Safety is a very important factor for users at all levels. We must always adequately protect our equipment, whatever the operating system. It also does not matter if we use a computer, mobile or any other. Neither is 100% self-protected. There are many threats on the Internet, but there are also many possibilities that we have to protect ourselves. In this article we are going to talk about what TPM is and how it protects our computers .
What does TPM mean
TPM stands for Trusted Platform Module. We can translate it as a Secure Platform Module. It is a unique hardware-based security solution that installs a cryptographic chip on the motherboard of a computer equipment, also known as a cryptoprocessor.

The function of this chip is to protect confidential data and prevent hacking attempts generated through the hardware of a computer. Each TPM contains computer-generated keys for encryption, and most computers today come with TPM chips pre-soldered to motherboards.
TPM works by generating an encryption key pair . It subsequently stores part of each key securely, as well as providing tamper detection. It simply means that a part of the private encryption key is stored in the TPM instead of being stored entirely on disk.
This is useful to prevent a hacker, in case he compromises our equipment, from accessing the content. TPM makes it impossible for cybercriminals to bypass encryption to access disk content, even if they remove the TPM chip or try to access the disk on another motherboard.

What benefits does TPM bring
As we can see, TPM is important for security. We already know that it is a fundamental factor and we must take care of our equipment at all times and thus prevent possible hackers from stealing information or compromising its proper functioning. Hence, it is very important to have all kinds of programs and features that help to enhance that protection, especially in devices that connect to the network and that may have more problems.
Data encryption
One of the benefits of TPM is data encryption . By using a combination of software and hardware algorithms, you protect your plaintext data by encrypting it. A way to protect everything we store on our computer and thus prevent a possible intruder from compromising privacy.
Data encryption is one of the most interesting options we have to protect ourselves on the network. When we are going to host content in the cloud, for example, we can take this option into account. But also at the hardware level, when we encrypt the disks of a computer.
Avoid malicious software in the bootloader
The TPM also helps protect a computer from specialized malicious software that can infect or rewrite the boot loader even before any antivirus software has a chance to act. Some types of malware can even virtualize the operating system to spy on everything without being detected by online systems.
A TPM can protect by establishing a chain of trust, as it checks the bootloader first and allows a startup anti-malware to start after that. It takes care of making sure our operating system is not tampered with and adds a layer of security. If TPM detects a compromise, it simply prevents the system from starting.
Quarantine mode
Another benefit of the TPM is the automatic switch to quarantine mode in the event of a compromise. If the TPM chip detects a compromise, it starts in quarantine mode so you can troubleshoot the problem. It is another very important protection measure that we can have on our team.
More secure storage
We can also safely store our encryption keys, certificates and passwords that are used to access online services within a TPM. This is a safer alternative to storing them within the software on your hard drive. On many occasions, it is essential to encrypt all content to prevent it from falling into the wrong hands and thus putting our privacy at risk.
How to know if TMP is enabled
We can know if we have TPM enabled in Windows in a simple way. To do this, you have to start the Windows + R key combination and run tpm.msc . This, if enabled, will open a new Trusted Platform Module Administration window. We will see a window like the one in the image below.
