pfSense is a firewall-oriented operating system that also acts as a professional router, since we will have hundreds of advanced configuration options, and even the possibility of installing additional software to further expand its functionalities. If you’ve ever wanted to try pfSense, but don’t know where to start, today in this article we are going to show you how to configure the Internet connection, how to create VLANs to segment traffic, configure the DHCP server with its corresponding Static DHCP, and even configure the DNS server, UPnP and also to open ports in NAT (Port forwarding).

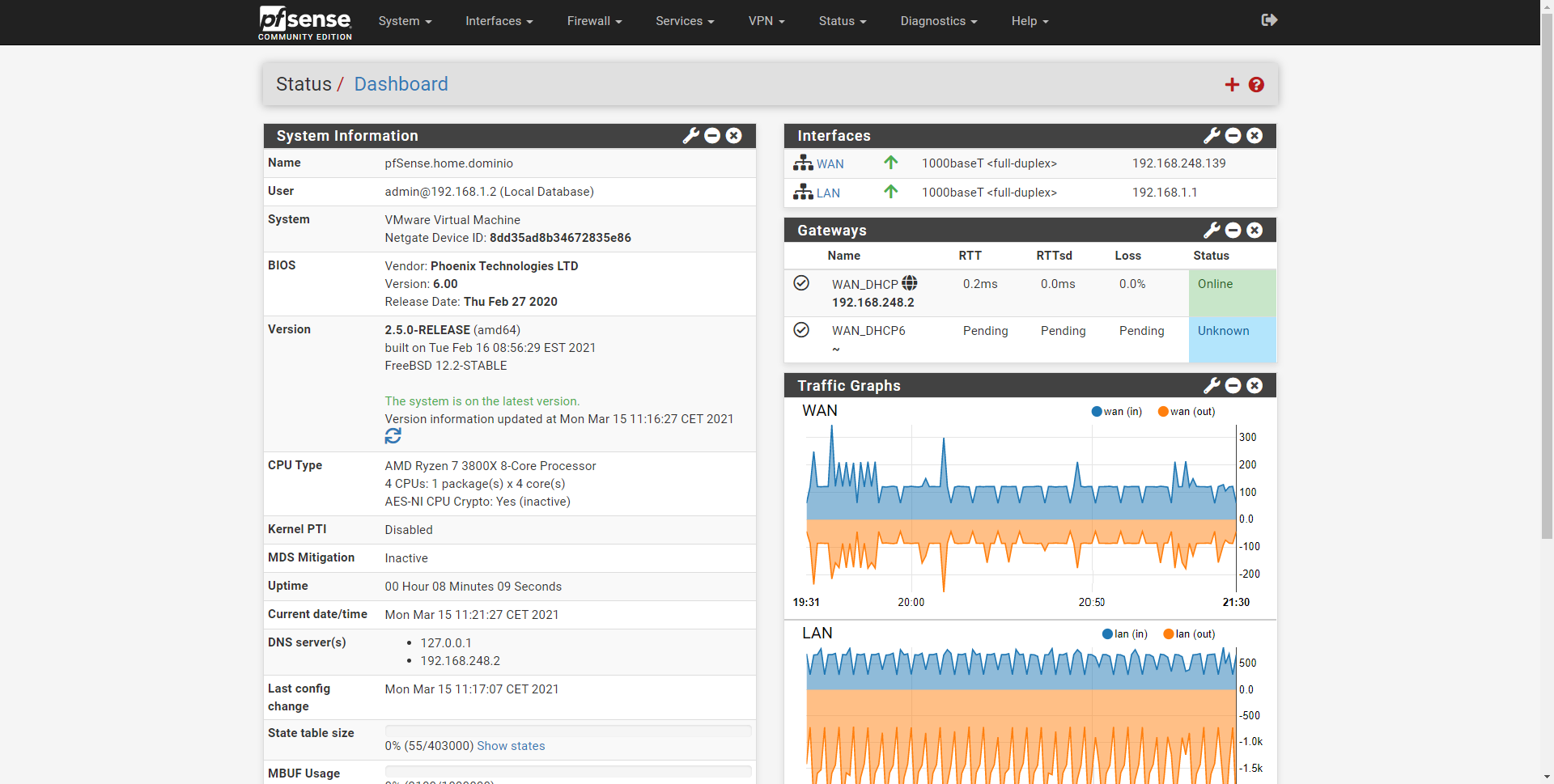
The first thing we have to do is enter pfSense with the default gateway. By default, we have two interfaces with the following configuration:
- WAN: configured as DHCP client without VLANs or any additional configuration. Access to the administration is not allowed by default.
- LAN: configured with 192.168.1.1/24 and with DHCP enabled. Access to administration is allowed by default.
Therefore, to access the firewall and router administration, we must put https://192.168.1.1 in the address bar, the username is “admin” and the password is “pfsense”, thus we will directly access the configuration menu via the web, where we can see the following:
Set up internet connection
pfSense is designed to connect directly to the Internet and have the public IP address provided by the operator, it is very important to have a public IP and not be behind CGNAT, otherwise, we will not be able to do port forwarding or remotely access pfSense itself . In Spain, it is very common for FTTH operators to use different VLAN IDs to provide their connection to the Internet. On some occasions, such as Movistar / O2, we can put the router in single-user position and configure only the PPPoE, but on other occasions, such as Grupo Masmovil, we must configure a VLAN ID in the Internet WAN to work, otherwise, we will not have a connection to Internet.
If your operator needs to use a VLAN ID, in pfSense we must follow the steps detailed below, if you don’t need VLANs, you can skip this step:
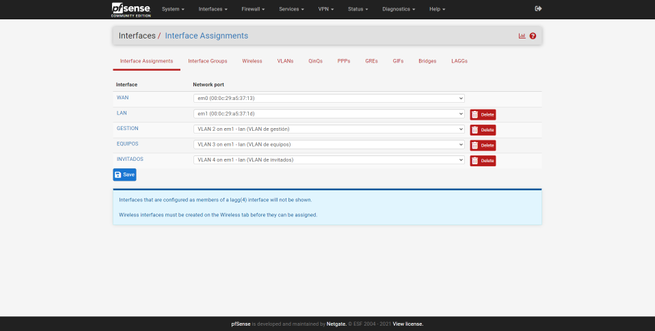
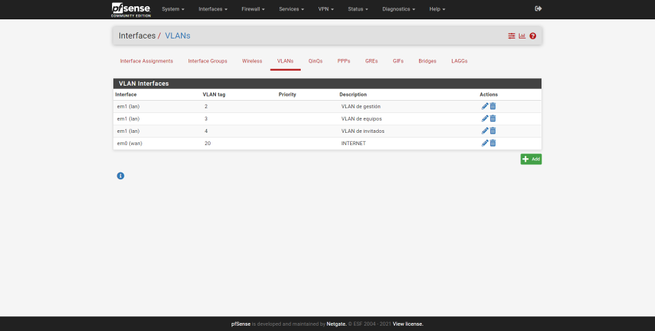
- Go to « Interfaces / Interface Assignments «, in the «VLANs» tab is where we will have to create them.
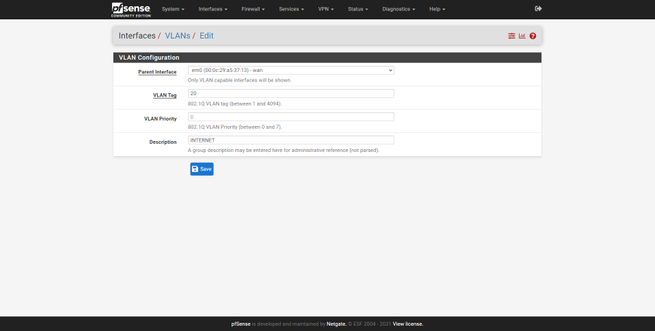
- Parent Interface : make sure we choose the port assigned to the Internet WAN, not the LAN.
- VLAN Tag : Create the VLAN ID that corresponds to the Internet connection, in Movistar / O2 it is 6, in Indirect Masmovil Group it is VLAN ID 20, this depends on each operator.
- VLAN Priority : we can leave it empty.
- Description : we put a descriptive name, for example, “Internet”.
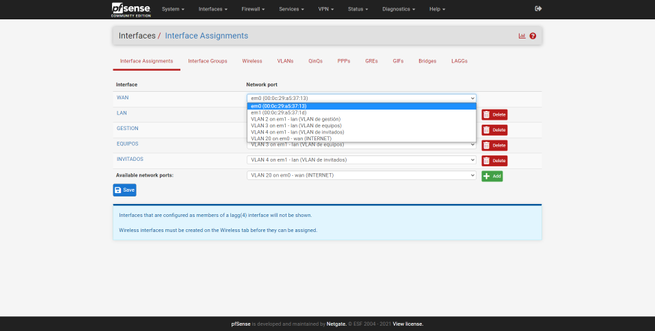
Once we have created the VLAN, we have to apply it on the Internet WAN. We return to the Interfaces / Interface Assignments menu and in the WAN section, we select “VLAN 20 on em0”, that is, the VLAN that we have just created. Once done, click on “Save” to save the changes.
Now we will have to go to ” Interfaces / WAN ” and perform the configuration provided by the operator, for example, Grupo Masmovil uses DHCP, but Movistar / O2 uses PPPoE. Depending on the operator we will have one type of connection or another, a username / password or another, but all the options for the WAN are in this section. It is highly recommended to check the two boxes at the bottom, both “Block private networks and loopback addresses” and “Block bogon networks”, to put rules in the firewall blocking these networks on the Internet WAN.
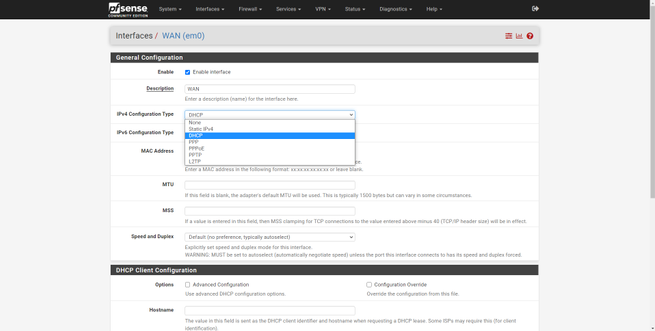
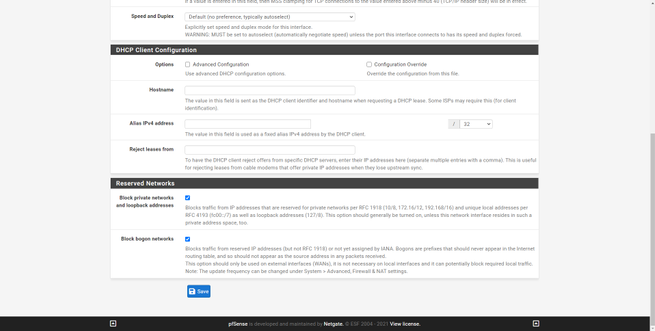
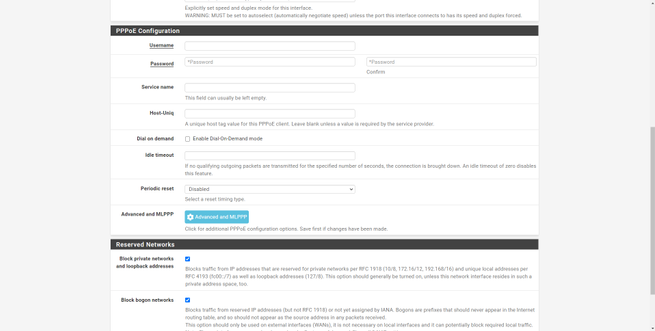
At this point, we should already have an Internet connection without problems, obtaining the public IP of the operator and the DNS servers that they provide us at the network level.
Create VLANs to segment traffic
VLANs (Virtual LAN) allow us to separate the traffic of different networks to increase the security of the network, we can create several VLANs to separate the networks and have different levels of permissions and accesses in each local network created. A typical network architecture consists of having all the VLANs created in the pfSense, and connecting a cable from a physical port of the LAN to a port of a manageable switch in trunk mode, in this way, we will be passing all the VLANs to them (with label) created in the switch to pfSense to do inter-vlan routing, and also to have the possibility of configuring different rules.
