When we install a Linux server based on Debian, it is always highly recommended to perform a complete hardening to protect the operating system and all services as much as possible. With the passage of time, there are always new vulnerabilities in the different software that we have installed, and even in the Linux kernel itself. Thanks to a tool like Debsecan, we can completely scan our operating system, detecting the packages we have installed and the security flaws that have been found. Today in this article we are going to show you how to use it.
Installing Debsecan on Debian
This tool is not installed by default in the operating system, therefore, we must install it manually through the official repositories of the distribution. To install it, we must execute the following command:

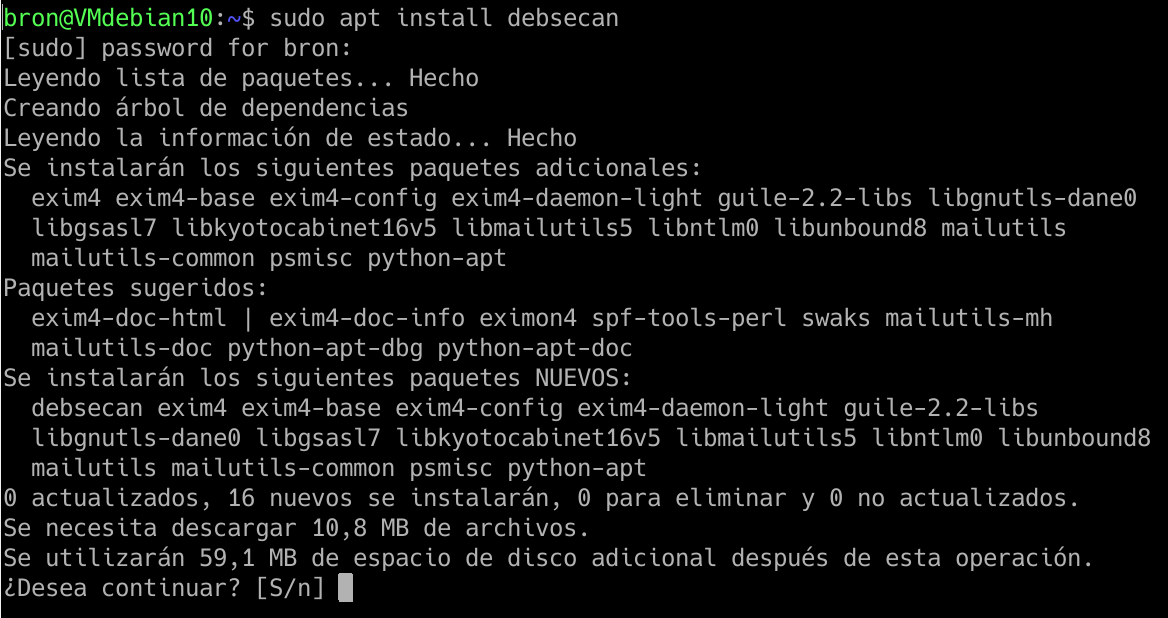
In the following screenshot you can see all the additional packages that you must install in order for it to work correctly:
