The firewall-oriented operating system pfSense has several VPN protocols to establish remote access VPN servers and also Site-to-Site VPN tunnels. L2TP / IPsec is a very popular VPN that allows remote VPN clients such as computers, smartphones and tablets, to connect to the local professional or home network securely. L2TP will be in charge of establishing the tunnel, and the IPsec protocol will be in charge of providing confidentiality, authentication and integrity to all transmitted data. Today in this article we are going to explain step by step how to configure the L2TP / IPsec VPN server to connect remotely.
What is a L2TP / IPsec VPN server for?
A VPN server in our pfSense will allow us to remotely access the different subnets that we have configured, it will also allow us to redirect all Internet traffic to the VPN server to go to the Internet through it. Thanks to the configuration of a VPN server, we will be able to connect to an insecure network in a secure way, because all the traffic from the origin to the VPN server is encrypted and authenticated.

L2TP (Layer 2 Tunneling Protocol) is one of the most widely used VPN protocols, it makes use of the PPP protocol for the connection of the different links, in addition, it includes PPP authentication mechanisms such as PAP and CHAP, in addition to supporting the use of RADIUS servers for client authentication. This type of VPN protocol is multiprotocol, and allows access to remote local area networks. The negative part is that it does not present a robust cryptography, therefore, it is not safe to use it. It only allows authentication between the end points of the tunnel, but not for each of the packets that travel through it, the same happens with the integrity of the packets, it is not checked. Also, L2TP does not encrypt the traffic from source to destination.
With all this in mind, the IETF organization made the decision to use the cryptographic protocols of IPsec in conjunction with L2TP, to provide the confidentiality, authentication and integrity features of the L2TP tunnel. For this reason, we will always find this protocol written as “L2TP / IPsec” in operating systems, because it uses both protocols simultaneously.