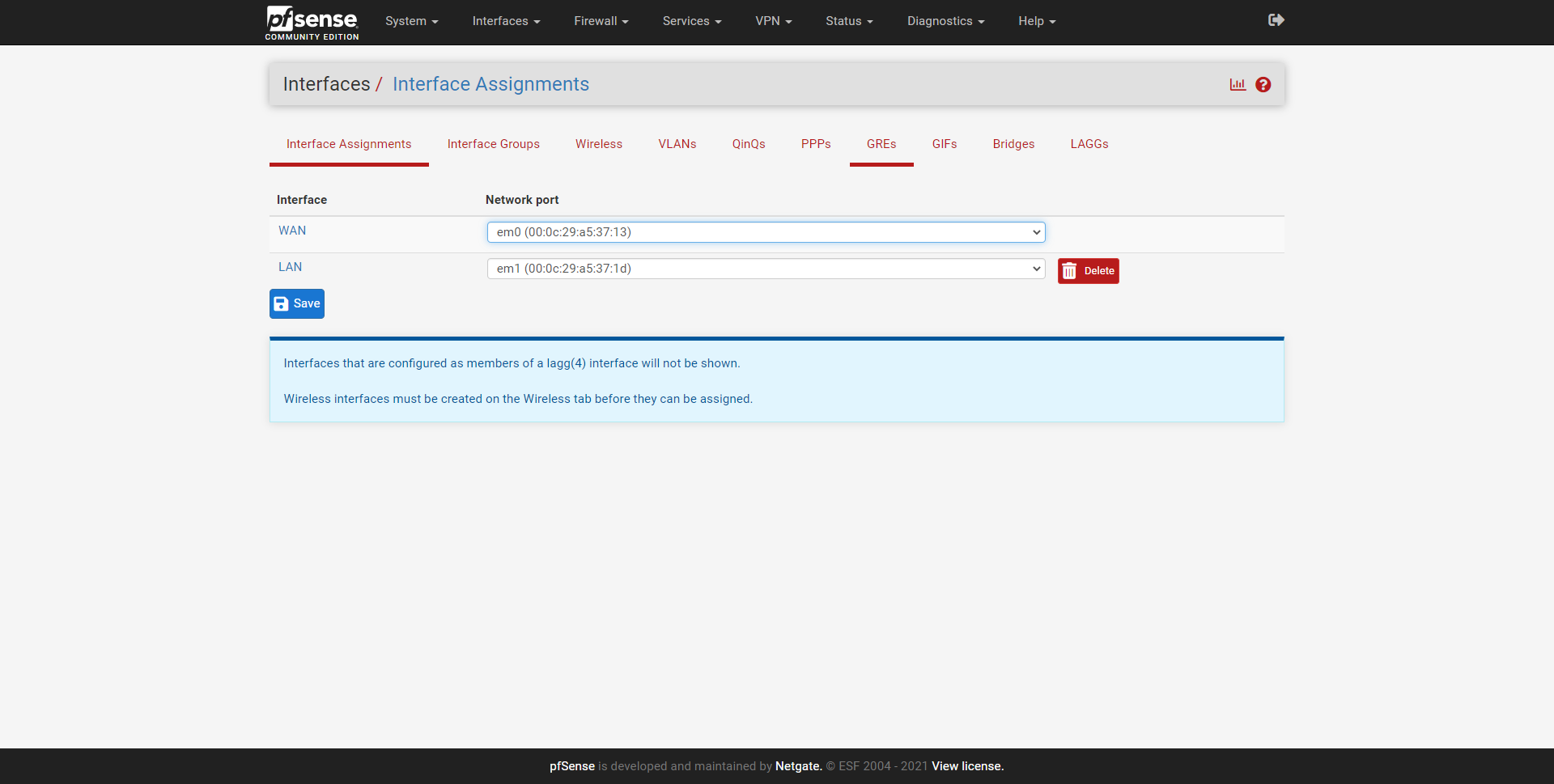
The first thing we have to do to create VLANs on the LAN is to go to the ” Interfaces / Interface Assignments ” section.
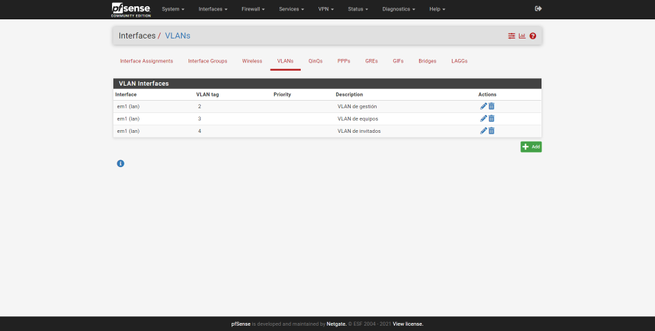
Once here, we click on the VLANs section to create them correctly, by default we do not have any VLANs created, as you can see below:
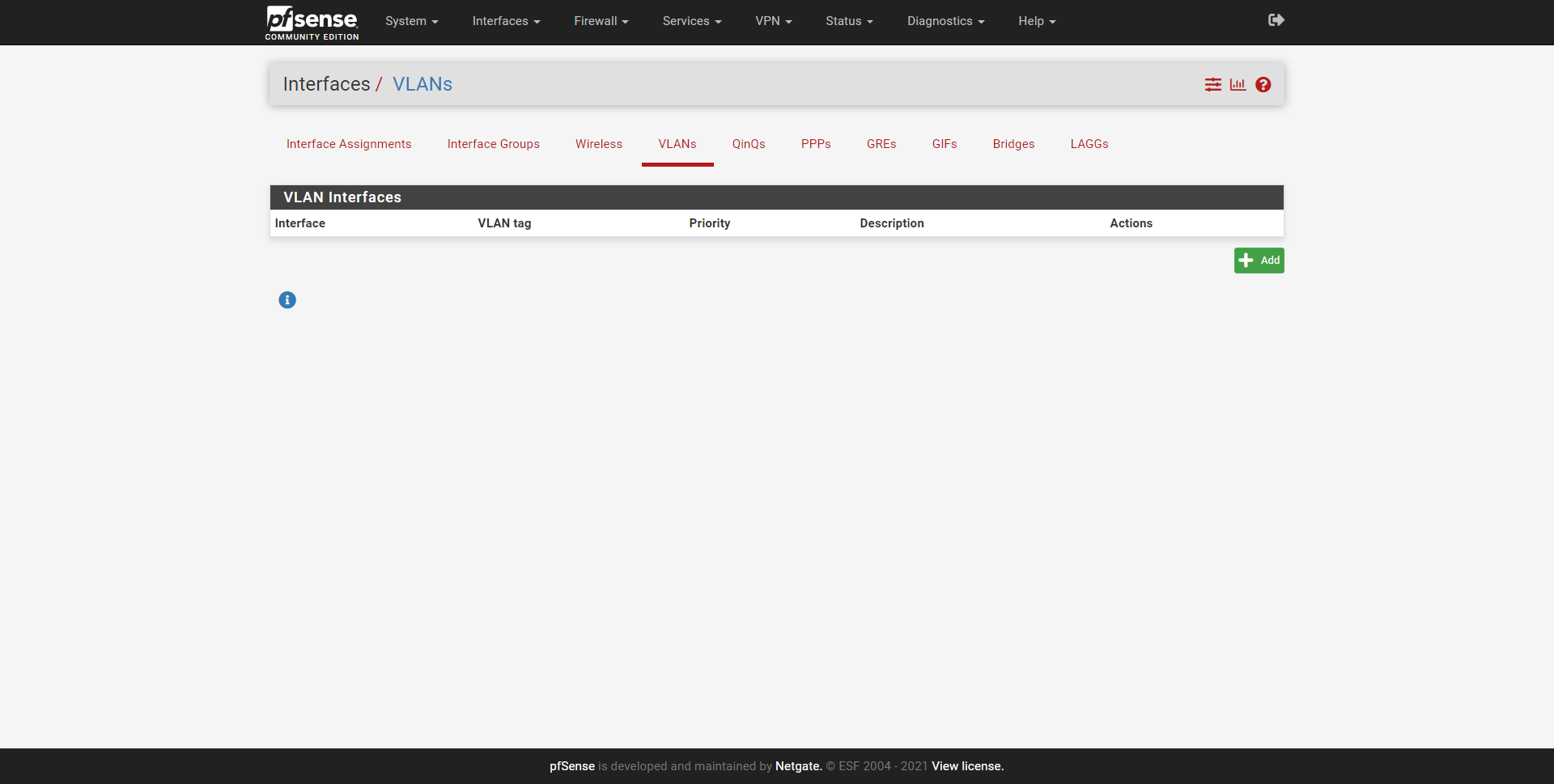
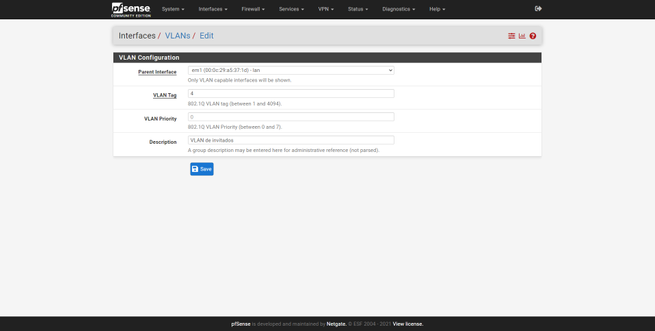
To create a new VLAN, click on «Add», and then carry out the following steps:
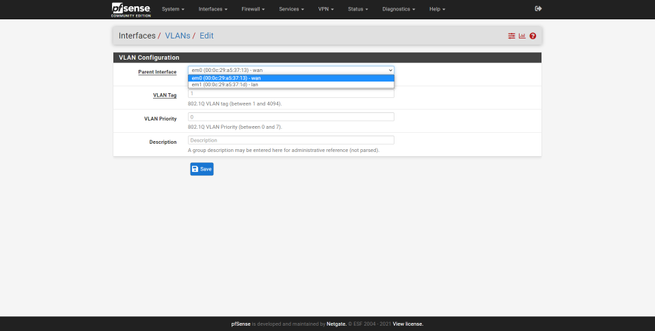
- Parent Interface : make sure we choose the port assigned to the LAN (not to the Internet WAN).
- VLAN Tag : Create the VLAN ID that corresponds to that of the switch.
- VLAN Priority : we can leave it empty.
- Description : we put a descriptive name, for example, «Management».
