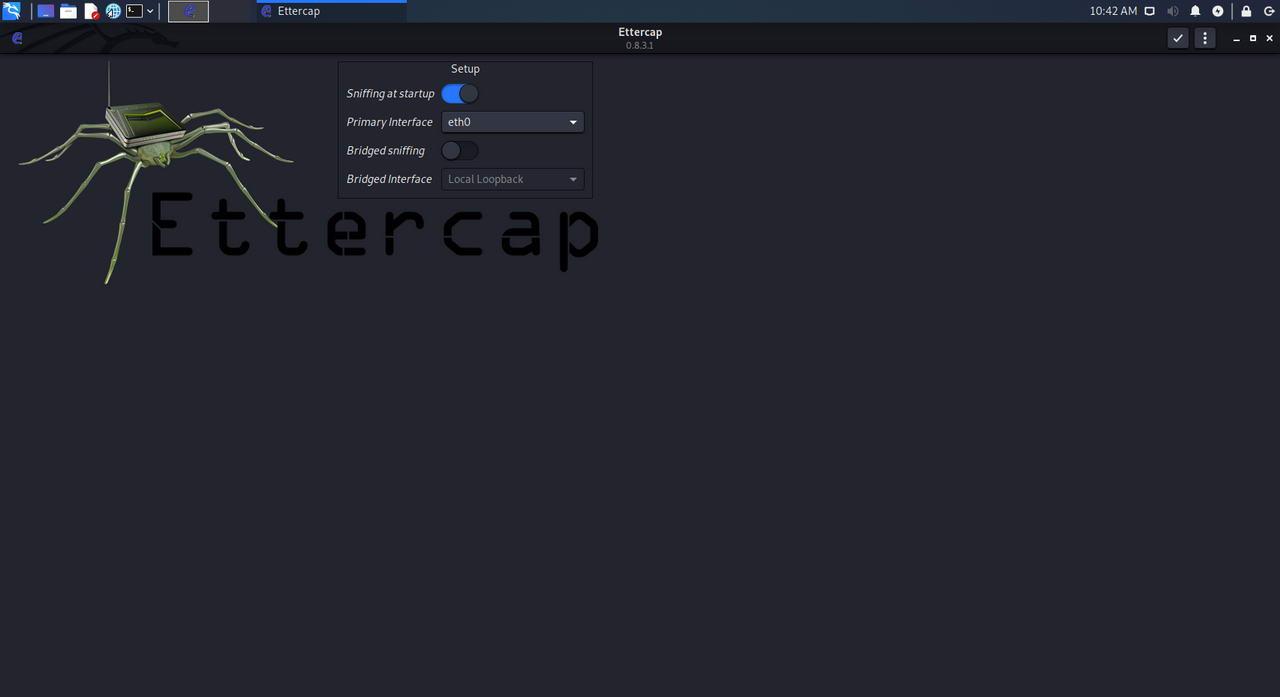
The next step is to select the basic Ettercap parameters, we can leave it with the default parameters, that is, start sniffing at the beginning, we will select the network card that we want, by default it is eth0. We leave the rest of the options as they are, and click on the button in the upper right part to accept the changes.
Once we have started the program, we will have to click on the “magnifying glass” that you see in the upper left, what Ettercap will do is scan the entire local network to which we are connected in search of the different devices that are connected, and therefore, some victim to attack.
Here we should get all the hosts or devices connected to our network. However, in case they do not all appear, we can carry out a complete scan of the network simply by clicking again on the «magnifying glass» that we have in the upper left part. After a few seconds, the list from before should be updated showing all the devices, with their respective IPs and MACs, connected to our network.
