07OpenVPN is one of the most used VPNs at home and professional level, it uses all the standards based on TLS 1.2 and TLS 1.3, therefore, the security we will obtain is optimal. Another very important feature of OpenVPN is that it incorporates a huge amount of configuration options, both for the data channel, the control channel and even for the routing and internal operation of the VPN. The only downside to OpenVPN is that it is currently vastly slower than WireGuard VPN under the same hardware and network conditions, but this could be over soon and both have similar performance.
In this article we have an extensive OpenVPN configuration tutorial where we explain in detail all the technical characteristics, how to configure the VPN server, the VPN clients and we even indicate several problems with their solutions, so that you can configure a VPN tunnel from scratch with this software. We also have a tutorial with the same information for WireGuard, a VPN that has found a place among us very quickly due to its ease of configuration, the default security it incorporates, and most importantly: the transfer speed .

OpenVPN speed vs WireGuard vs L2TP / IPsec
In this article we have carried out a speed test with high-end hardware on both the client and the server to check the real performance of the three most used VPNs, both at home and at a professional level.
The VPN client has the following hardware:
- Processor: AMD Ryzen 7 3800x, this processor has a total of 8 cores and 16 threads, the most important thing is that it has AES-NI hardware encryption acceleration, therefore, whenever AES is used in the communication channel the performance will be optimal.
- RAM: 32GB RAM DDR4 3200MHz
- Connectivity: ASUS XG-C100C at 10Gbps with D-Link DXS-1210-10TS managed switch and Cat7 cables, guaranteeing real 9.5Gbps of bandwidth.
- Operating system used in the tests: Windows 10 latest version.
- Tool used: iPerf 3
The VPN server has the following hardware:
- NAS server used QNAP TS-1277
- Processor: AMD Ryzen 7 2700, this processor has a total of 8 cores and 16 threads, the most important thing is that it has AES-NI hardware encryption acceleration, therefore, whenever AES is used in the communication channel the performance will be optimal.
- RAM: 64GB RAM DDR4
- Connectivity: QNAP QXG-10G2T-107 at 10Gbps with D-Link DXS-1210-10TS switch and Cat7 cables.
- Operating system used in QTS 4.4.1 tests.
- L2TP / IPsec VPN from QVPN and iPerf3 installed on QTS.
- OpenVPN and WireGuard installed on Linux (Ubuntu 18.04 LTS).
- iPerf3 installed on Linux Station (Ubuntu 18.04 LTS).
The configuration of the different VPNs in the tests was as follows (for the data channel):
- OpenVPN: data channel with AES-256-GCM.
- WireGuard: ChaCha20 / Poly1305
- L2TP / IPsec: data channel with AES-128.
In principle, with this AES configuration, both OpenVPN and L2TP / IPsec should have an advantage because we have hardware encryption acceleration, however, the performance obtained is as follows:
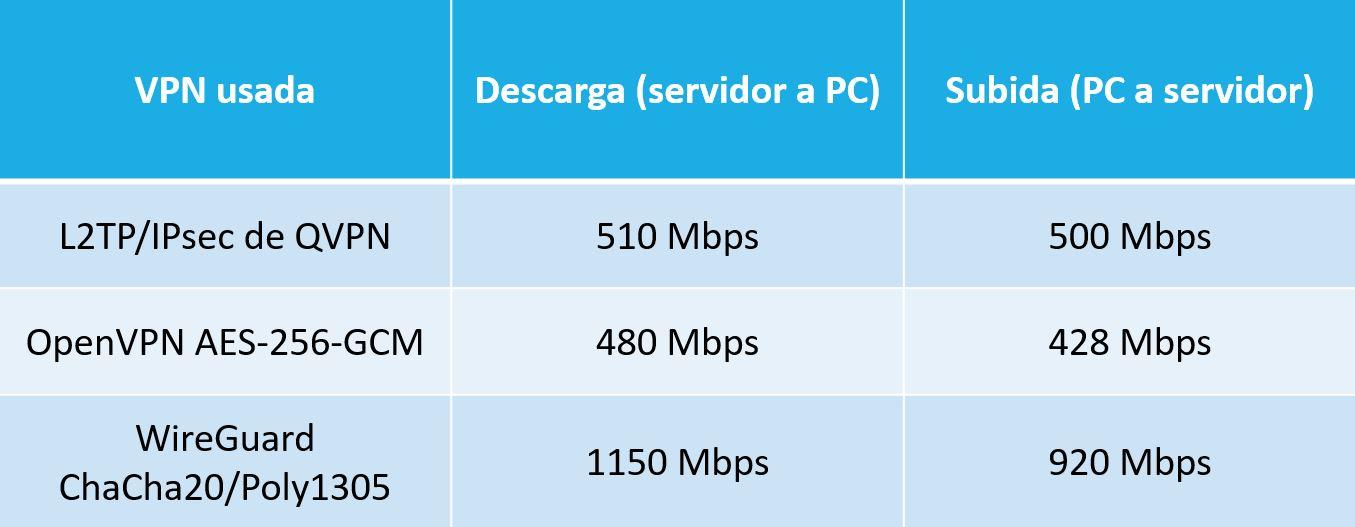
As you have seen, WireGuard is twice as fast as L2TP / IPsec or OpenVPN, proving that this VPN is really fast compared to its more direct rivals.
OpenVPN will be able to be integrated into the Linux kernel soon
The advantage that WireGuard has over the rest of VPNs is that it is directly integrated into the Kernel, therefore, it is really efficient and the performance is spectacular, as you have seen in the comparison table. Now, the OpenVPN development team is developing the “OpenVPN Data Channel Offload (ovpn-dco)” feature that can be integrated into the Linux Kernel with a specific module, all to achieve better performance in terms of latency and speed. .
What will be incorporated into this module is the entire OpenVPN data channel , making an offload in the server and client load. In addition, a very important detail is that currently this only works with AES-256-GCM, therefore, if we use some other type of symmetric encryption in the data channel, this will not work and we will continue to have the same performance as always. The control channel will continue to be outside the Kernel, although it is really fast thanks to the incorporation of TLS 1.3 in the latest versions of the OpenVPN protocol. Thanks to this module, we will avoid the transfer of payload between the kernel space and the user space, greatly optimizing performance.
In the GitHub repository you can find all the current source code, although we must bear in mind that this feature is currently experimental and in development, so it is not recommended to use it in production, but only in tests to check if there is any type of performance problem.