Once we have installed it, we can run it with the help, so that it tells us what arguments we can use and what options we have available:
debsecan --help
We can also run the man pages for the most complete help of this tool, to open the complete manual, just run the following:
man debsecan
How this tool works
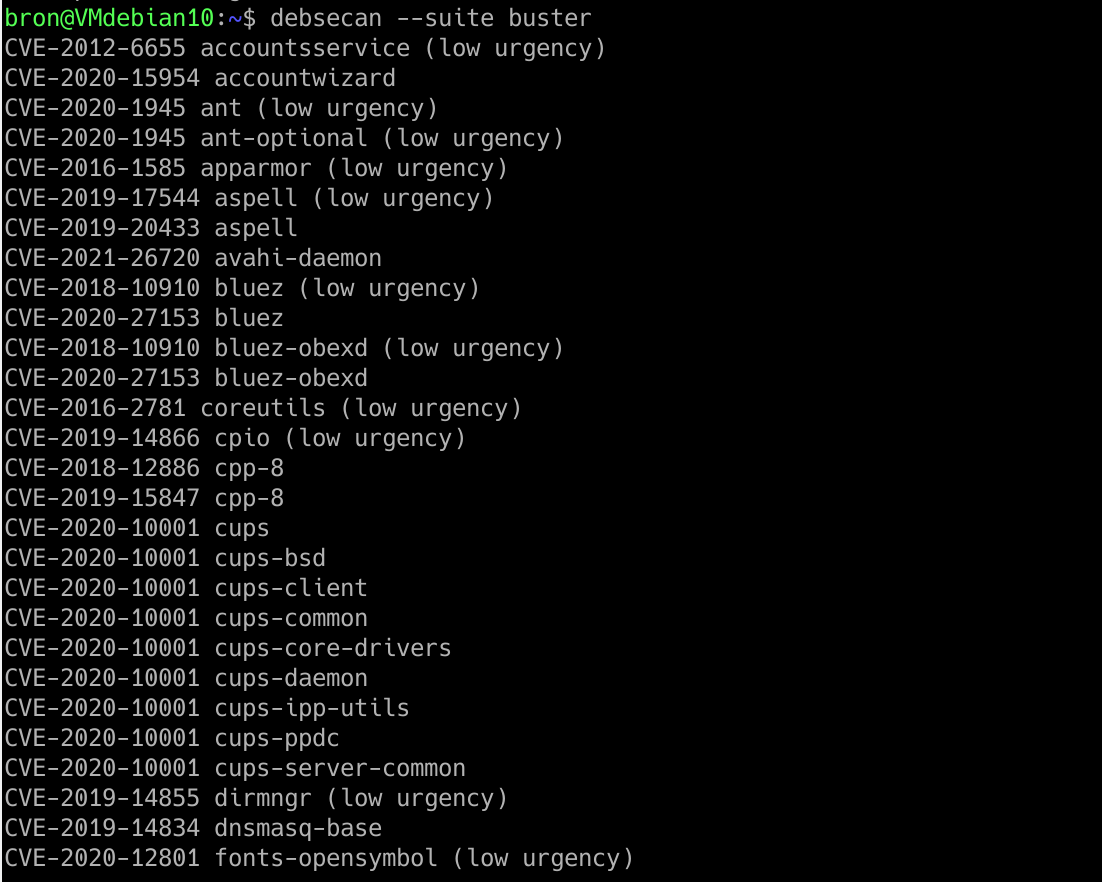
The way debsecan works is really easy, we just have to run the program with the argument of the Debian version we are using:
debsecan --suite buster
Once we execute this command, we will get a list of all the vulnerabilities that it has had or have in this version, and also a description of if there is little urgency to solve it, if it is already solved, even if it has little urgency, or if it is simply fixed the problem. It will also show us if the security flaw is not fixed, but it does have it in the vulnerabilities database.
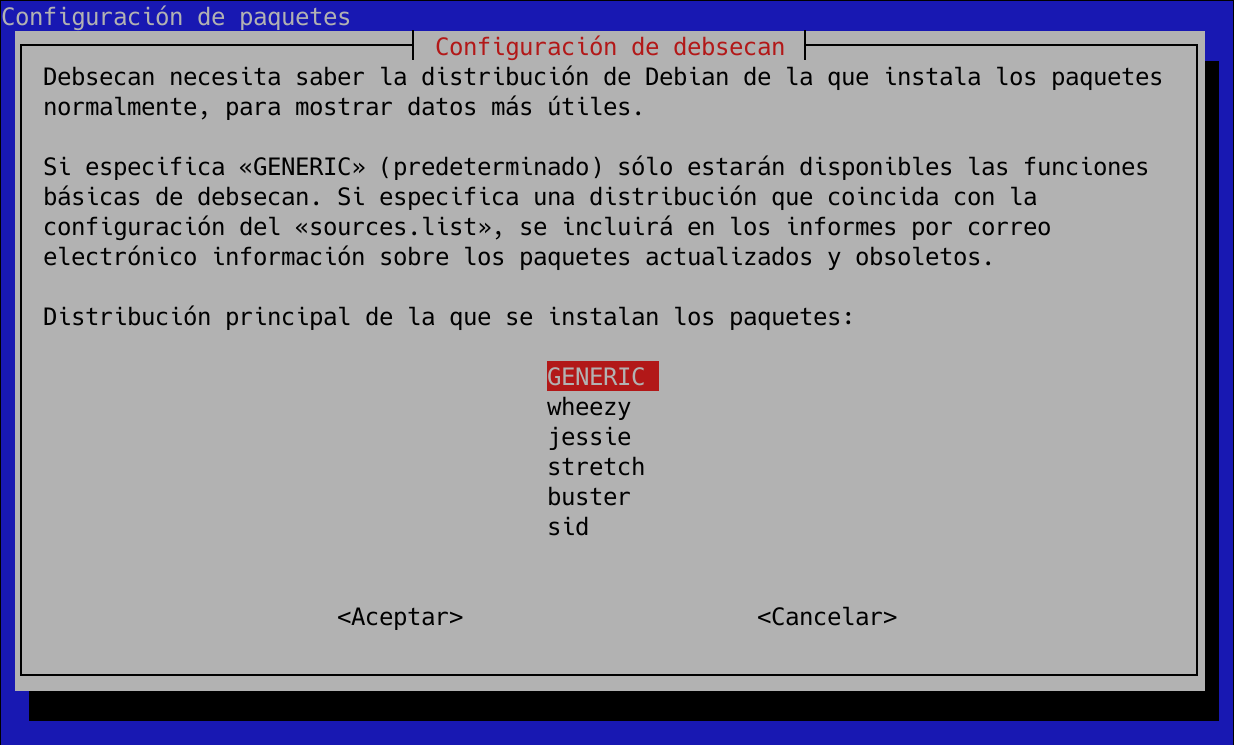
