Vulnerabilities in software are one of the main gateways for cybercriminals, but poor configuration of our services, and even exposure of the TCP / UDP port to the Internet without any type of filtering, is also a vector of attack. Hackers are constantly looking for new ways to attack any computer, server or network through these security flaws, for this reason, the companies’ own engineers, security researchers and ethical hackers are constantly analyzing different programs on Look for security flaws and report it for fix. The essential tool for this task with vulnerability scanners.
A vulnerability scanner is software designed to automatically analyze any application, system or network, looking for any possible vulnerability that exists. Although these applications are not capable of detecting the vulnerability with total precision, they are capable of detecting certain elements that could trigger a vulnerability, greatly facilitating the work for researchers and engineers. There are several types of vulnerability scanners , authenticated, in which tests and potential attacks are carried out from the network itself, and unauthenticated, in which the ethical researcher or hacker tries to impersonate a hacker by simulating an attack from outside to See how far you can go by analyzing (and exploiting) possible vulnerabilities.

On the network we can find a large number of vulnerability scanners, most of them very similar, but with some aspects that clearly differentiate them and make them better, or simply different, than others. Today in this article we are going to see which are the most important and known to carry out a first pentesting.
Nmap
We cannot start a compilation with the best vulnerability scanners without talking about one of the most powerful, complete and veteran that we can find on the net: Nmap . This software is one of the most used to search for hosts within a network, as well as to search for open ports through which we can connect to a system remotely and even collect information about all the hosts on a network, such as the operating system you use or the services you have enabled on a certain port. This program is open source and cross-platform, although it is most common to use it on Linux operating systems to perform the pentesting task. This software has a large number of advanced options, and also has an optional graphical interface called Zenmap.
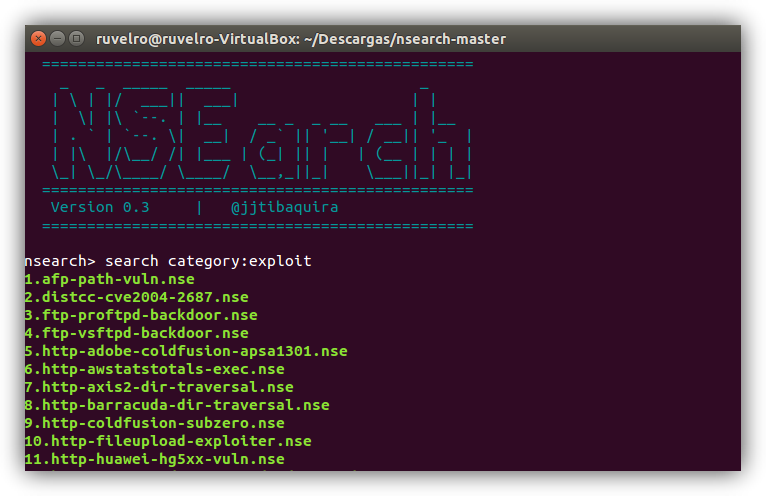
Although this tool was born as a port scanner, thanks to the NSE scripts that it includes by default (and that we can download from many web pages) it is possible to use it as a complete tool to search for vulnerabilities in networks and systems. NSE scripts use the power of Nmap itself, but it is also capable of exploiting known vulnerabilities to certain programs, so it is very useful to update it frequently with the latest scripts. Both NSE and Nmap make a really powerful team to help the hacker with pentesting.
In the following Nmap manual we explain how to download it and how to use it to search for possible vulnerabilities in a network or software.
Aircrack-ng suite
Wi-Fi networks are one of the weakest points of companies, and therefore it is one of the aspects that we must take care of the most. At this point, Aircrack-ng is without a doubt the best tool to test the security of any Wi-Fi network in search of any possible vulnerability that could allow any unauthorized user to obtain the password for our network.
Aircrack-ng is not really a single tool, but is made up of several tools that are specifically dedicated to different tasks:
- Airmon-ng: it is in charge of putting the Wi-Fi network cards in monitor mode, to allow the capture of all the information by Airodump-ng.
- Airodump-ng: it is capable of capturing data and exporting all the information, to later deal with third-party tools and even with other tools in the Aircrack-ng suite.
- Aireplay-ng: This tool is used to perform replay attacks, de-authentication of clients, create fake APs and other types of packet injection. An important detail is that the Wi-Fi card that we use, must be compatible with packet injection, since many are not.
- Aircrack-ng: this program is the one in charge of cracking the WEP, WPA and WPA2 keys of Wi-Fi networks, obtaining all the information obtained by the other programs in the suite.
If you have to pentest the Wi-Fi wireless networks, this suite is one of the fundamentals for you. If you are interested in pentesting wireless networks, you can see this master class on YouTube
As you can see, it lasts more than 3 hours and explains a large number of attacks that can be carried out, and even how to create our own tools.