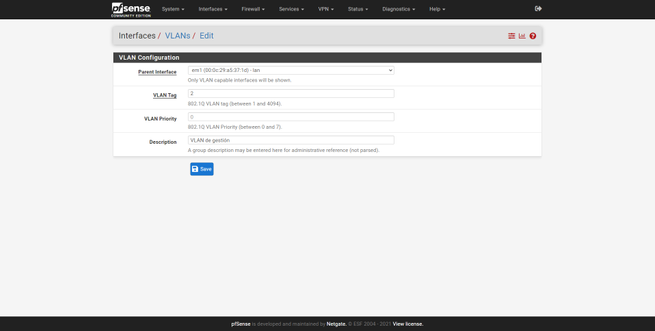
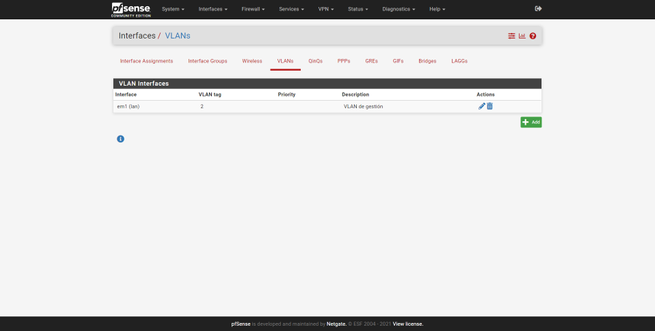
We can create all the VLANs we want, always “hanging” on the physical LAN interface. For example, we have created two additional VLANs, one VLAN for teams and one for guests. The procedure is exactly the same:
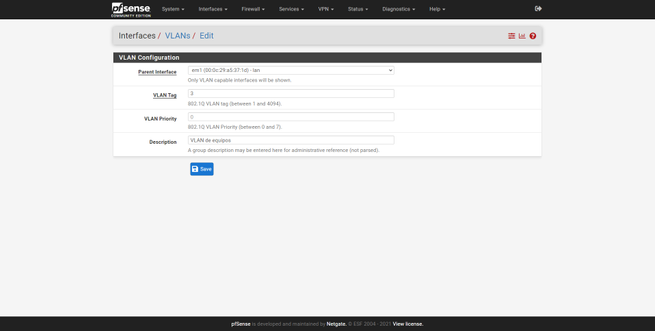
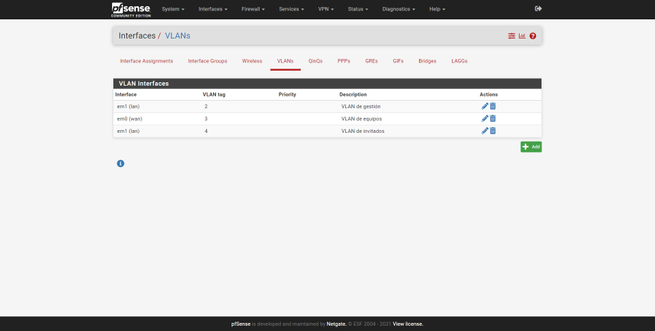
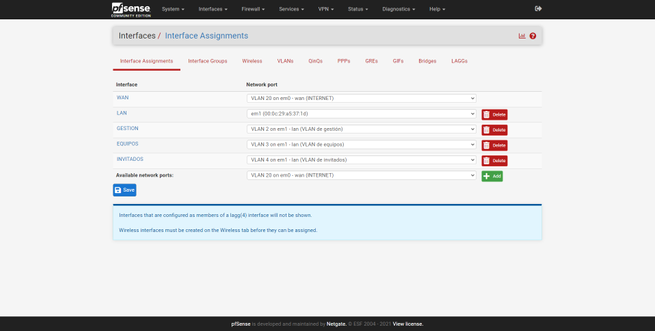
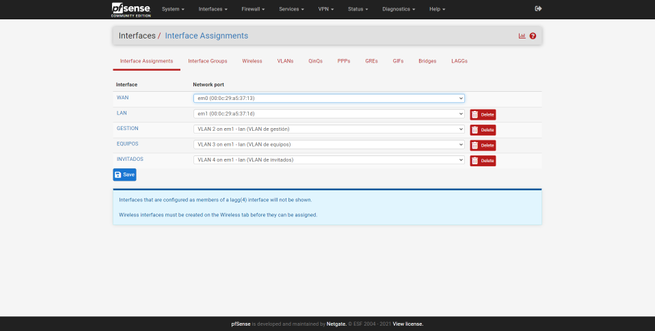
Once created, we will go back to « Interfaces / Interface Assignments «, here we can see a summary of the physical interfaces and the network port. By default, we will have the Internet WAN (with or without VLAN), and also the LAN. To add these new interfaces to the LAN, we simply select the «VLAN 2 on em1 …» interface and click on «Add», and the same with the others, as you can see in the following screenshots:
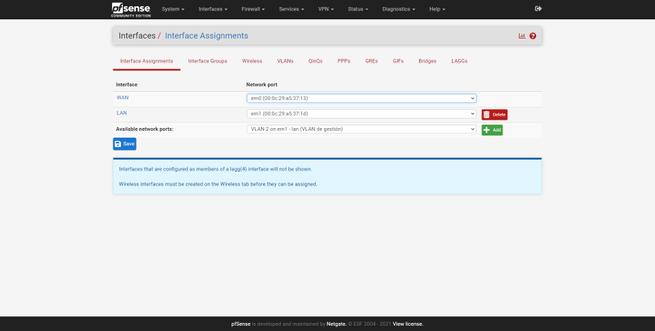
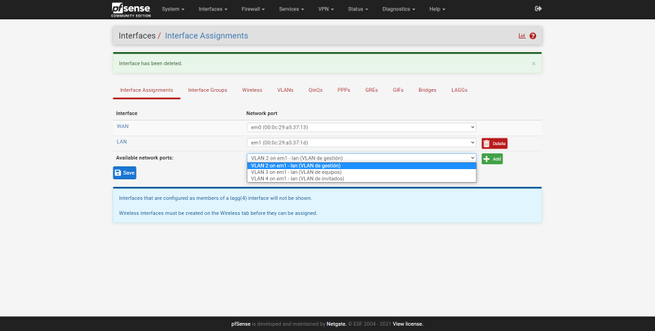
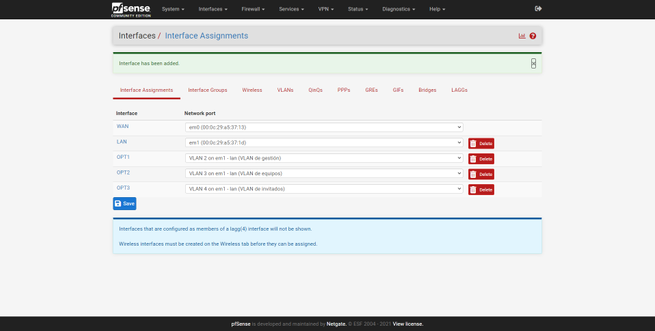
Once we have created them, all of them will appear in the “Interfaces” drop-down, with the default name being “OPT1”, “OPT2” and so on. By default, we have the LAN interface activated, with its corresponding private IPv4 address, based on this configuration, we can do the rest:
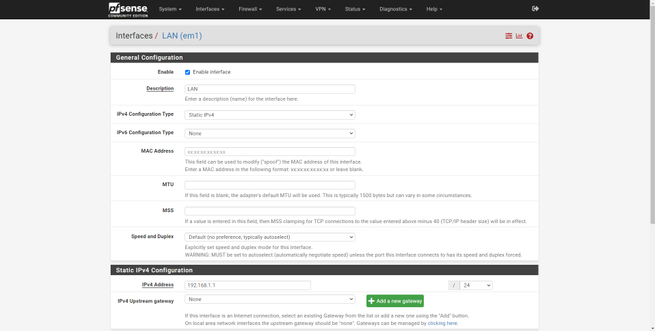
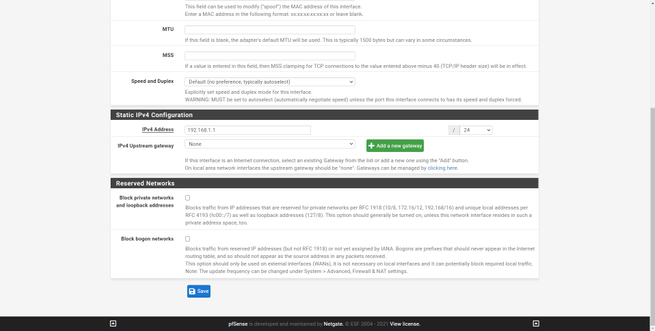
The configuration of the rest of the interfaces is exactly the same, we will have to enable it, put a descriptive name, put the corresponding IPv4 and / or IPv6 configuration, save changes and apply them.
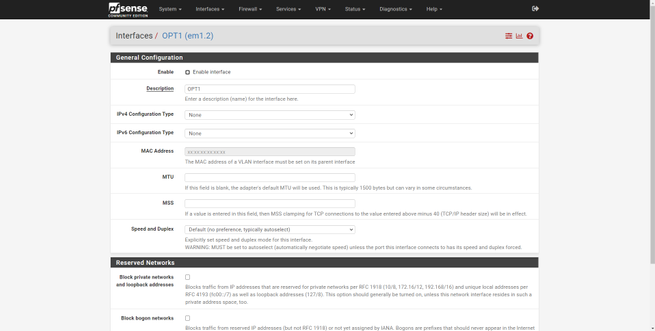
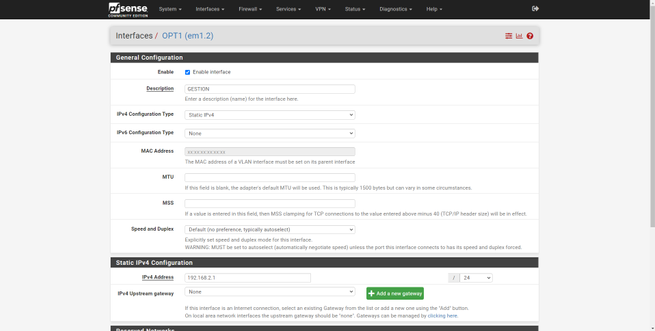
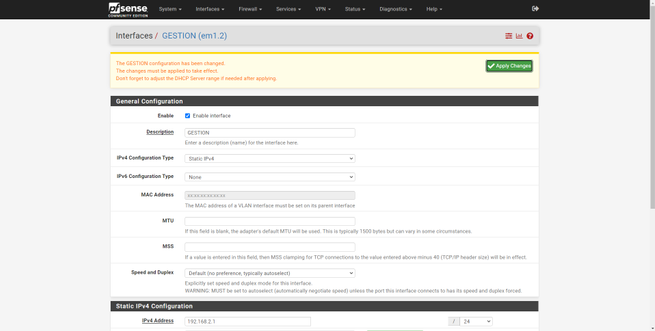
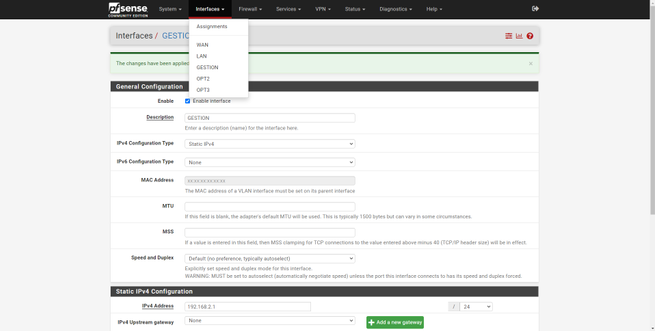
Once configured, we can see that now the name has been changed, we will have to do the same with the others. When we have finished, in the “Interface Assignments” section we will be able to see the name that we have given to each one of them.
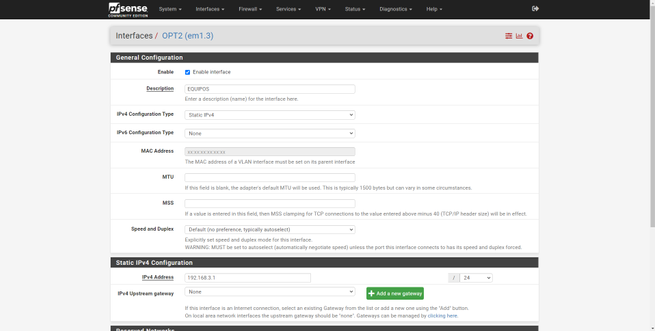
Now, when we connect different devices to the switch in a specific access VLAN, we can access this local subnet, but we must remember that the DHCP server is not yet activated in these newly created VLANs, it is exactly the next thing we are going to configure.
LAN interfaces DHCP server
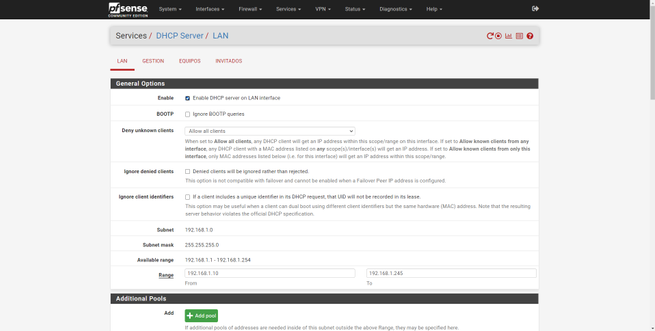
Normally each of the VLANs will have a DHCP server configured. To do this, we go to the “Services / DHCP Server” section. Just below we will have some tabs of LAN, management, teams and guests, the same networks that we have created previously. Here we can see the subnet to which each interface belongs, and what DHCP range we can provide at most.
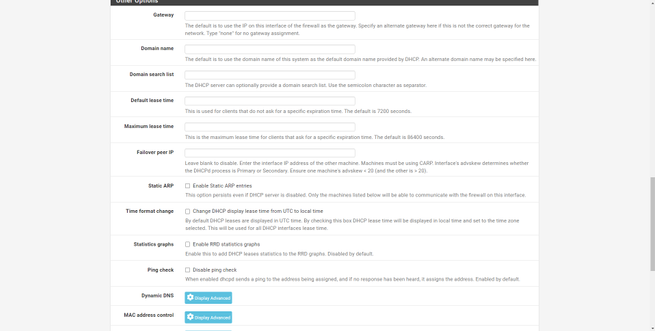
To configure the DHCP server, what we can do is put the same configuration as the LAN, changing only the subnet. In this way, we will make sure that everything works well. In these menus we can also add several “pools” and even define some WINS and DNS servers, we will also have advanced configuration options that we have right at the bottom.
The configuration options of the rest of the networks that we have just created are exactly the same as in the LAN, what we must take into account is to put a range within the same subnet, and that they have enough hosts for the network to work properly.