We have the possibility to configure debsecan to always use the version of “Debian Buster” (the one we are using), without having to define it in an argument. To do this, we must execute the following command:
sudo dpkg-reconfigure debsecan
And the following screen will appear, where we must choose the version of our distribution:
If we take advantage of using this configuration wizard, we can also configure debsecan to send us automatically and once a day, any change that occurs in the vulnerabilities via email:
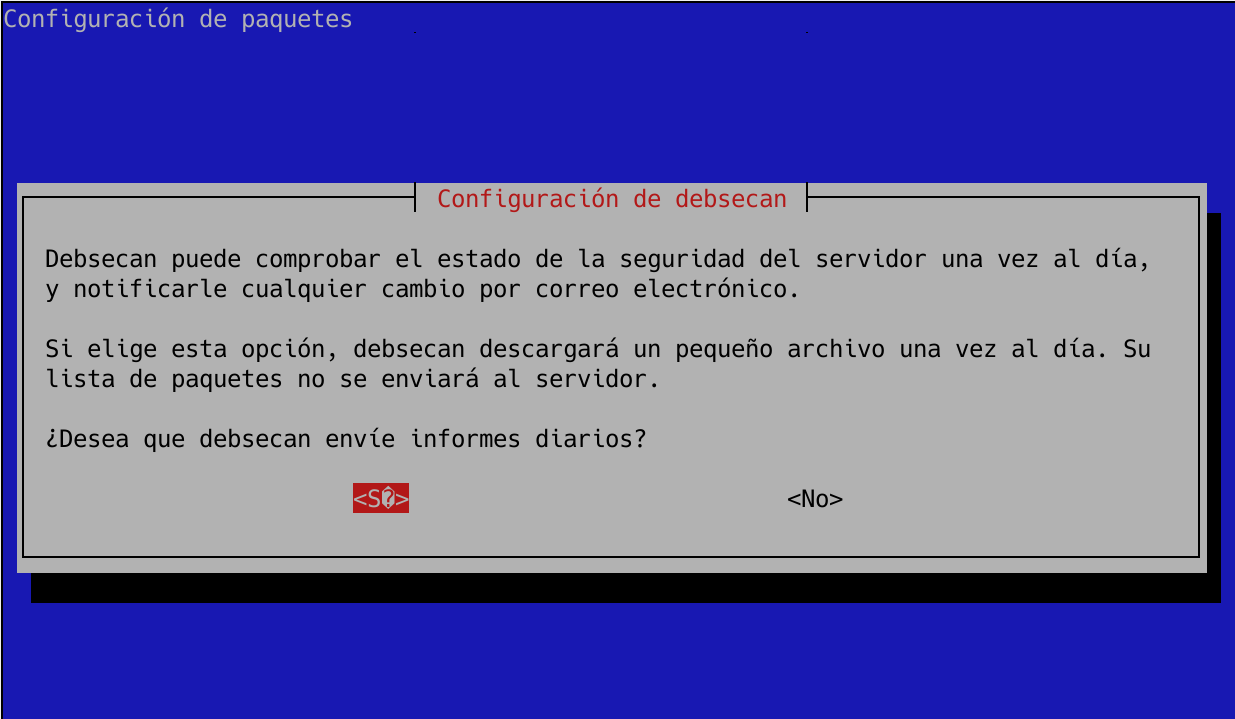
Next, we will define our email address, and the operating system itself will be in charge of sending us a daily email about the status of the system’s security. It will also ask us that Debsecan downloads the vulnerability information from the Internet, if the server is not connected to the Internet, or we do not want it to make requests to the Internet, we can define a URL with the vulnerability information to add it to its database. Once configured, we can run debsecan without having to put «–suite».