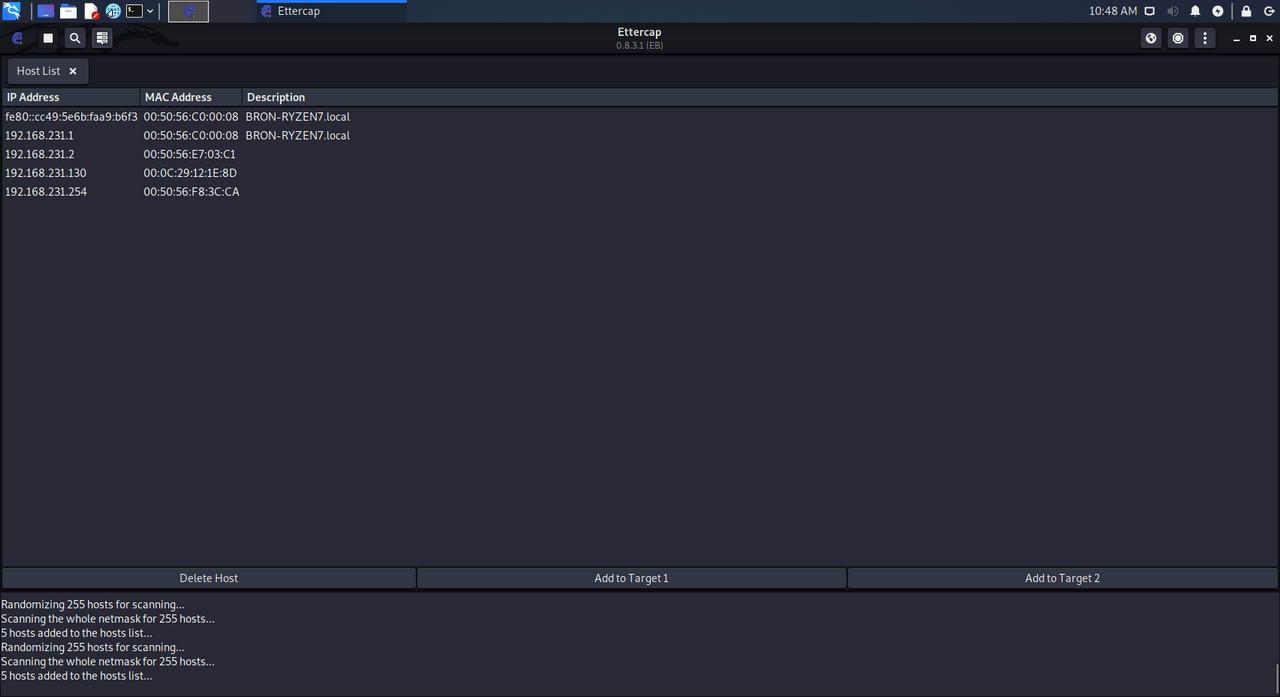
In case of wanting to carry out an attack directed against a single host, for example, supplant the identity of the gateway to monitor the connections of the victim that appears in the list of devices, before starting the attack we must establish both objectives.
To do this, below the list of hosts we can see three buttons, although we will pay attention to the last two:
- Target 1 – We select the IP of the device to monitor, in this case, the victim device, and click on that button.
- Target 2 – We press the IP that we want to impersonate, in this case, the one of the gateway.
