More than ever, there are no excuses when it comes to hacking tools that are easy to install and really useful. Also, if you use Linux as your main operating system, or if you use it every so often, you will find many options. On this occasion, we are going to show you a quick and simple tutorial to install a solution called FinDOM-XSS . This tool only requires a few commands and will help you detect XSS vulnerabilities, that is, Cross-Site Scripting. Above all, it focuses on DOM-based XSS vulnerabilities.
What is DOM?
Its acronym stands for Document Object Model . In Spanish, it refers to the Document Object Model . It consists of an API that is developed in HTML and XML format documents. But what exactly does it do? It is responsible for constructing the logic of the documents of the aforementioned formats, so that they can be accessible and manipulated. We can better understand the concept thanks to HTML format documents.
We know that HTML is one of the essential formats of the web as we know it. An HTML file can have content like the one shown below:
<!DOCTYPE html>
<html>
<head>
<title>Página HTML</title>
<style>
body {
background-color: red;
text-align: center;
color: white;
}
</style>
</head>
<body>
<h1>Este es un encabezado</h1>
<p>Este es un párrafo.</p>
<img src="avatar.png" alt="Avatar" style="width:200px">
</body>
</html>
If we look closely, the HTML file that we share is divided into several parts:
- The header (head) which is where we make some essential definitions before going to the content of the page in question:
- The main title on the page that appears in the tab of our browser (title).
- The section where we customize the layout of the page, that is, the general format it will have. It’s like choosing a WordPress or Blogger theme that we like the most.
- The body of the page which is where the content is stored (body):
- We put a header.
- We put the text we want.
- We insert an image of our preference in which we can customize its width and / or height.
Of course, all of this can be extended to much more. Just with an HTML document we can get a lot out of the multimedia content. However, this example shows us that thanks to DOM, it is possible that we can manage in a practical, simple and above all standardized way. The DOM model does not reserve HTML, it is open to other popular programming languages such as JavaScript.
DOM-based XSS attacks and vulnerabilities
DOM-based XSS attacks are carried out by modifying the DOM environment that is displayed in the user’s browser when visiting a certain web page. Basically, when a user visits a web page, the browser interprets the code in such a way that it can visualize what it wants. That is, images, text, video, audio and much more. However, this dangerous variant of XSS attack has the ability to alter what the user can see in the browser. It does so in a way that leads to damage such as the installation of malware, various types of viruses, scripts that consume your computer resources by mining cryptocurrencies, and much more.
We are going to build on an example shared by OWASP to illustrate how this attack is put into action. Let’s suppose that you want to visit the following web page which enables you a form to select your preferred language:
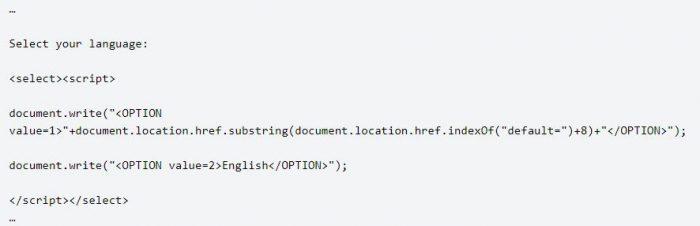
The URL, that is, the link of the original page is the following:
http://www.some.site/page.html?default=French
Very easily, a cybercriminal can alter said URL and it looks like this:
http://www.some.site/page.html?default=<script>alert(document.cookie)</script>
As we can see, what distinguishes the second URL from the first is the following:
default=<script>alert(document.cookie)
Instead of saying ” French “, the cybercriminal manages to alter the URL so that a ” document.cookie ” is displayed in the user’s browser, which can be any piece of malicious code.
The DOM-based XSS attack is possible in this case because the original Javascript code of the web page does not accept HTML code. Consequently, the browser directly interprets what the page URL indicates. The latter, regardless of whether the script the URL refers to is malicious. Unfortunately this is somewhat difficult for the user to control. However, later we will give advice to protect ourselves from this type of attack.