A very interesting order is the following:
debsecan --suite buster --only-fixed
This option lists the vulnerabilities for which there is a solution available, and we have to update the operating system to get rid of them. Note that a solution may appear, even though the package is not yet available in the Debian repository for update or installation. If it appears empty, it means that we have all the updates and patches available:
If we execute the following command:
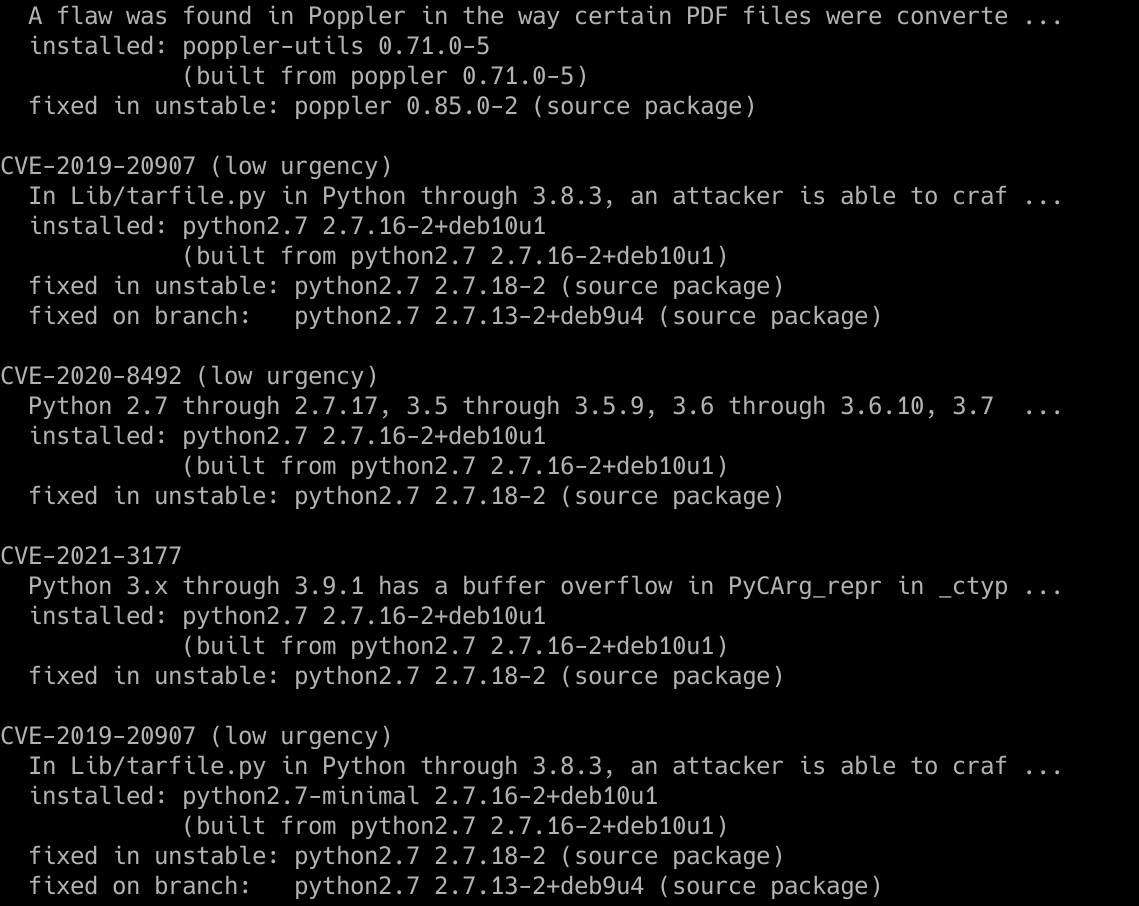
debsecan --format detail
It will show us all the vulnerabilities fixed or not but more in detail, in addition, it will show us which version of the software has the security problem, and which version solves it, both at the level of the unstable patch and the main repository. It is possible that the patch is in the repository “unstable” for weeks or months, so we must take it into account.