Static DHCP
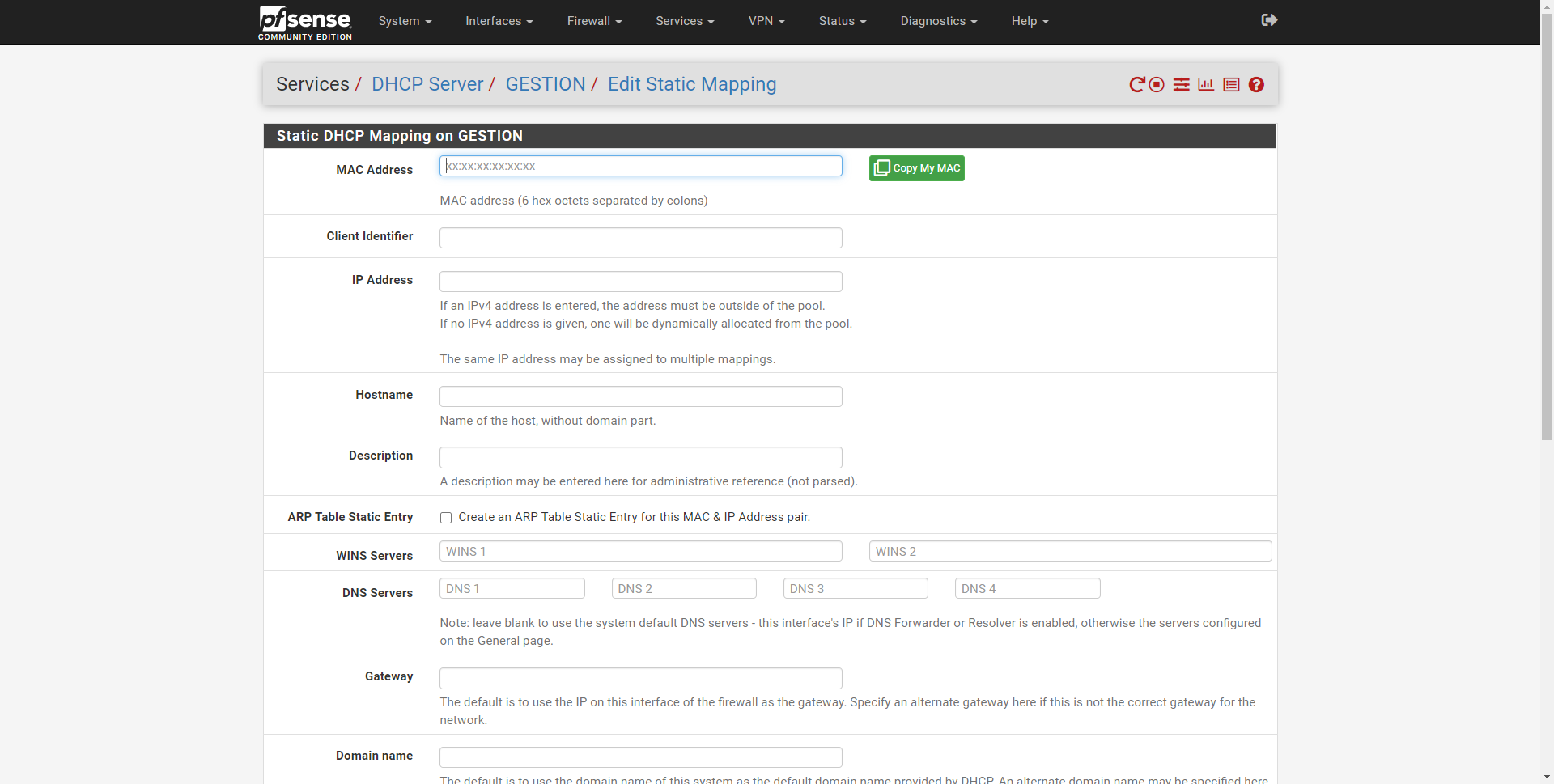
Static DHCP is the functionality of a DHCP server that allows us to provide the same private IP to the same network card. Putting the MAC address of the network card and the private IP that we want it to have, the DHCP server will always provide the same. In this section, the only thing that we will have to fill in is the following:
- MAC Address
- IP Address
- Hostname: to give it a name and access it via domain.
- Description: a descriptive name
- Click on «Create an ARP Table Static» to link the IP and MAC.
Next, we have the possibility to define WINS and DNS servers, as well as other parameters. If we leave everything blank, it will automatically inherit the configuration from the main pool, so we don’t have to worry.
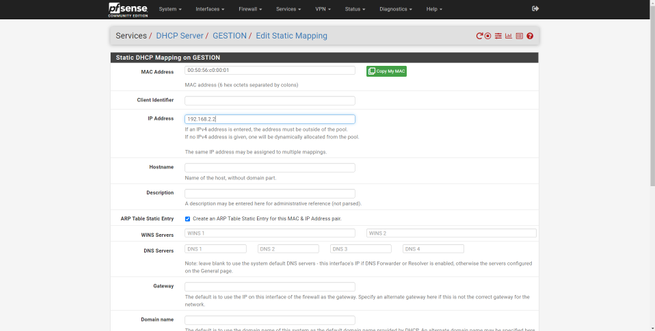
Next, you can see how to do it with our MAC of a PC and the IP that we want, it would be necessary to put the hostname and a description.
Configure DNS servers and DNS Resolver
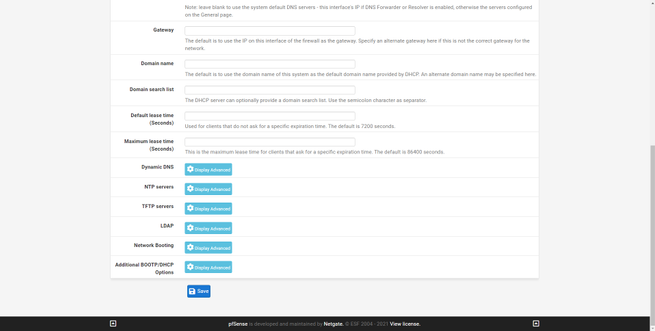
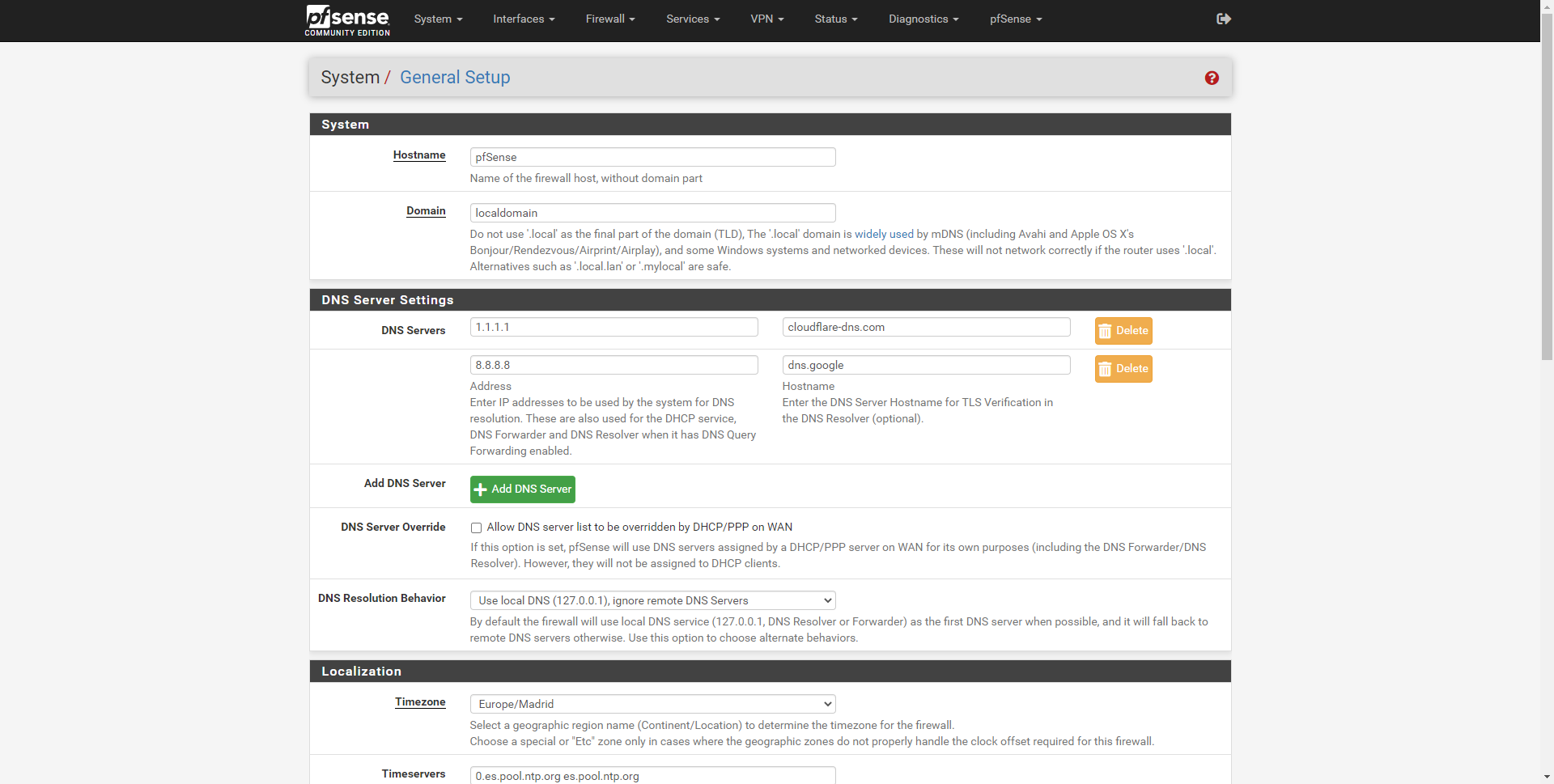
To configure the DNS servers, we have to go to « System / General Setup «, here we must incorporate the DNS servers that we want, one by one, by default there is a DNS server but we can add a secondary one. In addition, we can put the hostname of the DNS server for the TLS verification, as long as we want to have DNS over TLS in our pfSense.
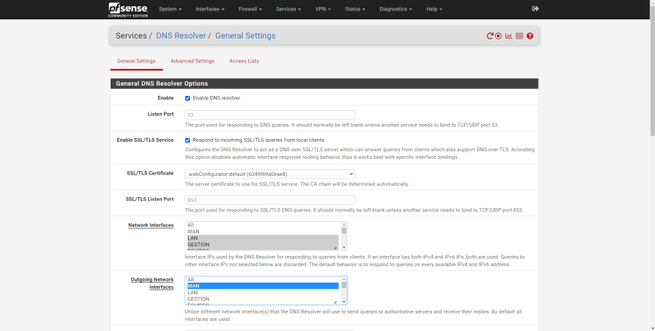
The most important thing comes in the “Service / DNS Resolver” section, here we enable it and allow clients to send us queries, although it is normal for clients to send queries through port 53 always, without SSL / TLS to no be that we have a client installed. The rest of the configuration options are to define where to “listen” to the clients’ requests, in the “Network interfaces” we choose only the ones we want, the LAN, management, teams, guests and the “localhost” so that pfSense itself can ask yourself about DNS.
We will also have to define the exit interface, in this case the WAN. The rest of the options are to enable DNSSEC support, enable the python module that is new to pfSense, and other advanced options. The normal thing is to have the option of “DNS Query Forwarding” deactivated, so that it is the DNS server of pfSense that solves the queries, and later use the DNS that we put.
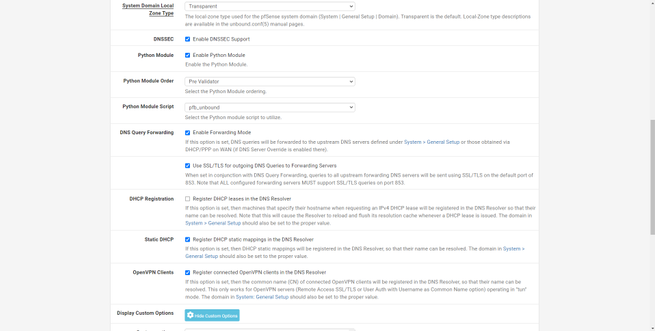
In the “advanced options” section we have the possibility to configure DNS over TLS, we can do it by adding these rules:
server:
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 1.1.1.1@853
forward-addr: 8.8.8.8@853
Then we have other options in the other tabs of the DNS resolver, in principle we should not touch them, but they will allow us to configure very advanced options related to the DNS server, and also create access control lists to use or not the DNS resolver.
Configure UPnP and NAT-PMP with security
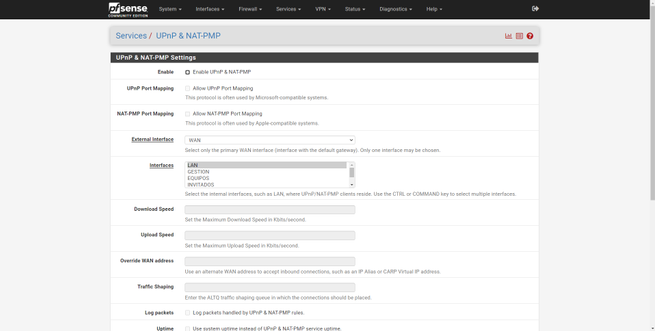
UPnP is a protocol that allows us to open ports in the pfSense firewall and router automatically, when a client requests such opening. This is a risk for the security of the network, because it is possible that a certain application opens a port that we have not requested. Regarding security, the best thing to do is to always disable the UPnP and NAT-PMP protocol.