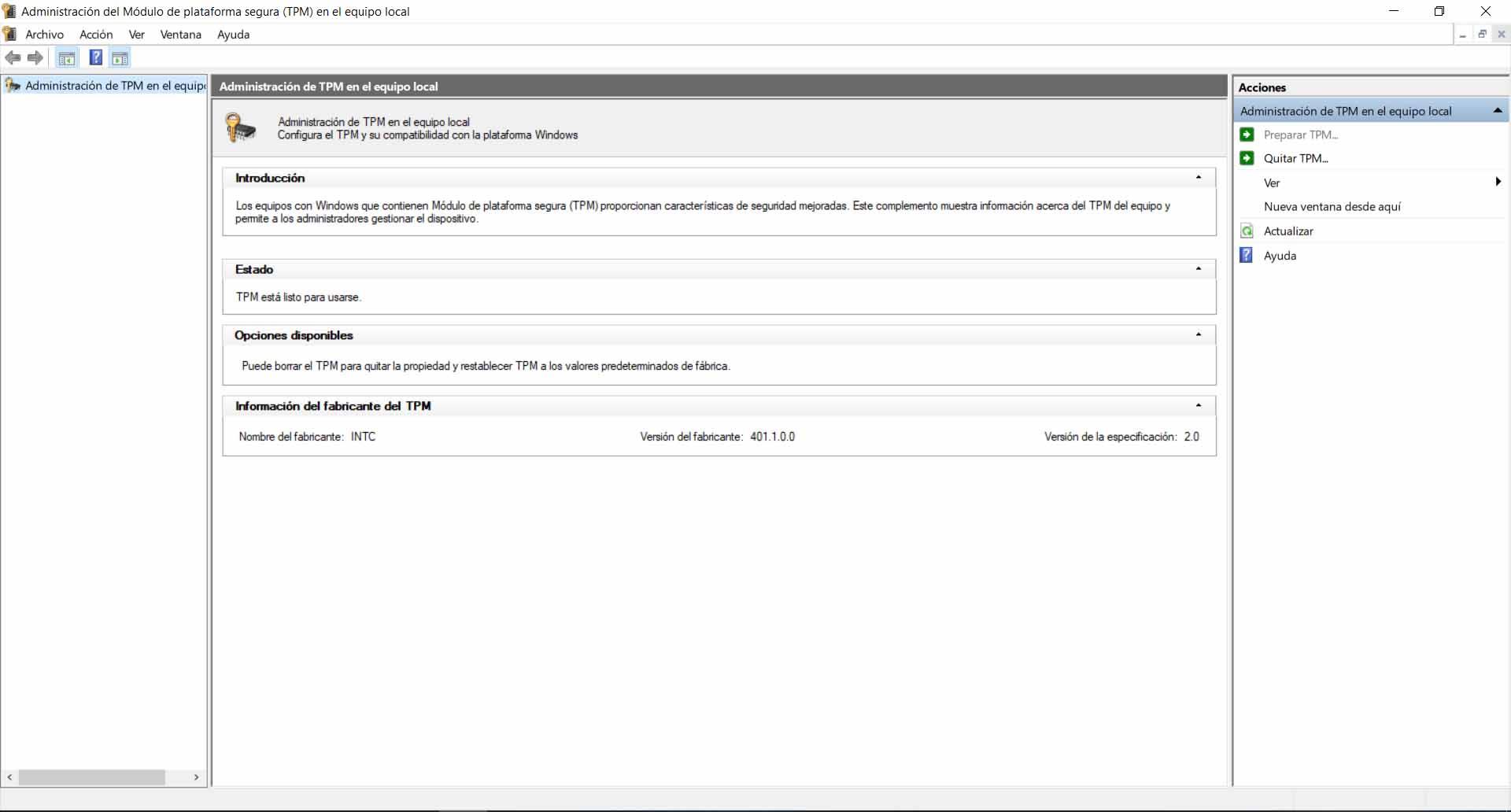
In case we see an error message it would mean that we do not have TPM enabled on our computer. It would not be normal, so in that case we would be facing a problem that we should correct to adequately protect our equipment. It could be due to a bad configuration or the entry of some type of malware. It would be necessary to analyze the cause and try to correct it.
In short, as we have seen, TPM is something important for our security. It helps to protect Windows against different attacks and problems. Protecting data, avoiding intruders who can access the system and stored information, is very important. It is one more complement to any service or program that we use to avoid intruders and always keep our equipment safe.
We must always keep the equipment properly insured. For this, you not only have to have an antivirus, but also have it updated and make use of the tools that are integrated with the operating system. On many occasions, vulnerabilities can appear that are exploited by cybercriminals. This means that we must apply any patch that is available, whether on a desktop, mobile or any other device that is part of our day to day.