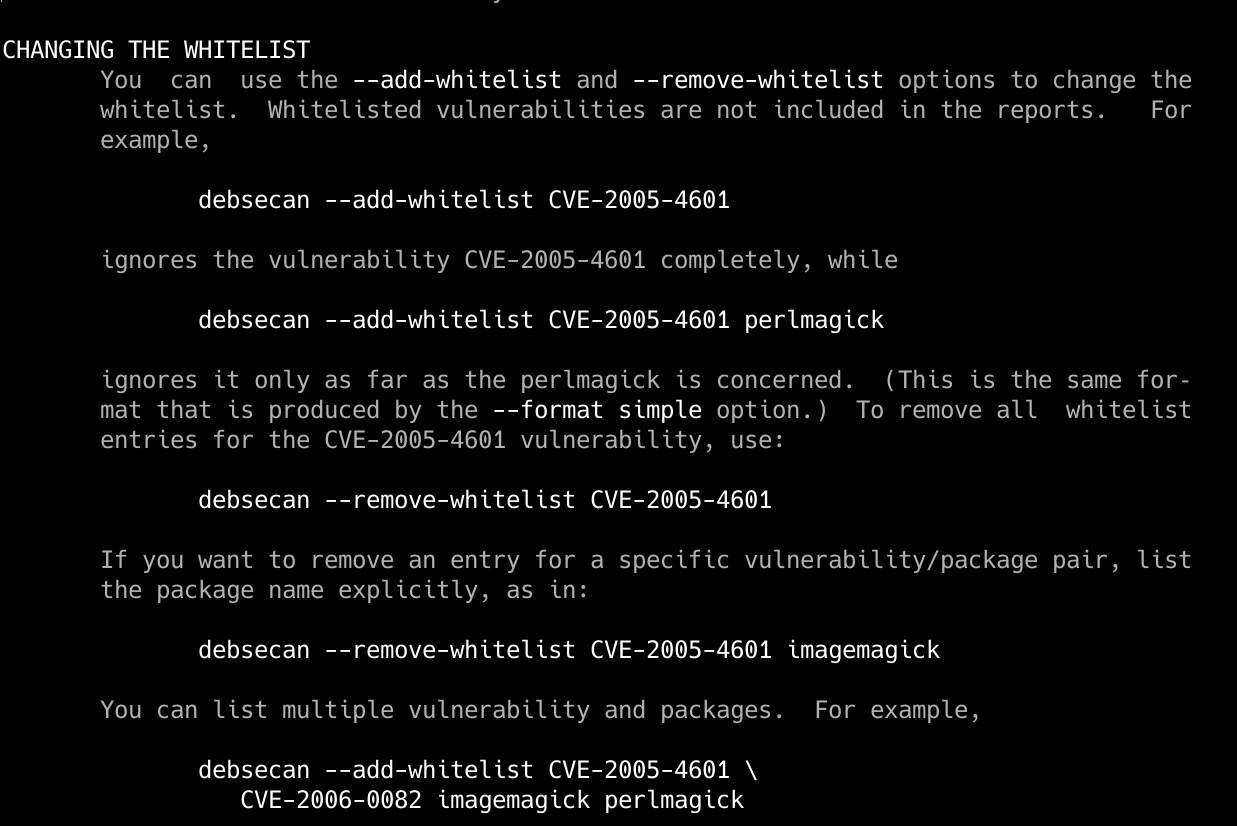
In the man pages, we can see in more detail how the whitelist works. Let’s imagine that we want to put a certain package with CVE code in a white list, in such a way that it never appears in the report list, to do so, we will simply have to execute the following:
debsecan --add-whitelist CVE-XXXX-XXXX
We will have to put the CVE code to be added to the white list. If we remove something from the white list we can also do it easily, so that it is included in the daily vulnerability reports.
As you can see, the debsecan tool is very useful to keep us informed of all the security flaws that are being found and that affect our Debian operating system, either the operating system itself, or the packages that we have installed. Thanks to debsecan we will be able to receive daily emails with the news regarding the resolution of vulnerabilities by the development team of the different software.
Finally, as a fundamental security measure on any server, we must never install programs or packages that we do not use, to minimize the surface of exposure to a serious vulnerability. Of course, hardening the server is essential.