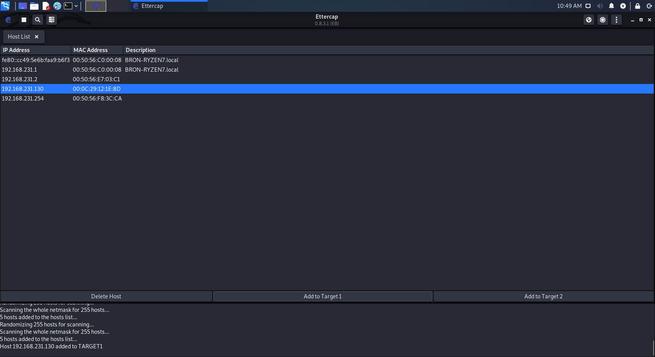
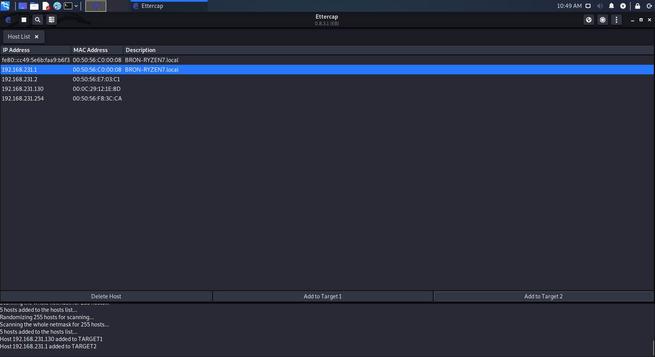
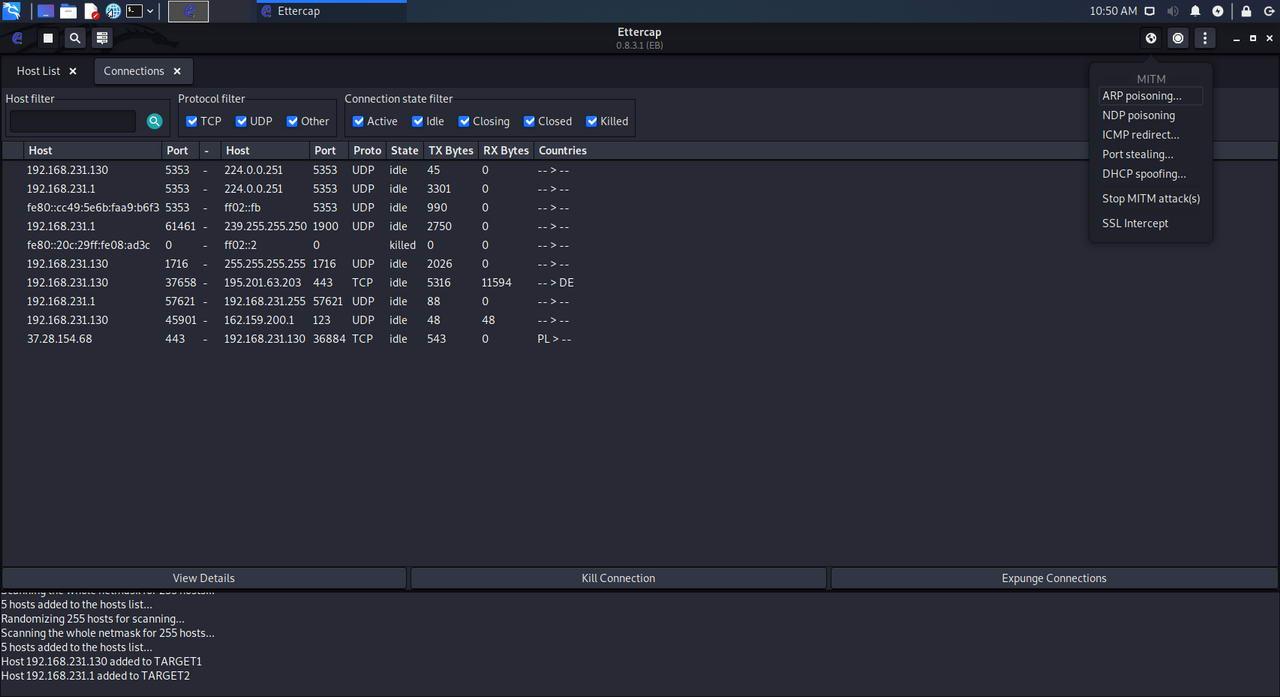
All ready. Now we just have to choose the ” MITM ” menu at the top and, in it, choose the ” ARP Poisoning ” option.
A small configuration window will appear, in which we must make sure to mark « Sniff Remote Connections «. We must also leave the “only poison one-way” option unchecked, this option will not perform ARP Poisoning in both directions but only in one, therefore, we do not have bidirectional communication. It is very important to leave this option “only poison one-way” unchecked, that is, as it is by default.
