Every day we suffer more attacks from malware, viruses, phishing etc. since cybercriminals do not rest and are on the lookout for new opportunities with which to profit. In this sense, we are going to offer you a series of tools and tips to prevent e-mail from becoming the weakest link in our security.
It has been discovered that e-mail is the weakest element in the security chain, since generally we all have a main email account where we have the main services, therefore, if our email is hacked, they will be able to access the rest accounts easily.

A third of security incidents originate from an email
According to the security company F-Secure, more than a third of all security breaches that occur in a company are initiated by sending a phishing email, or malicious attachments to company employees. Therefore, due to this, we can consider e-mail as the weakest element in the security chain, and companies, to prevent it, must train their employees explaining the methods to avoid it.
Currently, e-mail or electronic mail has made this service a very important part in the daily work of companies. Thanks to this communication tool, you can deliver official documents, business proposals and have a business conversation.

However, the use of email is also important for individual users, because thanks to this they can keep in touch with friends and family. Also in the private sphere you can be a focus of risk, receiving an email from someone you trust makes it less suspicious and you take less precautions. However, it can be a fatal error and can infect your computer. Also, if you are at work, things get complicated, and if your PC is networked it can affect more computers.
On the other hand, e-mail is undoubtedly one of the best ways for cybercriminals to achieve their goals. The reason is simple, they can hide under a fake email account and deceive the user. This anonymity that they achieve makes them feel more secure and believes that they will emerge unscathed, which is dangerous for victims.
Report on attacks received by computer equipment
According to the F-Secure report, the risks of email still represent a great danger for companies, as can be seen in this graph, which shows the types of attacks they can suffer.
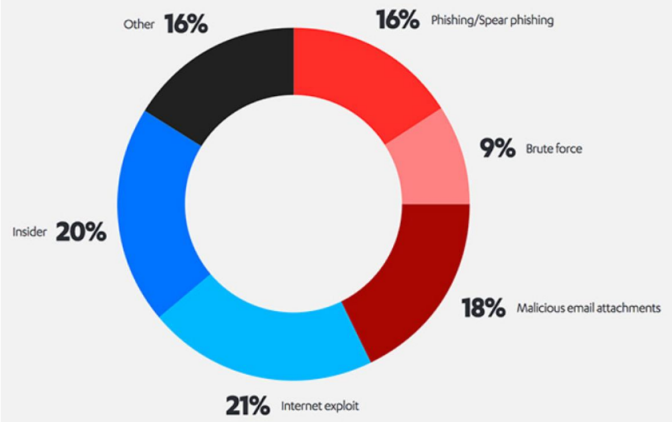
If we analyze the graph in depth, we see that the most common source of infractions were attackers who exploited vulnerabilities in a company’s Internet services, their percentage being 21%.
Other elements that also affect companies a lot are, with 16% phishing, and emails with malicious attachments 18%. If we add them together, they represent approximately 34% of the infractions, which indicates that we must be very vigilant about them.
The procedure they use is based on basic social engineering schemes, so sending false emails usually works out more than hacking systems. These types of attacks are popular because almost all companies depend on email for their operation.
Therefore, from this article, a tip that we recommend is that, when we receive an email, let’s think carefully before clicking to open that attachment. If we are not sure that it is a trusted issuer, the best thing we can do is not open it.
To conclude with the F-Secure report, it was found that companies received almost the same number of targeted attacks as opportunistic ones. Additionally, insider threats accounted for a fifth of security breaches, and the most common post-breach action was the spread of malware .
Simulators to see how these email attacks work
To provide an effective solution, people, processes, and technology elements must be included in the necessary cyber security measures. There is nothing better in these cases than knowing how we should face these situations. This prevents e-mail from becoming the weakest link in the security chain.
In this case, thanks to Keepnet Labs, I am going to introduce you to a series of simulators that will help you to be more prepared in these situations. We have the following:
- Phishing simulator that simulates phishing attacks in a benign environment, quantifies vulnerability and facilitates proactive response.
- A conscience educator that will allow us to obtain a cyber security awareness training.
- Email threat simulator : check your firewall, antispam and antivirus. In addition, using logic, it will offer a simulation of an attack directed at a company like yours, through your email services.
- Cyber threat intelligence – Scans the web for signals and data that may represent a breach of your data security.
- Incident responder – Allows the user to report suspicious emails with a single click, via an Outlook plugin, and sends the email content to the Keepnet Labs email scanner.
Prevents email from becoming the weak link in security
To finish, from this article we are going to offer you a series of tips that can help you a lot.
The first thing we have to do is be very careful with suspicious emails . If you do not know the sender, it is best not to open it, and if you do, never run or download any attachment that contains that email.
Another important point to keep in mind is that we must use strong passwords . Here I recommend forgetting to use only numbers or letters. Even a combination of both may be insufficient. The best passwords are made up of a combination of all these factors:
- Must include numbers.
- Also letters, but also must include upper and lower case.
- In addition, we must introduce less common symbols such as: @ # € ¬ ”$.
You can access our complete tutorial on how to create strong passwords for all your services. When in doubt, send that email to the trash. If you need it, the mail managers usually give 30 days to recover them. Finally, if you detect any cyber fraud either from phishing or through an e-mail, report it to the Police.