In case you have to activate it yes or yes, it is advisable only to do it in the private IP addresses that are needed, and not in the entire network, in order to protect the rest of the devices that are connected.
Open ports in NAT (Port forwarding)
When we are in a NAT environment, you may need to open ports to access certain services from the outside. If you have a NAS server with an FTP, VPN or SSH server, and you want to access all these services from the outside, you will have to open different ports in the NAT to allow starting the connection. If you open ports in the NAT, but you have the CG-NAT of your operator, it will be of no use to you.
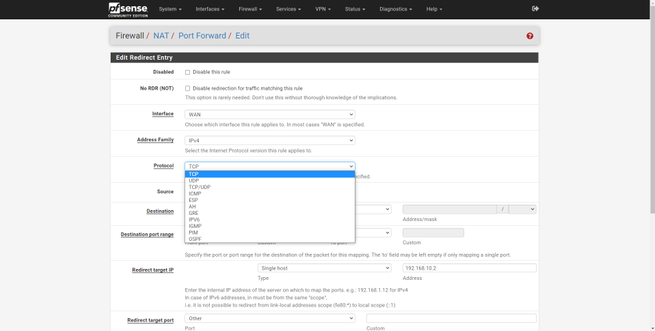
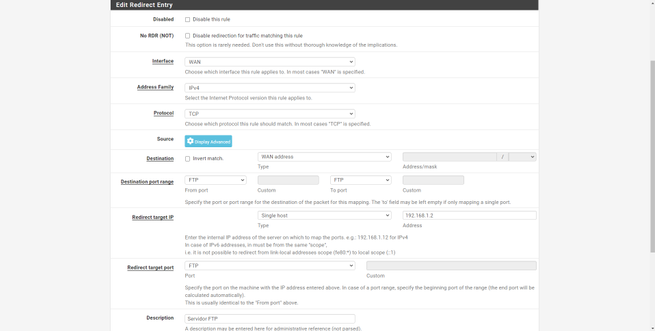
To open the NAT, the first thing we have to do is go to the “Firewall / NAT” section, and in the “Port forward” tab create a new rule.
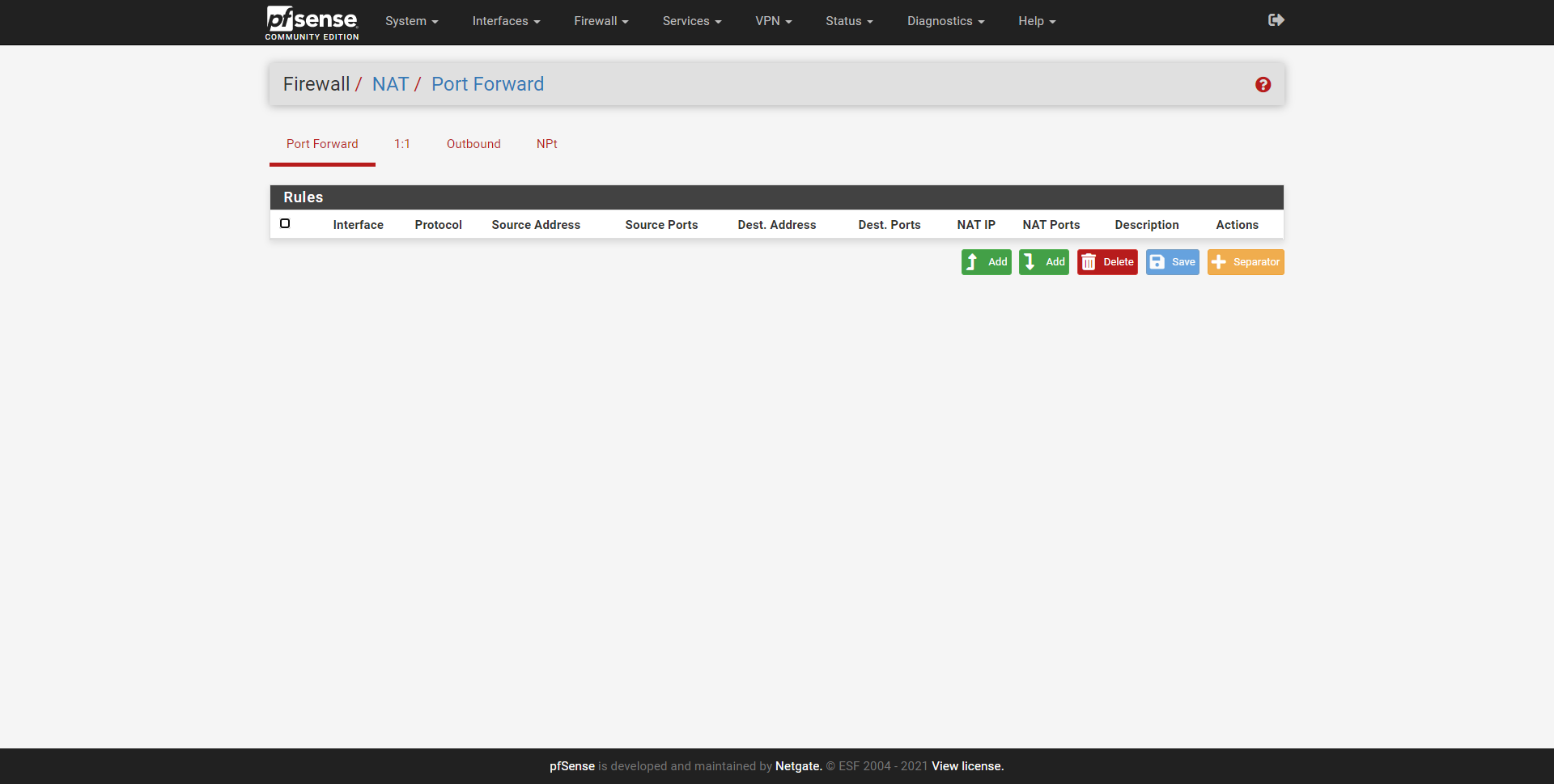
In this menu we will have different configuration options, but basically what we will have to fill in is the following:
- Interface : WAN
- Address Family : IPv4
- Protocol : we choose the protocol, in the example it is TCP
- Source: empty
- Destination : WAN Address
- Destination Port Range : We have to configure a range of ports or only one, if we want a range of ports, in the «From» we put a port, for example the 60000, and in the «To» we put the final port, the 61000. In the example we have opened port 51400.
- Redirect target IP : type Single host, Address the private IP address to which you want to open the port
- Redirect target port : it must be the same port as in “Destination Port Range”. This function allows us to have the 51400 open for the WAN, but internally we can “modify” it on the fly and use the 51500, for example.
In the following screenshots you can see how to do it:
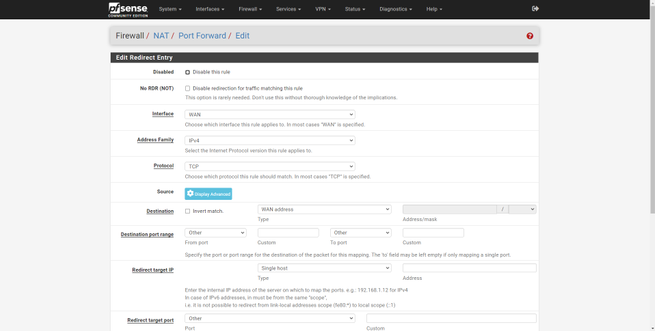
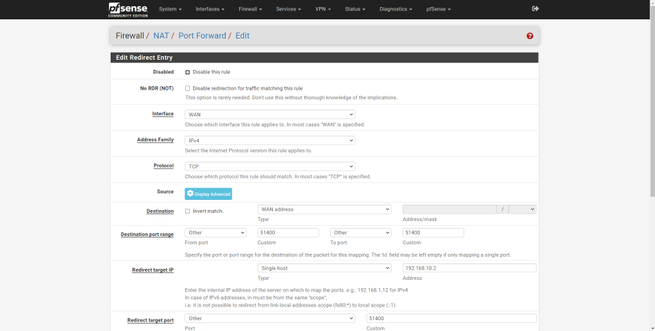
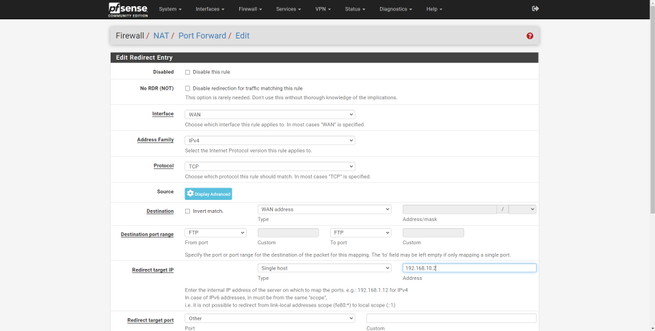
pfSense allows us to use a large number of protocols, TCP, UDP, both, ICMP and many others. The most normal thing is to open TCP or UDP ports, but we can also open many more types of protocols.
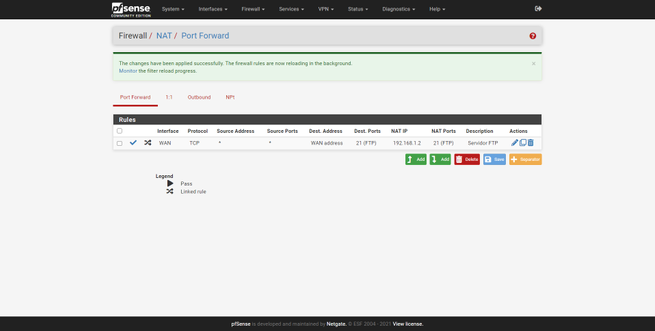
Once we have configured it, we will see it in the ” Firewall / NAT / Port Forward ” table, we must also make sure that the NAT is done correctly, in “Outbound” we can verify it. Right now we will be “swimming” all the subnets created. Finally, we must check that in « Firewall / Rules » and in the WAN tab there is the rule that we have created in the NAT, the order of this rule is very important, if, for example, we have a «deny all» above after permission rules, this new rule will be placed at the bottom, and we must reorder it.
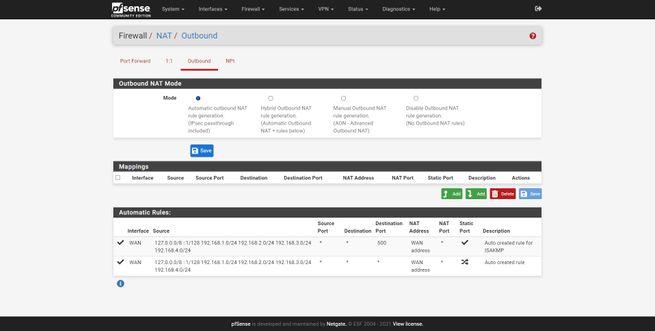
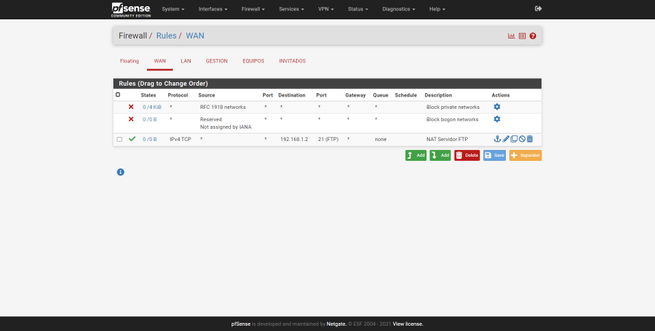
We must remember that the rules are analyzed in series, from top to bottom, if we put a very general rule at the top, and the more specific ones at the bottom, the latter will never be satisfied, because previously a more general rule has been met.
Configure rules on the firewall
The rules that we create in the pfSense firewall is the most important part to correctly segment the network, and allow or deny certain network traffic that flows through the different physical and logical interfaces that we have created. In the ” Firewall / Rules ” section we can see different tabs to create rules in the different interfaces, we have a total of five interfaces right now: WAN, LAN, Management, Teams, Guests.
We have an additional tab called “Floating”, these are special rules that affect one or more interfaces, and that are placed above the rules that we are going to define specifically in each of the interfaces. That is, the rules that we have in «Floating», if they affect an interface, will be verified before the rules that we are going to define specifically in the interface. These “Floating” rules can be activated in the input, output directions or both, the use of input and output filtering could be more complex, so you should review them well before applying them. For certain applications, the “Floating Rules” are very useful, such as for pfblocker-ng, although normally these “Floating” rules will not be used.
In the “Firewall / Rules / WAN” section we can see two predefined rules, which are activated by blocking the “private networks” and “bogon networks”, as we have explained previously. The third rule is the opening of ports that we have made.