Hashcat
Hashcat is a program that helps us to crack all kinds of password hashes, it is the best program to perform dictionary or brute force attacks against the hash of a key to try to crack it. Hashcat uses the power of the CPU and GPU to speed up the process of obtaining the key as much as possible. Although it is not a program that scans vulnerabilities, it will be widely used by you in case of obtaining the different password hashes, so we consider that it should be in this list of fundamental programs.
Wireshark
Continuing with network audits, Wireshark is the quintessential packet and protocol analyzer. This application is capable of recording absolutely all the packets that pass through a network, collect them and be able to filter and order them in a multitude of ways to be able to comfortably analyze all traffic. This tool is also capable of decrypting the packets sent through the main secure connection protocols to be able to analyze their content without problem.
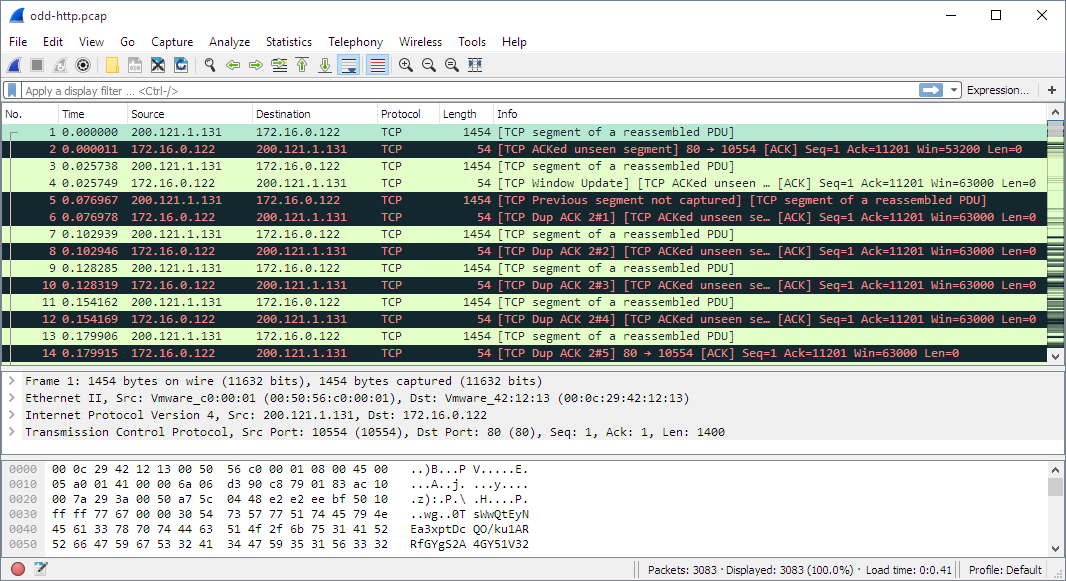
Without a doubt, the best application we can find to analyze any network and be able to detect any possible traffic leak or connections that try to exploit a security breach. It is compatible with Windows and Linux operating systems, in addition, it supports a large number of extensions that other programs use when capturing traffic, in this way, we will be able to analyze all the traffic later.
OpenVAS
Already entering the search for vulnerabilities in applications and computers, one of the most complete applications that we can find on the network is OpenVAS . OpenVAS is a vulnerability scanner to which we can enter an IP address and commission the analysis of said equipment, collecting information about the services in operation, open ports, configuration errors, possible known vulnerabilities in the software of the equipment or server, etc.
This program can be run both from within a network and from an external server, thus simulating a real attack. When it ends, it generates a complete report with all possible weaknesses that may pose a danger to our security. In addition, we can configure it in continuous monitoring mode, establishing alerts that will jump when the slightest failure is detected.