Once we have a summary of how both VPN protocols work, we will proceed with the configuration. By having two protocols to configure, L2TP and IPsec, we are going to clearly divide the configuration into two parts.
L2TP protocol configuration
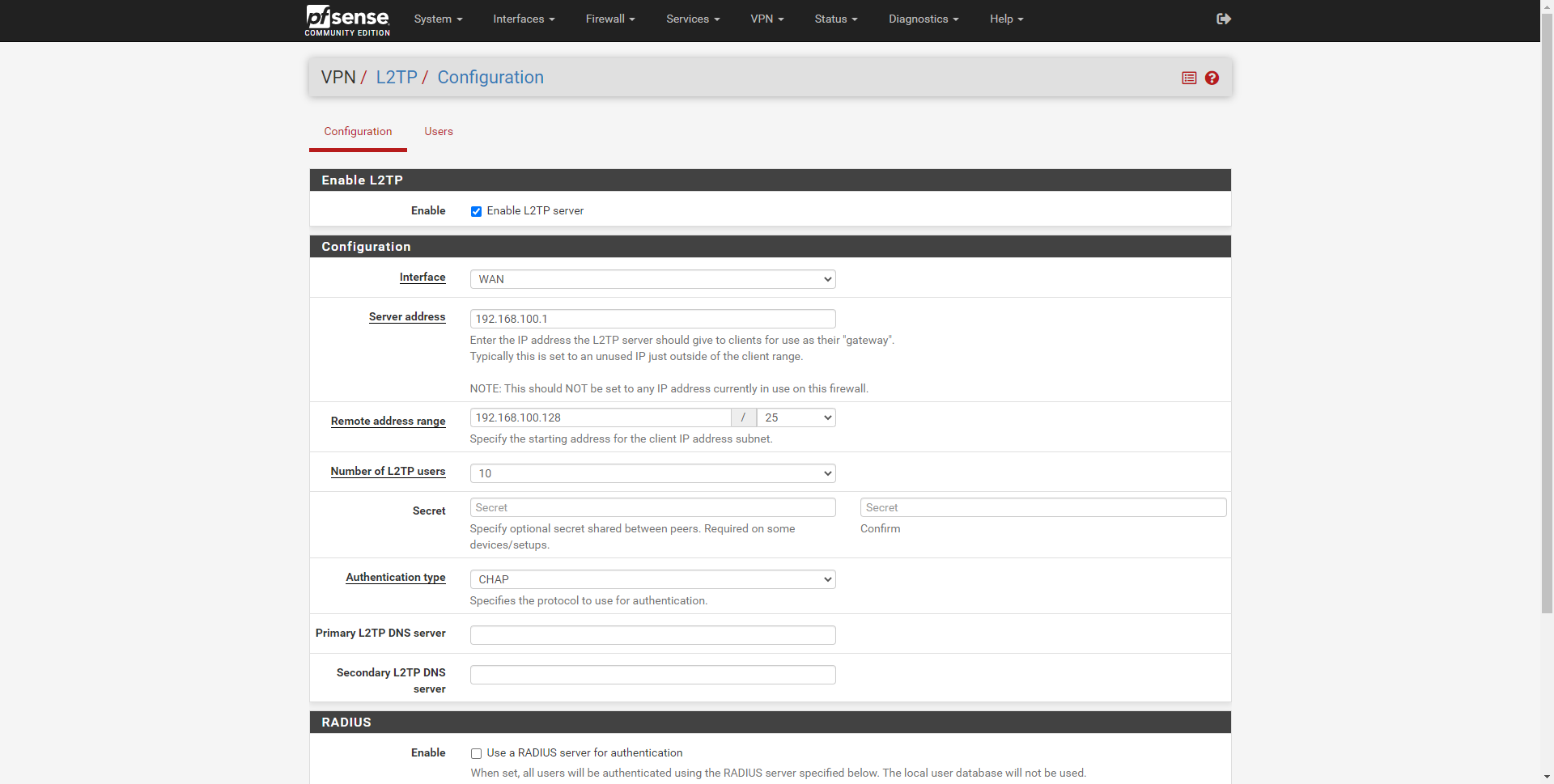
The first thing we must do is configure the L2TP protocol, for this, we go to the “VPN / L2TP” section, and configure it as follows:
- Enable L2TP
- Enable L2TP Server: Enabled
- Configuration
- Interface: WAN
- Server Address: 192.168.100.1; We must put a subnet that is not in use, and that serves only to use it as a customer gateway
- Remote Address Range: 192.168.100.128/25; We give a local subnet to connecting clients.
- Number of L2TP Users: 10, this can be configured to suit the user.
- Secret: 1234clavel2tp; We can put a passcode, it is recommended to put it, although some clients do not require it. It depends on the configuration.
- Authentication Type: CHAP
- Primary / Secondary L2TP DNS Server: we can put a DNS server for the clients
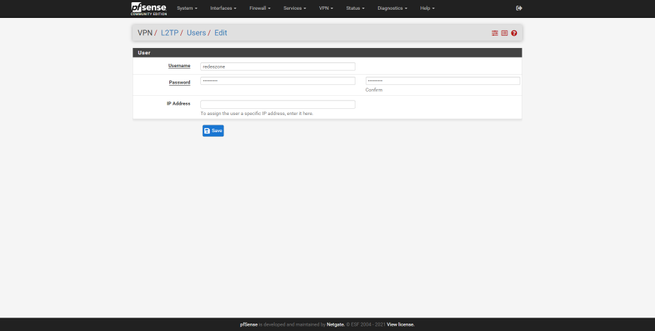
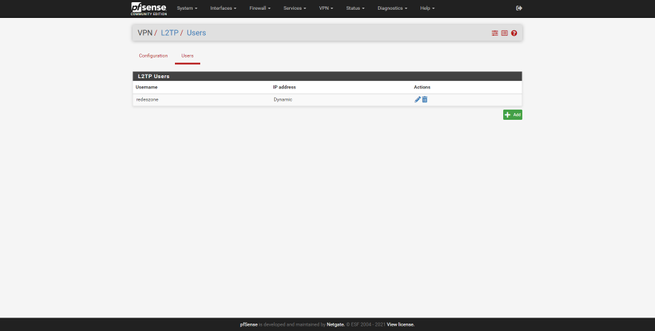
Once we have configured it and clicked on «Save», we go to the «Users» section and create a username and password to access. This is where we will have to register all the users of the VPN server to which they are going to connect, the IP address part can be left blank without configuring, so that the server assigns the IP dynamically.
Once the L2TP server is configured, we can configure the IPsec protocol.
IPsec protocol configuration
To configure the IPsec protocol together with the L2TP protocol, we will have to perform a total of three actions. The first one is to enable the “Mobile Clients”, that is, the remote access VPN. The second is to enable IPsec phase 1, and then configure IPsec phase 2.
Configure the «Mobile Clients»
This is one of the most important parts, because if we go to the “Tunnels” section we create a Site-to-Site VPN tunnel, and what we want to do with IPsec is configure a remote access VPN so that the different customers.
In this menu we enable “Enable IPsec Mobile Client Support” and choose “Local Database” although we will use it because that is for xAuth authentication. We click on save.