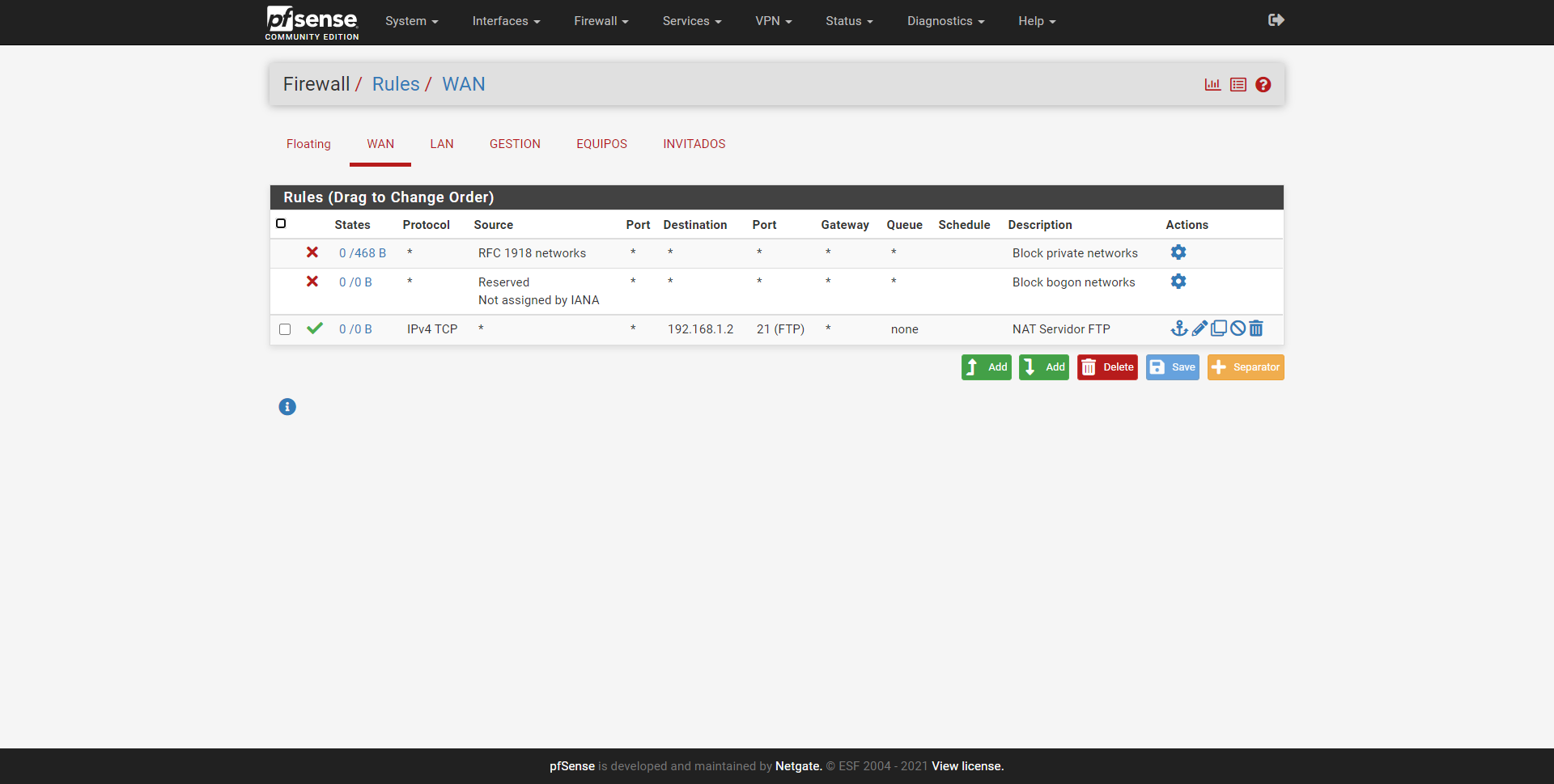
In the LAN we also have predefined rules, basically we will have a rule that prevents us from blocking ourselves to access the pfSense administration web interface, if we had the SSH server activated, a rule would also be incorporated here to allow access to the port of SSH. Next, we have permission to access anywhere from the LAN, both with IPv4 and IPv6.
We must remember that the rules are verified from top to bottom, if at the top we put a “block all”, we will automatically go offline.
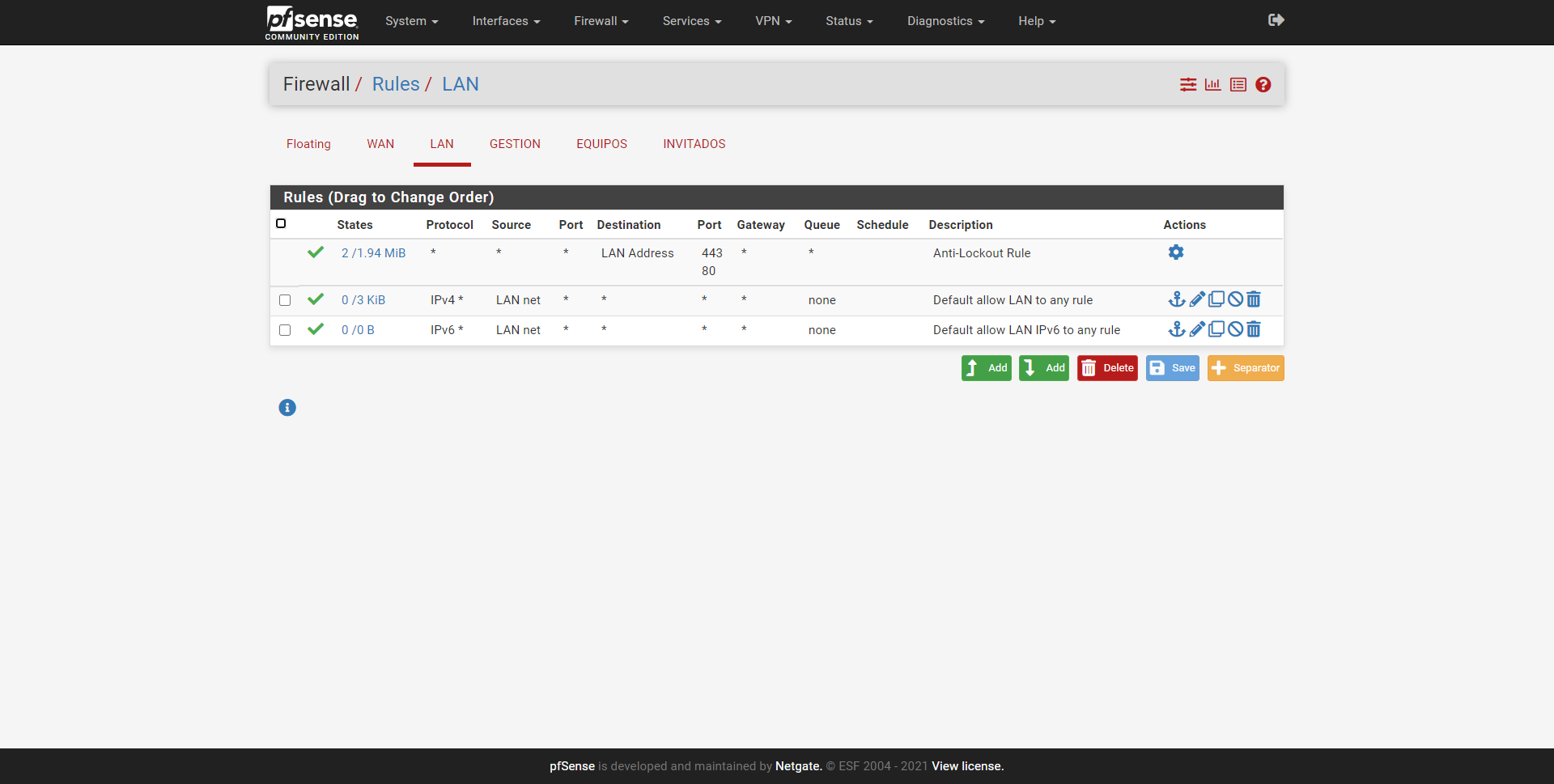
The rest of the networks that we have configured with their corresponding VLANs are completely empty. If you are empty, that means that we have an implicit deny all, that is, we will have to incorporate an allow rule to let network traffic pass.
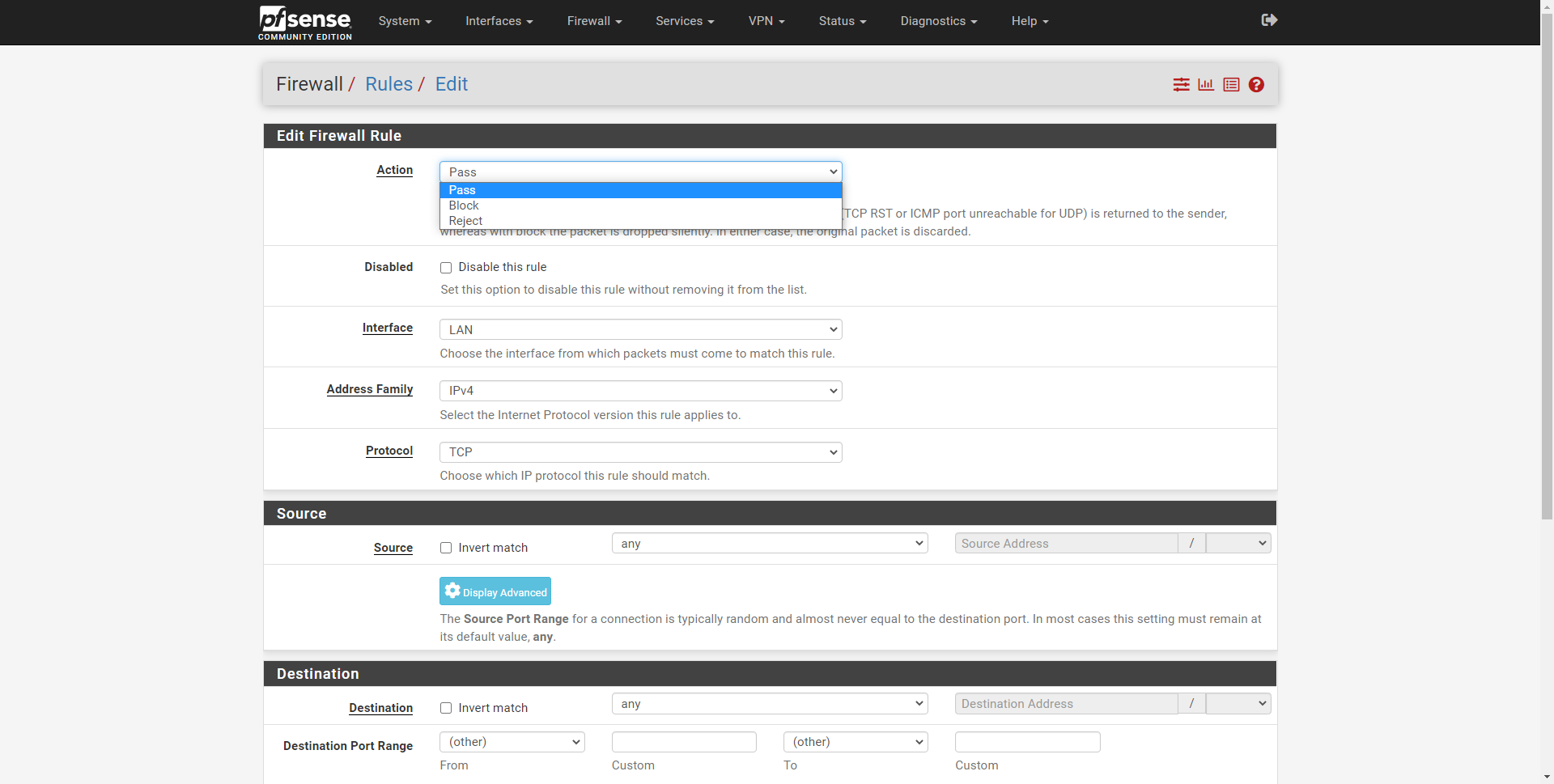
The graphical user interface to create a rule is the same for all interfaces, in the upper part we can configure different aspects of this rule that we are going to create from scratch:
- Action : if we want to allow (pass) the traffic, block it, or reject it (reject). It is the first thing that we must define, if this rule is applied and it is verified, the firewall will act accordingly.
- Disabled : allows disabling a created rule, this should not be touched if we want the rule to work.
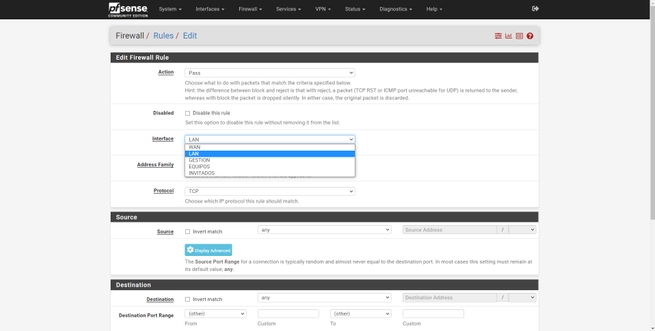
- Interface : we choose the physical or logical interface where we want to apply this rule.
