Although social engineering scams are more prevalent and do not require much sophistication, there are still large groups of hackers that use advanced programming to infect their victims and extract as much information as possible.
RedEyes, one of these most famous hacker groups in the world, has recently returned to the fray, releasing a new malware that arrives camouflaged in seemingly harmless image files and quite undetectable, since it leaves very few traces.

This is how the M2RAT malware infects you
The APT37 hacker group, also known as RedEyes or ScarCruft , is a North Korean cyber espionage group believed to be state-supported. Now it has been discovered that they use a new evasive malware called M2RAT for data stealing and intelligence gathering.
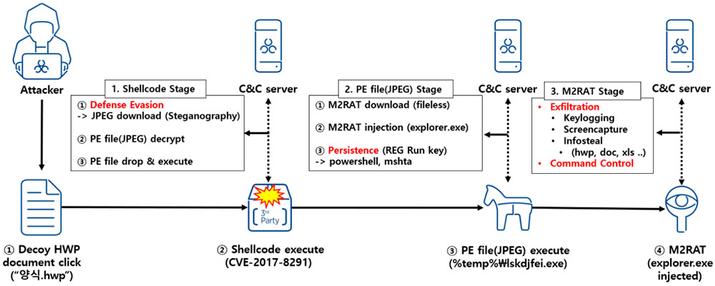
As reported by AhnLab Security , this new strain of malware called M2RAT uses a shared memory section for commands and data extraction and leaves very few operational traces on the infected machine.
The group of hackers sent phishing emails containing a malicious attachment to their targets. Opening the attachment triggers the exploitation of an old vulnerability in EPS ( CVE-2017-8291 ) in the Hangul word processor commonly used in South Korea. The exploit causes shellcode to be executed on the victim’s computer that downloads and runs a malicious executable stored within a JPEG image .
This image file uses steganography , a technique that allows code to be hidden within files, to stealthily introduce the M2RAT executable (“lskdjfei.exe”) into the system and inject it into “explorer.exe”.
Hackers infect Windows and phones
The M2RAT backdoor acts as a basic remote access Trojan that performs keylogging, data theft, command execution and screenshot taking, which activates periodically and works autonomously without the need for a command. operator specific. The malware supports commands that collect information from the infected device and then send it to the C2 server for review by attackers.

Particularly interesting is the ability that this malware has to search for portable devices linked to the Windows computer, such as smartphones or tablets. If a portable device is detected, it will scan the contents of the device for documents and voice recording files , and if found, copy them to the PC for leaking to the attacker’s server.
Before extraction, the stolen data is compressed into a password-protected RAR file and the local copy is wiped from memory to remove any traces.