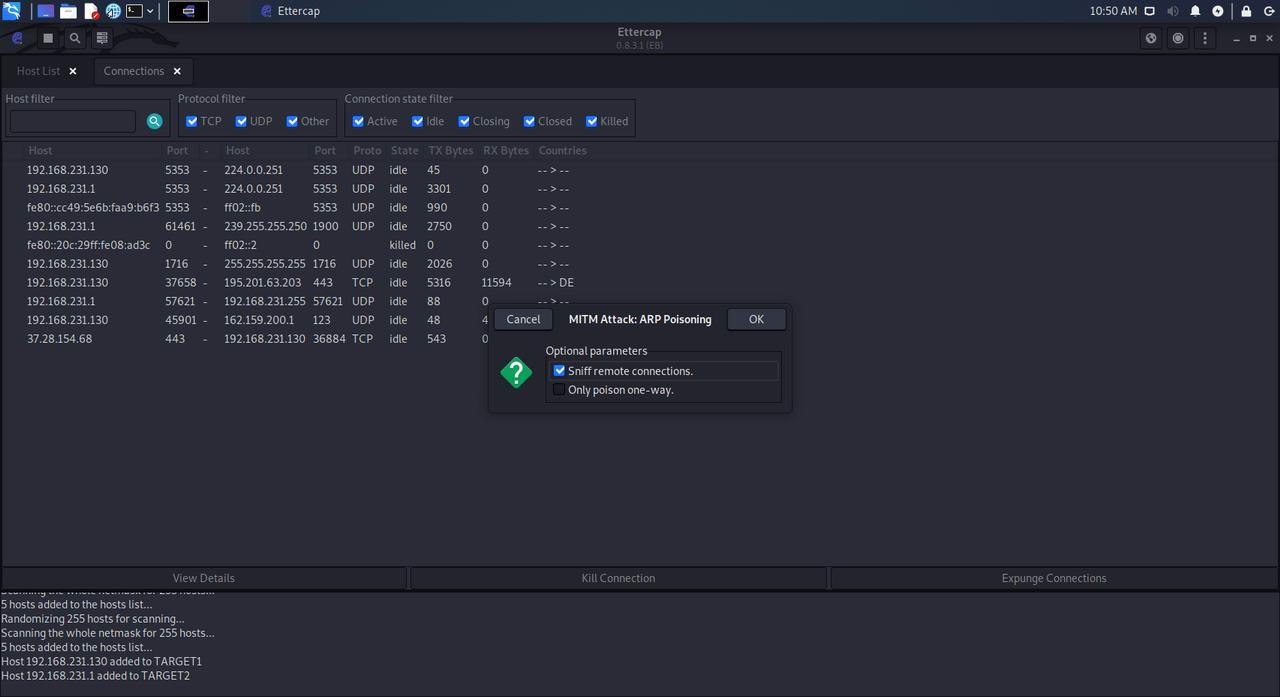
We click on «Ok» and the attack will take place. Now we can have control over the host that we have set as ” Target 1 “.
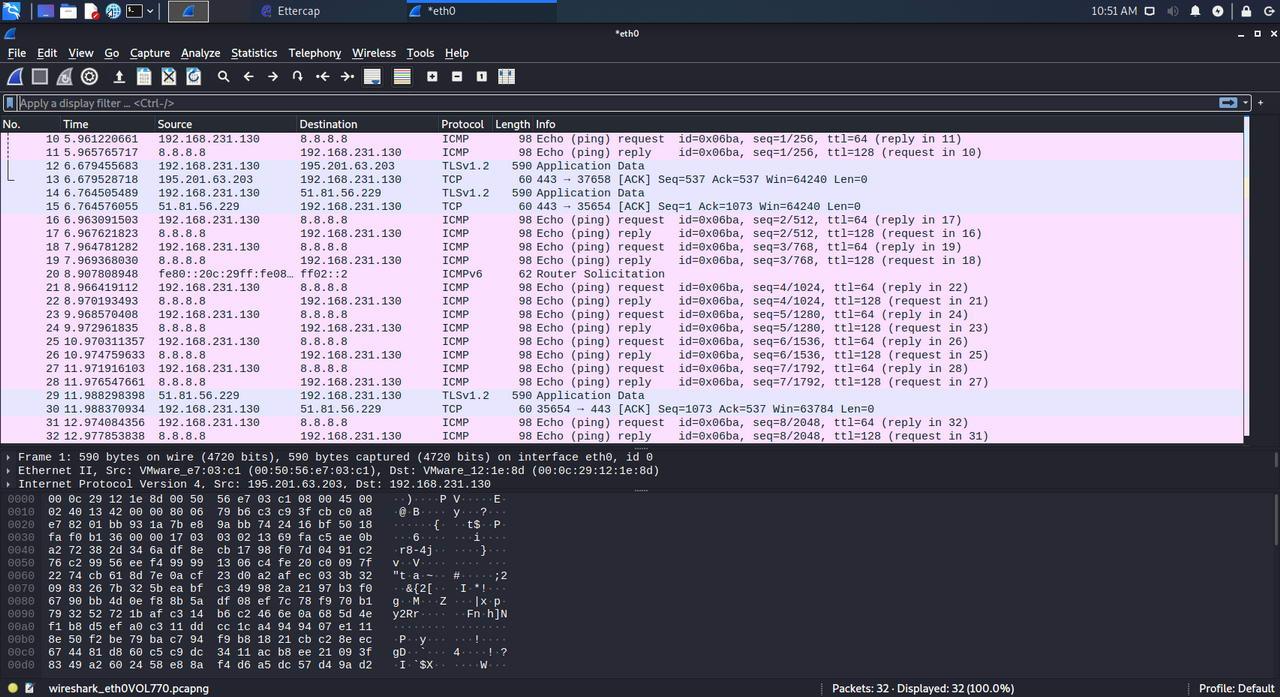
The next thing we must do is, for example, run Wireshark to capture all network packets and analyze them in search of interesting information or resort to the different plugins that Ettercap offers us, such as, for example, the remote web browser, where it will load us all the websites that the target visits. For example, we have done the typical ping to Google, the attacking team has captured everything correctly.
These techniques are only for private use within our own network, or in a network in which we have permission, logically these techniques can be applied for illegal purposes. If we use these techniques to monitor other people’s systems, we are committing a crime.
Once we have already learned how we can do this attack with Kali Linux easily and quickly, let’s see how we can mitigate this attack.
Detect and mitigate this attack to surf safely
This attack on data networks is very popular and is available to anyone, for this reason, it is very important to know how to detect if this attack is being carried out on us, and also how we can mitigate this attack so that it does not succeed. In many cases, the only thing we can do is encrypt all our communications so that, although they can capture all the information, they cannot read anything at all. Below, you can see all the details to detect and mitigate this attack.
How can I detect that this attack is being carried out on me?
The easiest way to detect that an ARP Poisoning or ARP Spoofing attack is being carried out is to check the ARP table, with the previous command of «arp -a» we can see the complete ARP table of our device, in case we have two IP addresses with the same physical MAC address, that means that someone is carrying out a Man in the Middle attack with an ARP Poisoning. For example, let’s imagine we have the following ARP table:
Internet address Physical address
192.168.1.1 00-01-02-03-04-05
192.168.1.2 00-01-02-03-04-AA
