Google and Microsoft have their own engineers who are constantly analyzing their programs for vulnerabilities that could pose a danger to users. In addition, thanks to the Bug Bounty programs, any user, hacker or researcher who wants to can report bugs in exchange for monetary rewards that vary depending on the severity. But even so, there are always users who decide to go on their own and, instead of reporting a bug and keeping it private, they decide to make it public, putting users at risk and exposing companies. And this is what just happened with Chrome and Edge.
Again, another glitch in Chromium’s V8 JavaScript engine
Just a few hours ago, a well-known security researcher, Rajvardhan Agarwal , just published a zero-day security flaw (that is, a flaw that has not yet been fixed), along with a proof of concept, which works on the latest versions. of the two most used web browsers: Google Chrome and Microsoft Edge.

This security flaw is found in V8, Chromium’s JavaScript rendering engine, and allows code to be executed on the vulnerable system through it. Since the V8 engine is part of Chromium, all browsers based on this engine are affected by this vulnerability.
When the proof of concept is loaded, using a simple HTML file, and the corresponding JavaScript file is loaded, the browser is able to run programs (be it the Windows calculator, or whatever malware has been downloaded to the PC) without the user have to do anything.
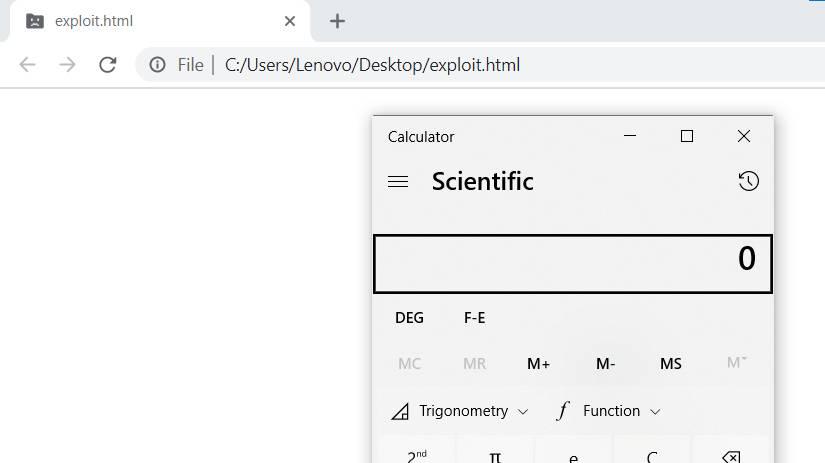
Fortunately, it is not all bad news. Currently, this 0-day bug cannot escape Chrome’s sandbox mode. This mode, activated by default, what it does is isolate the browser process from the rest of the system so that, in the event of a failure of this type, it cannot access the system’s processes or programs. For the PoC to be successful it is necessary to run the browser with the “–no-sandbox” flag, which disables this mode.
As a fun fact, this is the same bug (or a very similar bug) as one discovered and used in Pwn2Own 2021.
How to protect ourselves from vulnerability in Chrome and Edge
As we have explained, luckily, the bug cannot get out of the browser sandbox. Therefore, if we run the browser with this mode (something that is done by default) we do not have to worry , since we will be safe. On the contrary, if we are running the browser without this mode, we must start by activating it to prevent the exploit from leaving the browser’s safe space.
Google has already fixed the vulnerability in Chrome’s V8 engine, although this update has not yet been released to users. It is expected that it will be tomorrow, with the launch of Chrome 90 , when this vulnerability will be corrected. Meanwhile, if we have the browser with the sandbox mode activated, and we navigate carefully not to reach suspicious websites that may be dangerous, we do not have to worry.