A new security flaw has been found in Windows 10. This time it affects one of the basic commands of the Microsoft operating system. The affected one in this case is the Finger command, which can be exploited to download and steal files easily and quickly. The list of native Windows executables that can download or run malicious code continues to grow, and the Finger command has just been added to the list.
These are known as living-off-the-land binaries (LoLBins) and can help attackers bypass security controls without triggering a security alert on the system. Thus, as attackers use pre-installed tools to carry out their work, it makes it more difficult for defenders to detect attacks that are occurring on systems.

How the finger command works
The Finger command is a command that all Windows users have available. To start using it is as simple as:
- We go to the Start Menu.
- We write cmd to enter the command line.
- We write Finger and hit enter.
Here is an example of the Finger command for Windows 10 in which it shows us the parameters offered by this executable.
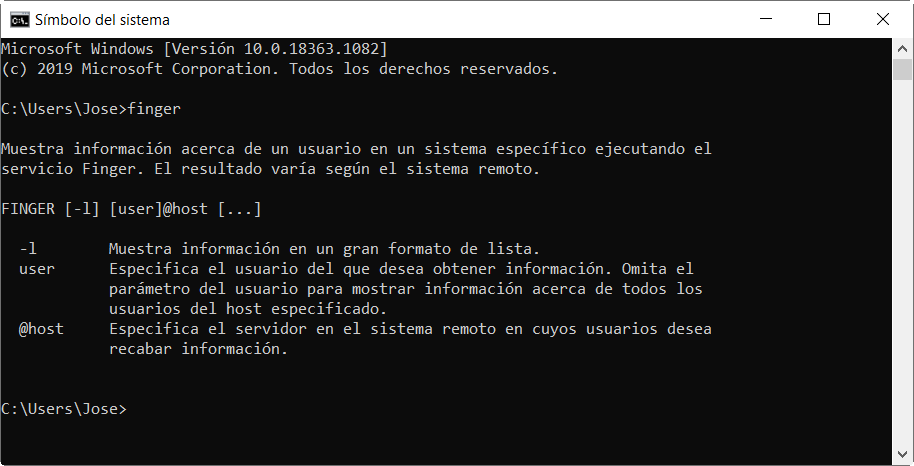
As you can see, we will use -l to specify the user from whom we want to obtain information. We also have @host to specify a server on a remote system and get information from those users. In this sense, the Finger command found in Windows 10 is used to retrieve information about users on remote computers running the Finger service or daemon. What it does is show us information about the users of a specific remote computer that normally has a UNIX operating system, and is running the Finger service.
How can we exploit the Finger command to steal files
Security researcher John Page has found that the Finger TCP / IP command in Microsoft Windows 10 can also be used to:
- Downloading files.
- Be used as a makeshift command and control server that can be used to send commands and filter data.
According to the aforementioned researcher, by using commands we can mask Finger queries to download files and exfiltrate data. Thus, if we do it this way, Windows Defender will not detect any suspicious activity. The fault could be found in that port 79, which is the one used by the Finger protocol and which is frequently blocked within a company. However, an attacker with sufficient privileges can circumvent the restriction. We could do this using Windows NetSh Portproxy, which acts as a port forwarder for the TCP protocol.
Thanks to this way of working, it would allow us to overcome the firewall rules and communicate with the servers through unrestricted ports for HTTPS. So by doing it this way, the Portproxy queries are sent to the local machine IP and then forwarded to the specified host. It should also be noted that the Finger command to download files also has limitations. However, it is not something we cannot solve, since, if we encode the files with Base64 it will be enough for us to avoid detection.
Video of the Finger command in action and more
John Page, the researcher we talked about before, uses the hyp3rlinx nickname to make his publications. In a video you have demonstrated how you used the Finger command to download files. This security researcher has created proof of concept (PoC) scripts. In that sense, it published DarkFinger.py for the server and DarkFinger-Agent.bat on the client side to demonstrate that double function that allows us to perform finger.exe. If you want to consult those scripts you can do it from here .
Here’s the video from hyp3rlinx showing how the DarkFinger script completed the test without interruption on a Windows 10 PC, and furthermore that Windows Defender did not detect any suspicious activity.
In a Talos Intelligence report from last year, 13 LoLBins were listed that affected Windows, for example we have the famous powershell.exe or certutil.exe. Finally, it should be noted that the Finger command, as has been demonstrated, will become part of the list of LoLBins that we can use in windows.
We recommend that you read our tutorials on how to protect a Windows 10 system , and how to improve Windows Defender security , to protect your Windows as best as possible.