Millions of people download torrent worldwide. Torrent downloads are a very efficient way to share files from any part of the planet in a decentralized way without depending on servers, since everything is done peer-to-peer ( P2P ), or from one user to another. In this process, our IP is known to anyone who is downloading a torrent that we are sharing. But why is this so?
To do this, you have to understand how a P2P network works. These networks, as we say, are formed by private computers of users who act as equals among themselves. They are both servers and clients at the same time, and being able to do it freely between two or more computers has made these networks the ideal place to share content subject to copyright, such as movies, series, music or software. These virtual networks (trackers) to share files are created on top of the “real” networks, and are beyond the control of the authorities.

However, in order for a user to find another, there needs to be some kind of identification element. When we download a torrent file or add a magnet, what we are doing is adding the networks in which that file is being shared. Those networks are the trackers, or trackers, that are in charge of managing the data that each user has of a specific torrent to distribute them efficiently.
Anyone connected to our tracker knows our IP
The entire set of IP addresses managed by a tracker that are currently sharing or downloading a torrent is known as a ” swarm “. As soon as we stop downloading or sharing it, we disappear from that swarm. There are two types of trackers: public and private. In both, the IP address is known by the members of that swarm, since it is the only way to identify our identity facing the Internet. Also, we can see which clients each user uses, as well as the ports.
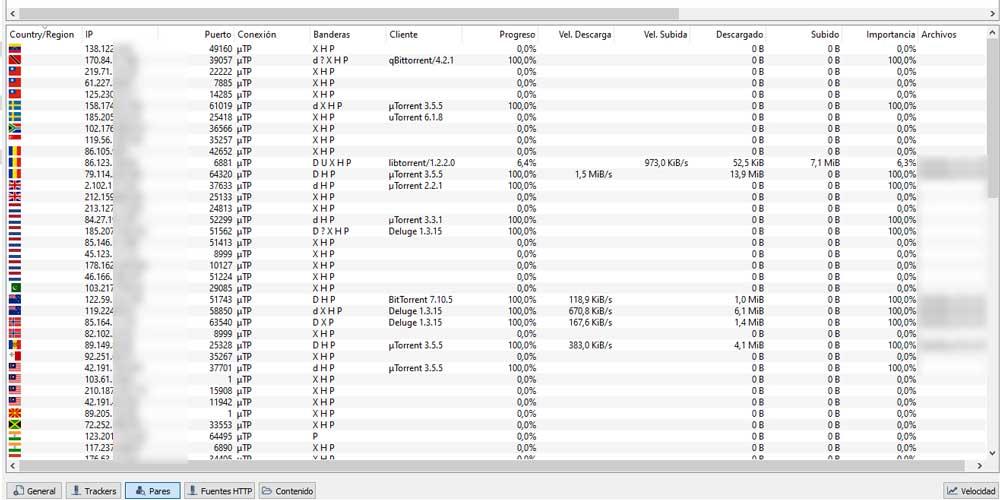
This makes it relatively safe for private trackers to see our public IP, since only members of that closed tracker will know it, and it is necessary information to associate our file upload and download statistics.
The problem is that on public trackers this can be very dangerous. So much so, that the web iknowhatyoudownload.com collects all the torrents that an IP address has downloaded. With this, we can know what a person downloads, or at least the people who are within that local network. The website has a database of 1.5 million torrents , and accounts for more than 200 million daily downloads , analyzing both torrent websites and listening to DHT. So there are some poorly shared torrent that can escape your analysis.
So, imagine for example that a member of the audiovisual industry decides to search for all users who have downloaded one of his latest films. All you have to do is start sharing the torrent, and collect everything that users download. Curiously, it is only possible to know the IP addresses that are sharing a content if you are uploading or downloading it too, so any crime that you accuse those users should also be applicable to whoever is monitoring those downloads.
Once they get the IP addresses, these companies ask a judge to compel operators to identify the owners of those IP addresses. In the event that they are transferred is when the legal problems can start, as happened to some users in Spain who downloaded the movie Dallas Buyers Club and others.
A VPN, the best solution to protect our identity?
This is easily solvable with a VPN. With it, we can hide our real IP by redirecting traffic through another node that is the one that “sees” the swarm. Thanks to this, and assuming that our VPN does not share our real IP with third parties if requested by a judge, our identity will be safe at all times.
The problem with using a VPN is that, in the case of free VPNs, the speed is very limited because we are sharing bandwidth with hundreds or even thousands of users, so we will not have all the speed that our fiber optics offers. In the case of private ones, we have more available traffic, in addition to a greater certainty that they will not share our real IP address if a judge asks for it.
Operators can tell if you are sharing torrent
Encrypting traffic through a VPN will also hide what we are doing on the network from the operator’s eyes. Without a VPN, an operator can tell if we are sharing P2P traffic, as they can see that there are several active upload channels and many different TCP connections, since you are communicating with many IP addresses at the same time. Fortunately, even though they know the type of traffic, European net neutrality laws prevent an operator from slowing down these connections.

At the beginning of the 21st century, when BitTorrent began to emerge, clients used ports 6881 and 6889 by default, causing operators to quickly block them to prevent content from being shared by P2P. Since then, torrent clients use random ports with each opening to avoid such blocks.
P2P traffic back then was also communicating unencrypted, making it possible to inspect packets to see what was being downloaded. To fix it, Protocol Header Encryption (PHE) or simply Protocol Encryption (PE) was included , which encrypts BitTorrent traffic. However, the type and number of connections is still known to operators, and the IP addresses that share each content are still known to any member of the tracker.
To avoid blocking the trackers, the DHT we mentioned before is also used, which implies that even the trackers are not centralized, so they cannot be blocked because the information is also exchanged between them via P2P using UDP.
In short, the only thing we can do to protect our IP when downloading torrent is to use a VPN, or have an operator that has CG-NAT to mix our IP with many other homes so that our identity is protected.