- Address Family : we select the protocol IPv4, IPv6 or both.
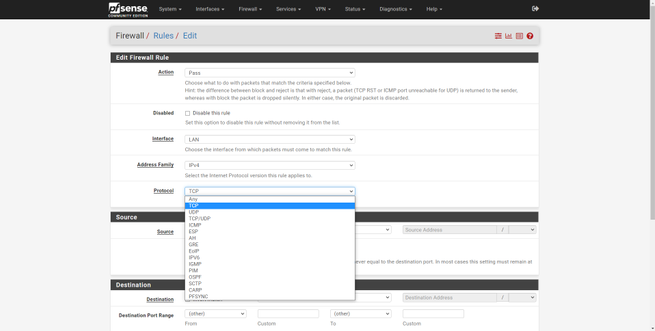
- Protocol : here we will have a list of all the protocols that we can allow or block, such as TCP, UDP, TCP and UDP, ESP, OSPF and much more.
In the following gallery you can see all the options for interface, address family and also for protocol.
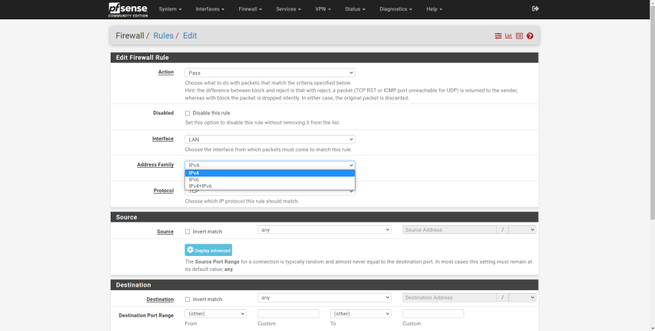
Once we have defined the above, now we will have to select the source of the traffic (Source). In this case we can choose any origin (any), or define a specific origin for a specific subnet, an individual host or an alias (we will explain what this is later). We can also choose as a source PPPoE clients, L2TP clients, or directly a network or IP address of the interface created.
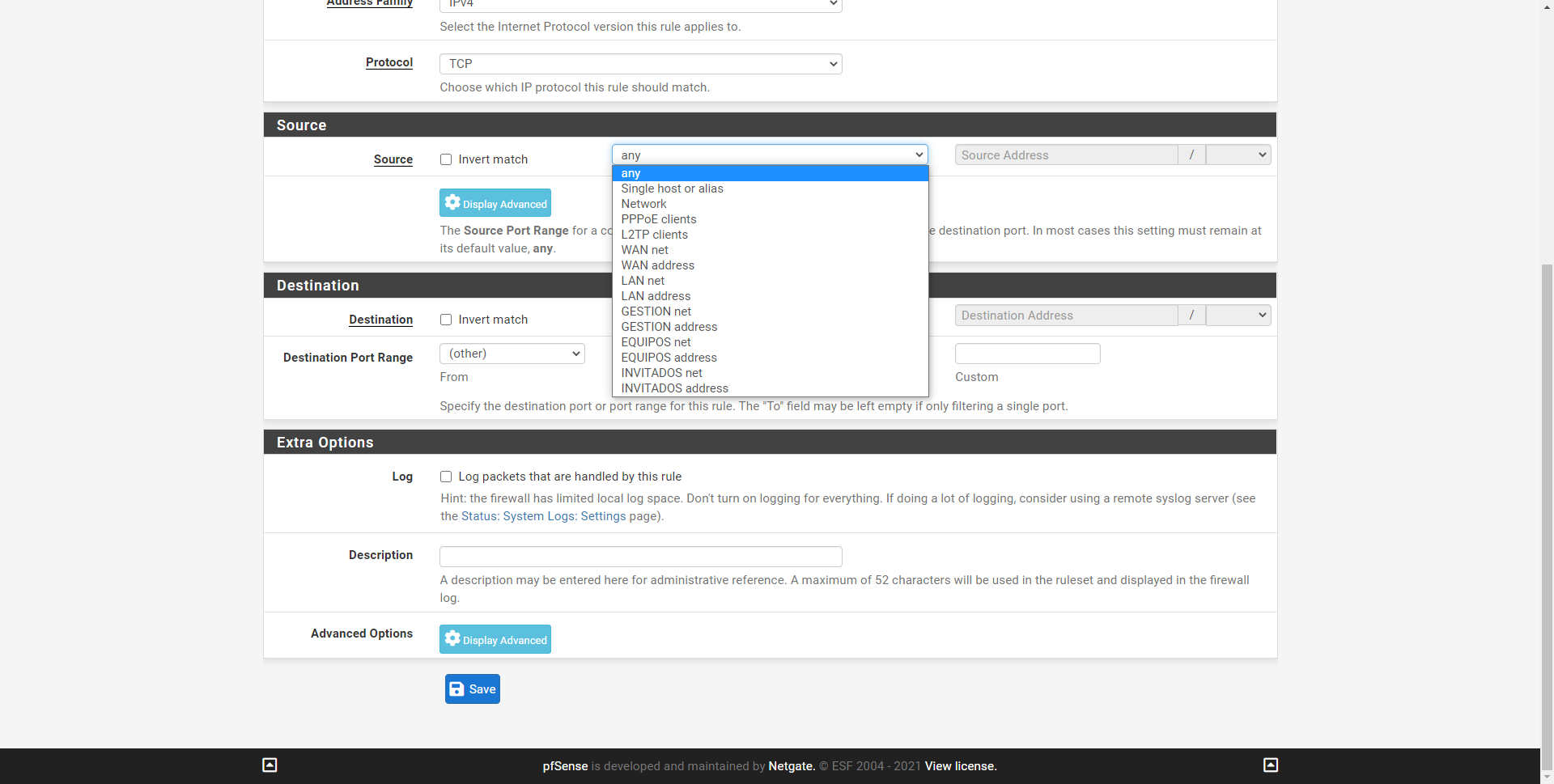
Exactly the same configuration options we will have in the «Destination» section, we can choose any one, an individual host, aliases, or the different networks that we have available.
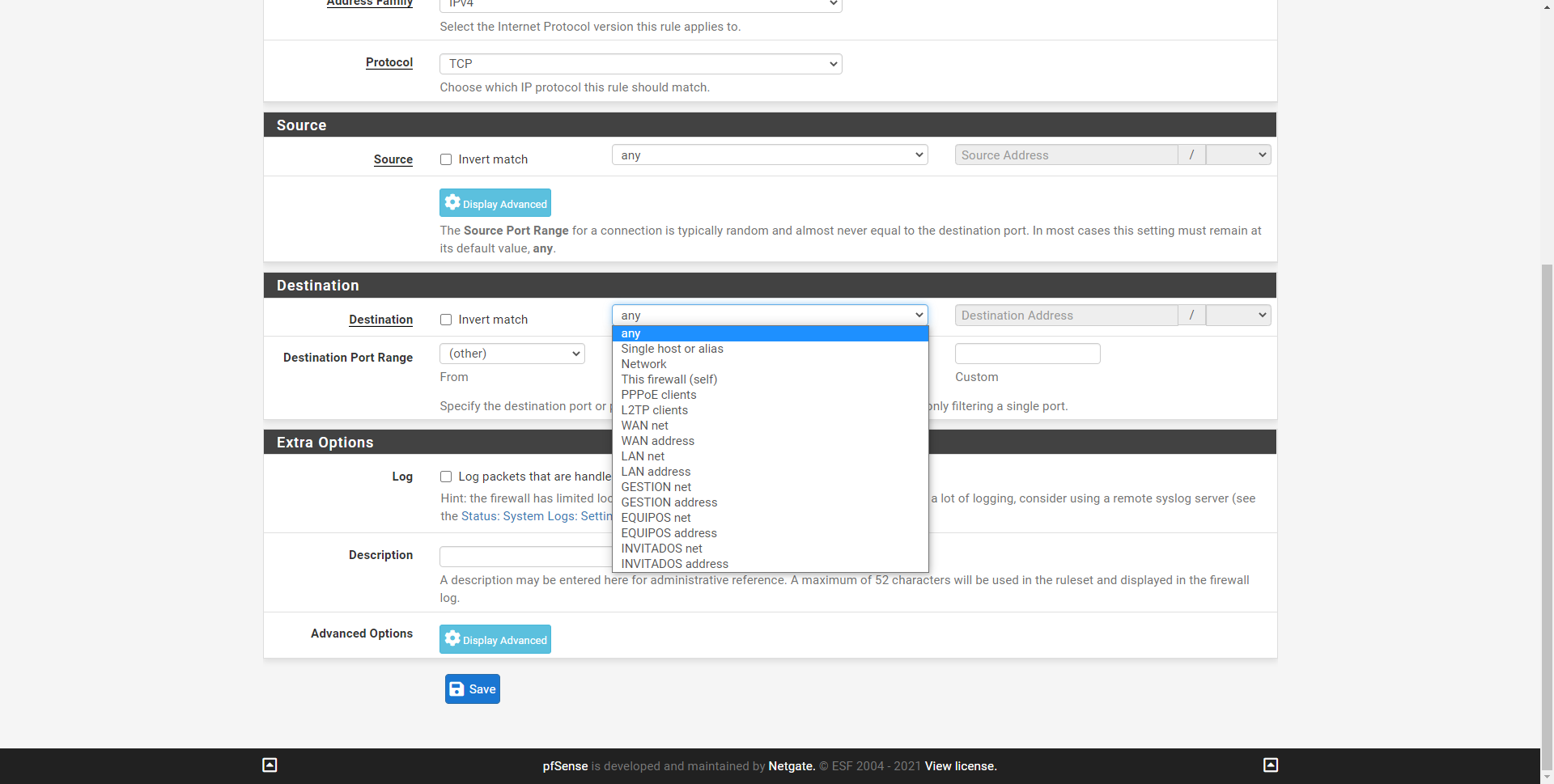
If we click on the “Source” section in “Display Advanced” we can see that we also have the possibility of filtering by port origin, providing a single port with a range of ports.
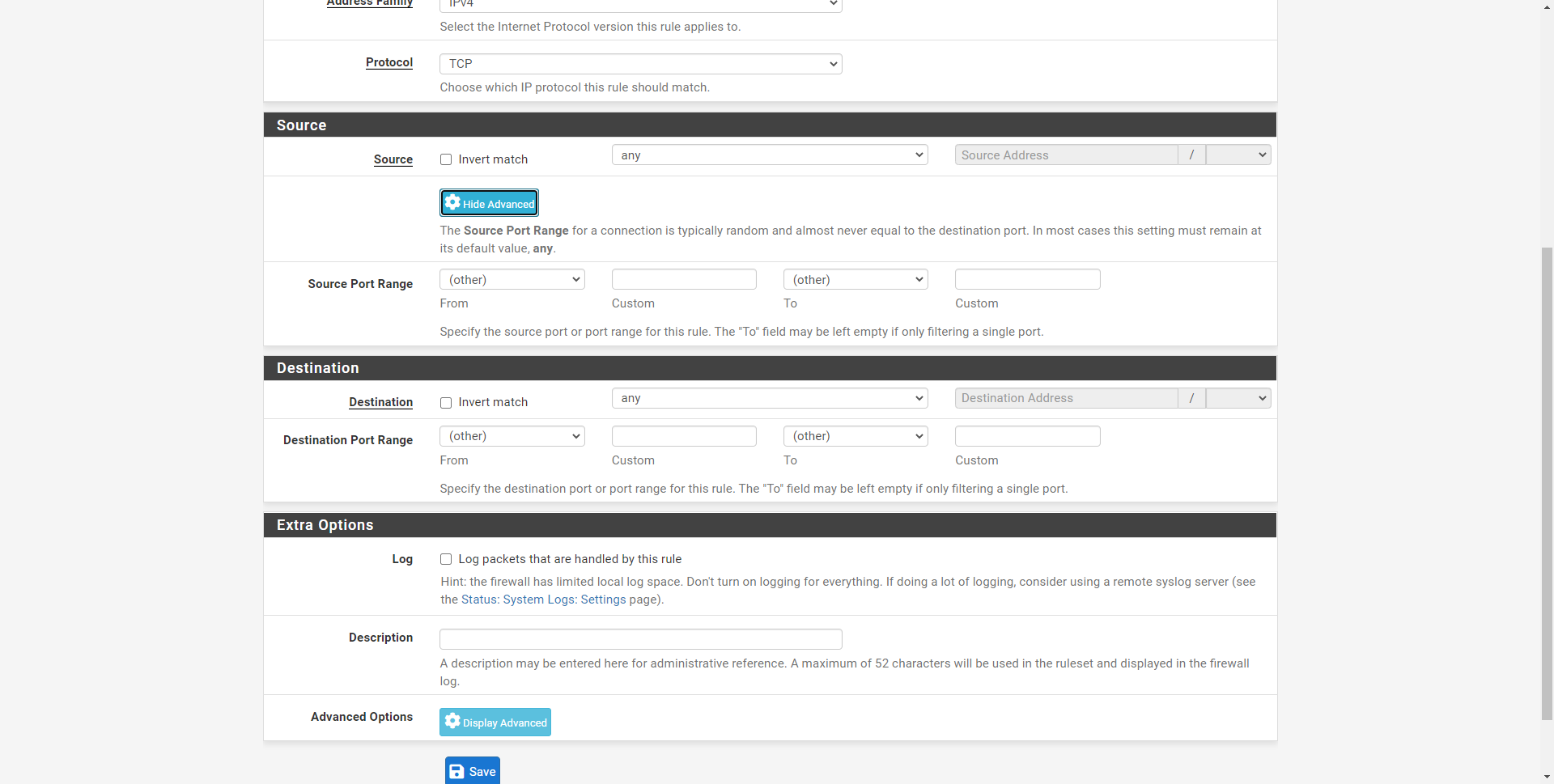
If in the “Protocol” section we choose the TCP protocol or another, and click on “Extra options / Advanced Options / Display Advanced” we will be able to see the advanced options of this specific protocol, to filter everything in detail.