192.168.1.3 00-01-02-03-04-05
In this case, it can be perfectly seen that both the router and the second PC have exactly the same MAC address. This means that the ARP table is being poisoned. There are security programs that allow us to automatically detect if such an attack is being carried out on us, it will continually check the ARP table to find if there is a duplicate MAC address, then it will send the user an alert.
Measures to mitigate this attack
For a user, the only measure that can be taken to mitigate this attack is to use a VPN , this will guarantee the confidentiality and authenticity of all connections. We must remember that, in certain cases, it is possible to violate HTTPS connections using SSL Stripping techniques, therefore, if you want to be protected against this attack, our recommendation is that you use IPsec, OpenVPN or WireGuard type VPNs, all of them will guarantee us security and privacy in the network.
Another measure that a user could take is to register a static entry in our ARP table , however, this will only work if we always connect to the same networks, otherwise, we would have to be registering and deleting the ARP entry , which is very uncomfortable. If it is a static computer such as a desktop PC, it could be done this way, however, it is much better to do it at the network level by the administrator.
In the case of the administrators of the network itself, currently switches and routers / firewalls have anti ARP-spoofing techniques , in this way, if we activate these security measures, it will prevent an attacker from attacking another user within our own network, therefore, it would be a very important feature in order to protect its own users. We could also activate DHCP Snooping to prevent an attacker from setting up his own DHCP server to provide addressing to a specific victim or to several.
Finally, once we have carried out these mitigation measures, our recommendation is that you carry out this type of attack yourself to verify that your defenses are effective, that is, it is very important that you check your own security.