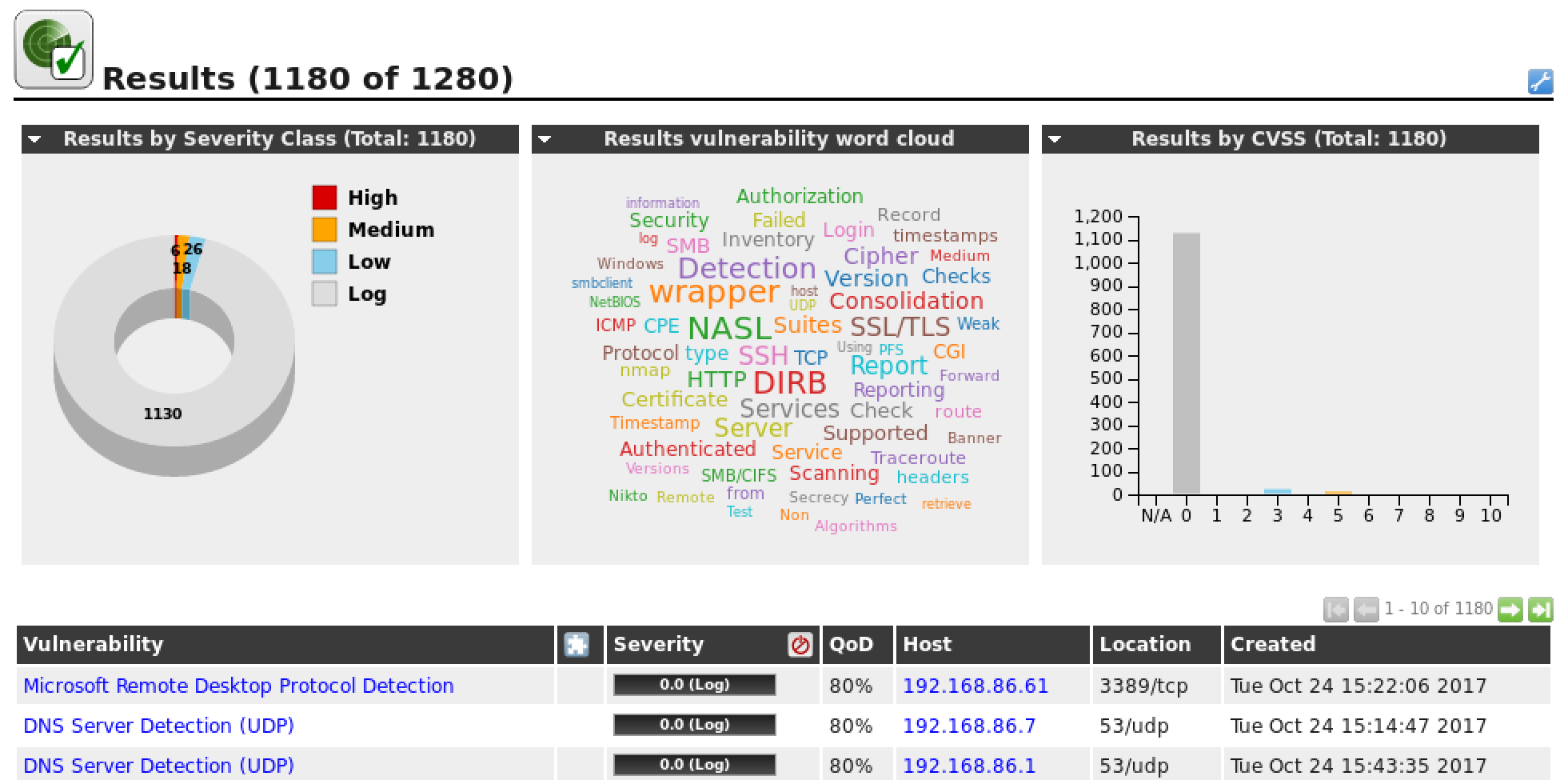
OpenVAS is a completely free tool that will allow us to carry out a large number of vulnerability tests against web servers, in addition, it has a large community behind it to support it and incorporate new functionalities to maximize its full potential.
OWASP Zen Attack Proxy ZAP
The OWASP project (Open Web Application Security Project) is an open and non-profit project designed to improve the security of networks, servers, computers and applications and services in order to make the Internet a safer place. Zed Attack Proxy , ZAP, is one of the free tools of this project whose main purpose is to monitor the security of networks and web applications in search of any possible security flaw, bad configuration and even still unknown vulnerability that may pose a problem for the net.
ZAP is a truly comprehensive tool, and if you are new to auditing it will be quite complex to get working, but once you know how it works, it is one of the best you can have in your arsenal of tools. On the official ZAP website they invite us to see all the videos of their tool where they will show us how it works and everything it is capable of doing.
Finally, ZAP has an addons store to increase the default functionalities of the tool, these add-ons have been developed by the community behind this project.
Nessus
Nessus is a vulnerability scanning program for all operating systems, it consists of a nessusd daemon that scans the target operating system, and nessus the client that shows the progress and reports everything it finds in the different scans. Nessus can be executed both at the console level by commands, or also with a graphical user interface. Nessus first starts by doing a port scan, since it is the first thing that is usually done in a pentesting, Nessus uses the power of Nmap for it, although it also has its own open port scanner.
This tool allows you to export the scan results in different formats, such as plain text, XML, HTML and LaTeX, in addition, all the information is stored in a “knowledge” database for subsequent revisions. Currently Nessus has a very limited free version, and later a much more complete paid version with support from the company behind it.
Some very important features of Nessus are that it has very few false positives, it has a great coverage of vulnerabilities and it is widely used by the entire security industry, so it is updated almost continuously to incorporate the latest technologies and security flaws in Applications.
Seccubus
Seccubus is a tool that uses other vulnerability scanners and automates the task as much as possible. Although this is not a scanner properly speaking like the previous ones, this application unites several of the most popular scanners on the market, such as Nessus, OpenVAS, NMap, SSLyze, Medusa, SkipFish, OWASP ZAP and SSLlabs and allows us to automate all analyzes in a way that from this single application we can carry out an analysis as deep as possible, in addition to being able to analyze programs at regular intervals to ensure that all equipment and networks are always properly protected and, in case something goes wrong, receive timely warnings real.
As you have seen, we have a huge number of programs to carry out vulnerability scans to our networks, computers, web services and other services that the servers incorporate. Depending on what we are doing, we will have to use one scanner or another.