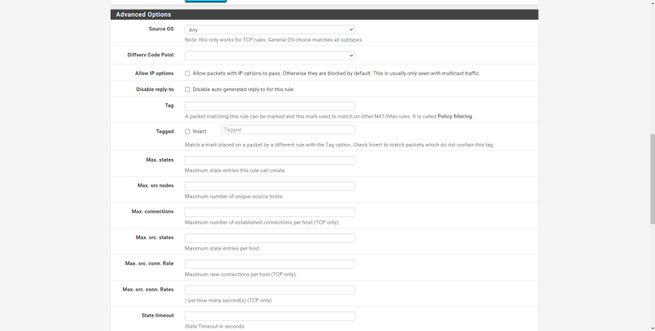
Once we have filled in everything, we will have to click on “Save”, and then on “Apply changes” in pfSense, as a green button will appear.
Aliases
Aliases are very useful for naming a set of IP addresses, subnets, or ports. This is ideal so that, with a single rule in the firewall, you can block multiple IP addresses automatically, without having to create 50 or more rules to block all IP addresses.
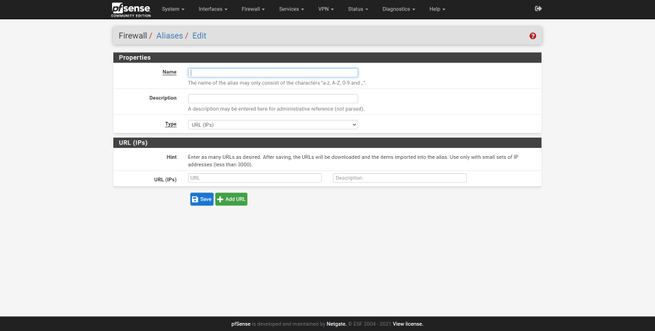
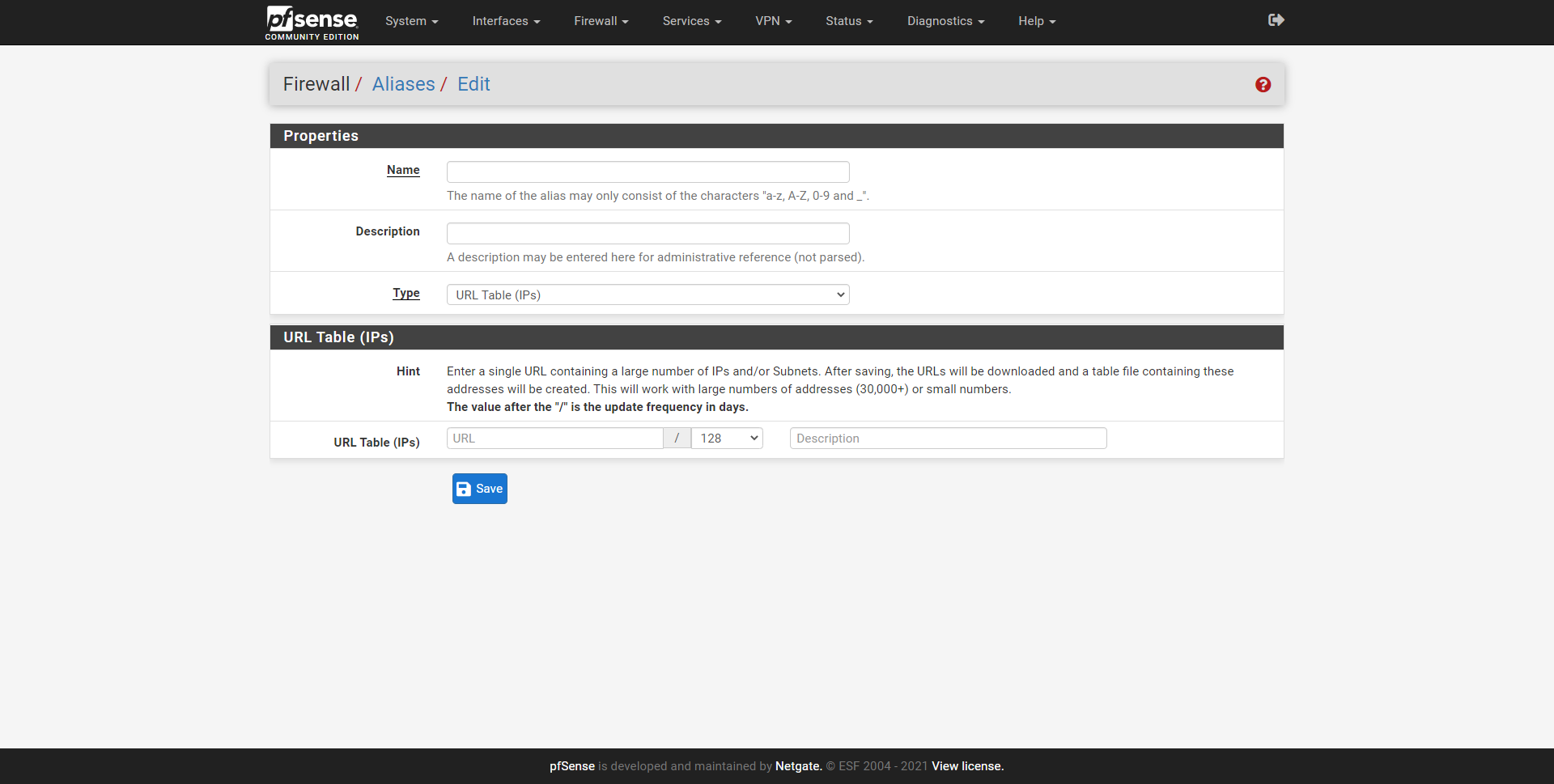
In the «Firewall / Aliases» section we can see the graphical user interface, we will have the possibility to add IP (hosts or networks), and also ports. In addition, in the URL section we can enter the address to a text file to automatically download hundreds or thousands of IP addresses, networks and ports to pfSense.
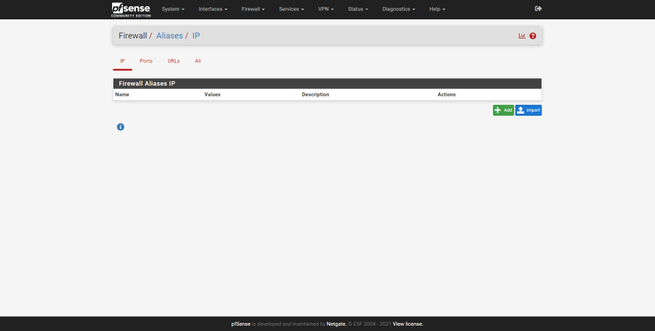
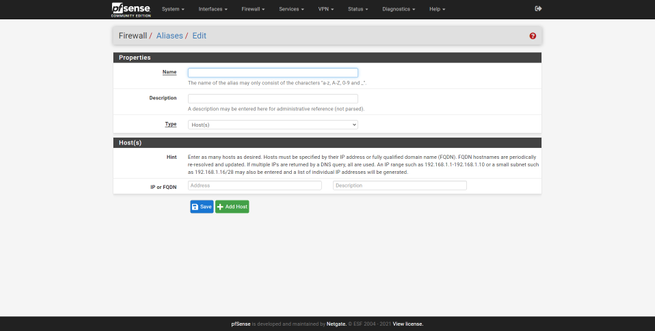
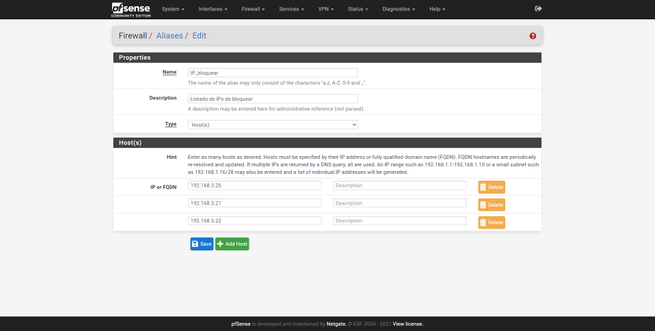
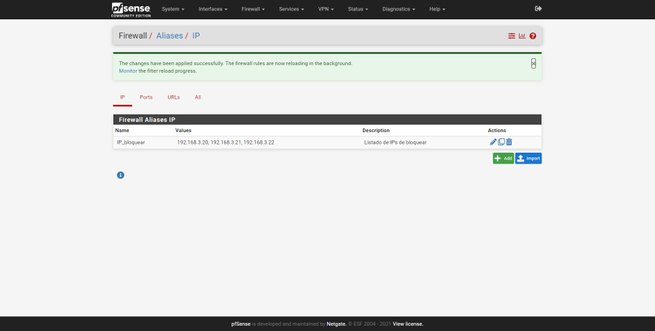
Let’s imagine that we want to create an alias called “Ip block”, with a list of IP addresses that we later want to block in the firewall. We enter the “IP” section, click on “add”, we give it a name, description and also a type. Then, just below we are entering the different IP addresses one by one, in addition, we can give it a description “Pepe’s computer”, to know which computer that IP corresponds to. Once created, it will appear in the list of IP aliases:
The same happens with ports, we can create an aliases to “block ports”, and define one or more ports that we will later block in the firewall.
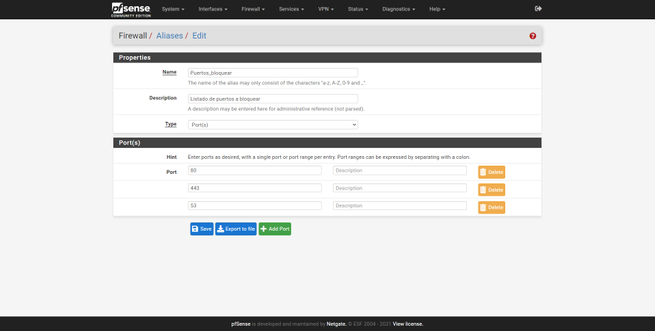
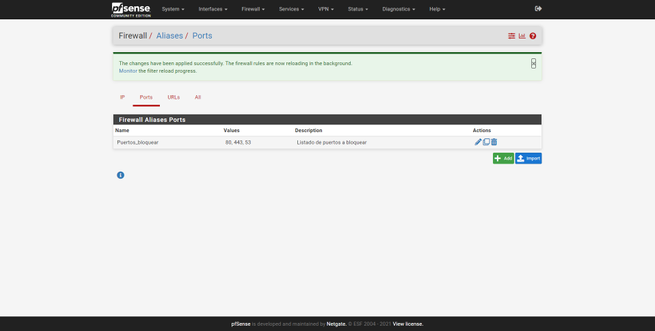
The graphical user interface of the URL would be as follows, and we must choose whatever type it is, IPs or ports.
Once we have the aliases created, just go to the “Firewall” section, and we can load it at source and / or destination, we choose the option “Single host or aliases”, and just to the right we write the name of the aliases that we have created, it will automatically recognize it and we will get a list of aliases that begin with the same letter that we have entered. And the same happens if we are going to configure ports, but here we will have to put it in the source and / or destination ports section.
As you have seen, using pfSense as a router and firewall in our house is really easy and fast, it is a very professional and complete operating system, but with this start-up guide we are sure that you can start with a good base on how to configure it. .