What is XSS?
It is worth refreshing the concept of XSS injection attacks. The acronym stands for Cross (X) Site Scripting. It consists of the action of malicious scripts that are injected into web sites and applications that, in principle, have lawful or benign purposes. How do they occur in general? The cybercriminal takes over the site or the web application, especially on the front-end , and in various ways malicious code is inserted. Unfortunately, it is a common situation that web sites and applications do not have strong control over what is executed on the end user side or what the user can insert especially through web forms. .
Besides DOM-based XSS attacks, which we have described in this note, there are other variants that are as or more dangerous than this one. Stored XSS and Reflected XSS should be mentioned , which are attacks that are more aimed at violating the security and integrity of the web server.
How to install FIN-DOM XSS
This solution is a powerful scanner for vulnerabilities that could lead to DOM-based XSS attacks. It is extremely simple to install, you only need to have Linux through the distribution of your choice. Remember that it is not necessary to have a separate computer with this operating system. You always have the option to virtualize!
The first thing we must bear in mind is that the installation is through the command line and we will obtain everything we need through its official portal on Github.
Install LinkFinder
It is a script developed in Python to detect endpoints and their parameters in Javascript files. It is widely used by pentesters and people dedicated to hunting bugs ( bug hunters ). As well as FIN-DOM XSS, we are going to install from the command line. This is a prerequisite or dependency for the correct operation of the scanner.
Enter the following commands to install LinkFinder :
$ git clone https://github.com/GerbenJavado/LinkFinder.git
$ cd LinkFinder
$ python setup.py install
Finally, we add a couple of dependencies that are modules in Python so that this script works properly through pip . For more details regarding LinkFinder, you can refer to the official portal on Github.
$ pip3 install -r requirements.txt
Starting with FIN-DOM XSS
Since you have completed the prerequisites, you can proceed to install the scanner in question with the following command:
$ git clone https://github.com/dwisiswant0/findom-xss.git
Once the installation is complete, you must make an adjustment in the configuration. It is to change the value of the LINKFINDER variable on line 3 with the corresponding path to your main LinkFinder file.
To execute FIN-DOM XSS you only need to execute the following command:
$ ./findom-xss.sh https://target.host/about-us.html
The structure is simple, the command that calls FIN-DOM XSS to run is ./findom-xss-sh .
On the other hand, there is the link that would be our target that we want to examine in search of vulnerabilities. It can be any web page. Then it is possible to translate the command above to a more concrete example.
$ ./findom-xss.sh https://www.freecodecamp.org
You even have the option of adding one more parameter to the command so that the results are automatically exported in a plain text file located wherever you prefer.
$ ./findom-xss.sh https://www.freecodecamp.org /rutaejemplo/rutaejem/resultadosescaneo.txt
However, even if you don’t put the third parameter, the results of the scans are stored by default in the results folder and the file name is target.host.txt .
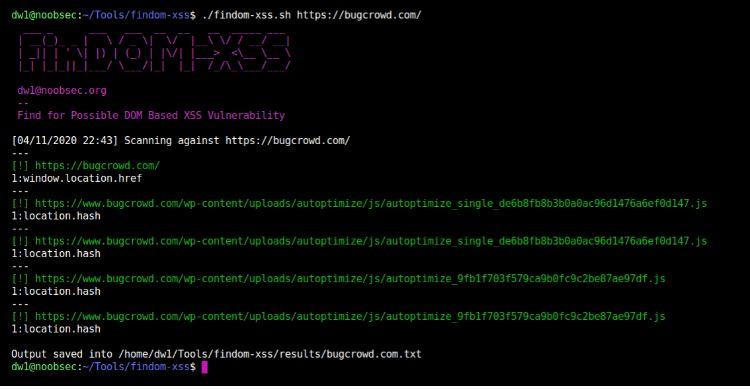
This is the screen result that you should get when successfully executing FIN-DOM XSS:
We hope this tutorial helps you find these types of vulnerabilities.