Little by little, network architectures and their traditional management models are lagging behind. This guide will show you the basics of micro-segmentation and how it adapts to these new network architectures that work with multiple cloud services and virtualization. A much higher level of security is one of its most outstanding features.
What is microsegmentation?

It is a type of network segmentation that is specifically aimed at dealing with critical problems, those that have to do with network protection . The main objective is to reduce the risks of attacks and adapt security measures to the demands of use. Microsegmentation is a modern approach to provide networks with greater security, very much in line with dynamic Information Technology environments.
Network security is no longer an optional matter in its management, this segmentation model is a more practical and simple way to start adopting the Zero-Trust model in networks. Remember that the latter consists of applying all access controls, authentication and more, to all users equally, without distinction of roles and functions within an organization.
How does it work
Micro-segmentation applies to each member a unique and centralized network policy. This allows an implementation of network policies that goes beyond where people are. That is, it no longer depends on where the user is connected. Now, it depends if the user is actually connected. This way of applying network policies is necessary because cloud services are increasingly adopted, and these, of course, go far beyond the perimeter of a given network.
Although it is apparent, micro-segmentation is aimed at end users. Especially due to the fact that a large part of the events that threaten network security originate from the devices of said end users. In other words, this way of managing networks is not closed to huge corporate infrastructures such as data centers.

Types of micro-segmentation
Host-agent
This is focused on end users. All data traveling through the network passes through a device that acts as the central manager . One of the main advantages is avoiding having to discover and decrypt algorithms and / or encryption protocols that the traffic has. However, for this micro-segmentation strategy to work to its full potential, specialized software must be installed on all hosts on the network. Also, it is important to know that by using the Host-agent type it will be possible to prevent security events on the network even before a host enters the network itself.
Based on Hypervisors
What is a Hypervisor? It is the core of many hardware virtualization technologies. These are responsible for deploying and managing the guest operating system, that is, virtualized. The advantage of implementing micro-segmentation with hypervisors is that already implemented firewalls can be used, in addition to migrating current network policies to the same hypervisors or others, depending on how network activity is migrating to this management model.
However, this model is not the most recommended. Because it does not work entirely in cloud environments, containers or bare-metal hypervisors (those that are installed on the computer hardware itself and from there, virtualization is carried out).
We can also cite another model that is seen as an extension of traditional network management . Which, for example, includes segmentation based on Access Control Lists and other methods. According to the experts, this is the easiest model to adopt, considering that it is not a “sudden” change in ways of managing the network. However, problems can start from the moment you want to adopt micro-segmentation to very large network segments. This is so because when managing and providing event support, many financial resources and specialized personnel are required.
Why is micro-segmentation safer?
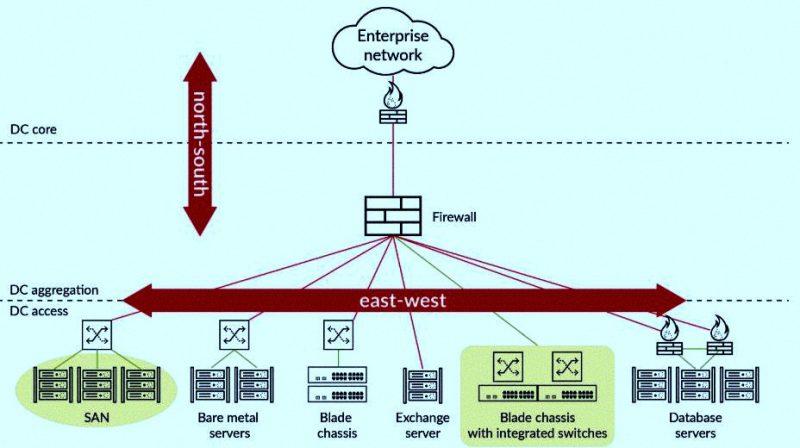 Palo Alto Networks explains the importance of micro-segmentation in the context of “North-South” network traffic (North-South in the graph) and “East-West” traffic (East-West in the graph) . Network segmentation, as we know it, works best when it comes to North-South traffic, which involves server-client-type communications across the network. Today, network architectures in general have been renewed thanks to cloud services and their combination is known as hybrid architecture . The latter has more East-West network traffic, that is, server-to-server communications.
Palo Alto Networks explains the importance of micro-segmentation in the context of “North-South” network traffic (North-South in the graph) and “East-West” traffic (East-West in the graph) . Network segmentation, as we know it, works best when it comes to North-South traffic, which involves server-client-type communications across the network. Today, network architectures in general have been renewed thanks to cloud services and their combination is known as hybrid architecture . The latter has more East-West network traffic, that is, server-to-server communications.
The graph we shared above demonstrates how much of the network traffic occurs with the East-West rate. We see servers dedicated to Storage Area Networks (SAN networks) and Exchange servers (or any other dedicated to emails). We can also see servers dedicated to functioning as databases which are surrounded by firewalls.
Another point in favor of microsegmentation is the increasing use of virtual machines and other virtualization methods. Remember that it is possible that a single server can host multiple virtualizations, each with its corresponding workload and security requirements. This renewed way of segmenting improves security measures at a granular level, that is, according to each component of the network.
Considerations before implementing it
There are essentials before making an investment to implement network micro-segmentation. It is recommended to have a control with a high level of detail in relation to which network architecture is used, in addition to which systems and applications are used. On the other hand, you must know how the systems communicate with each other.
For all this, it is necessary to carry out an analysis with all the parties involved. Especially if we are talking about a large network that has critical operations that are carried out on a daily basis. It is even possible to carry out this analysis with the support of the provider. In this way, it will be much easier to identify the points where the micro-segments will be installed. Here, the most important thing is to avoid as far as possible that there are no drops in network functionality.