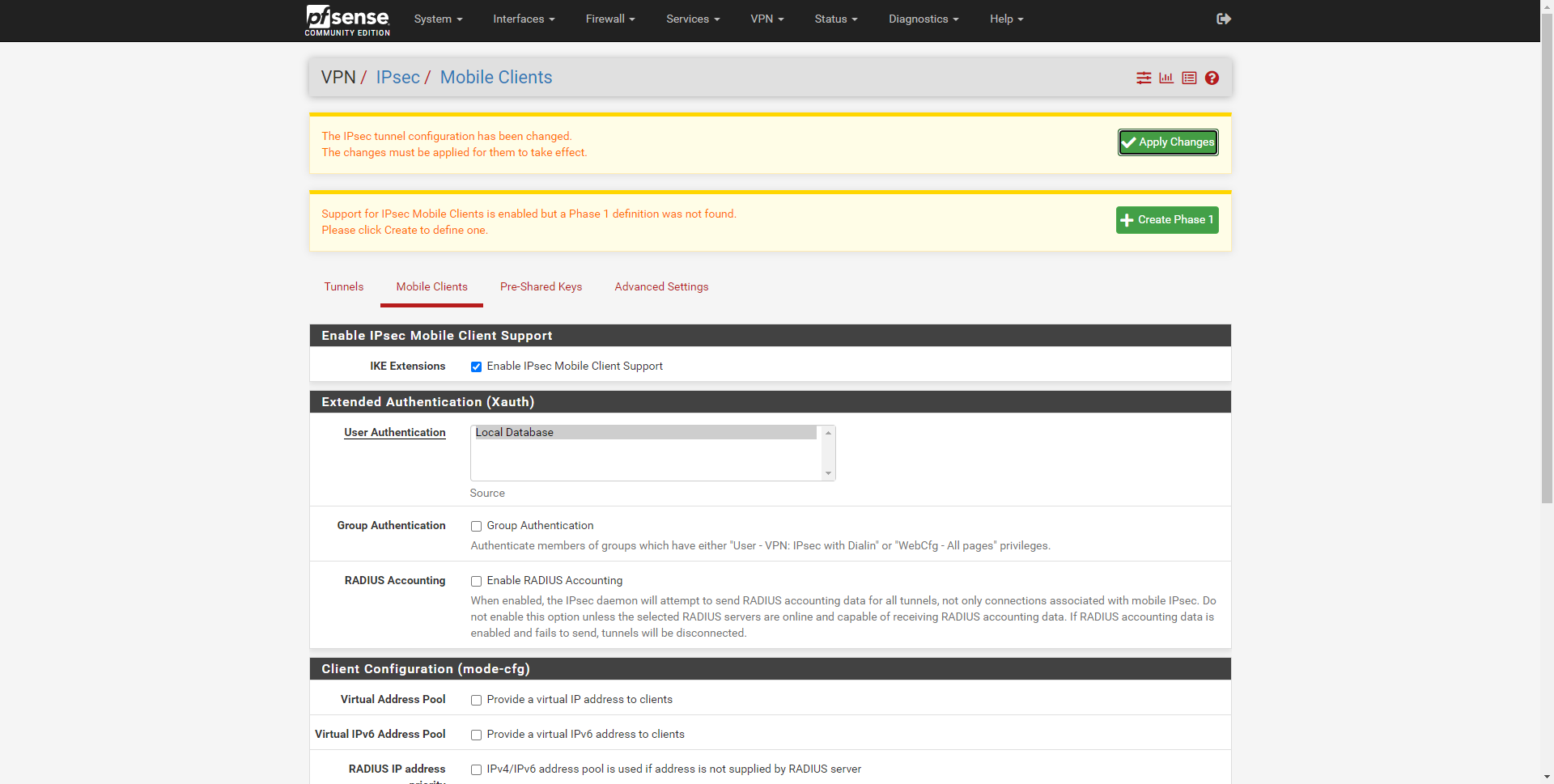
As soon as we click on «Save», we will also have to click on «Apply Changues», then click on the green button that indicates «Create Phase1».
Configure IPsec Phase 1
In this menu we will have to configure the IPsec protocol correctly to use it with L2TP, not all the configurations will work, in addition, depending on the VPN client used (Android, iOS, Windows …) the security configuration may change, since not all operating systems they support the best VPN ciphers. By default, we will see the following menu where we have selected IKEv2, which is not compatible with the L2TP / IPsec protocol that we want to configure.
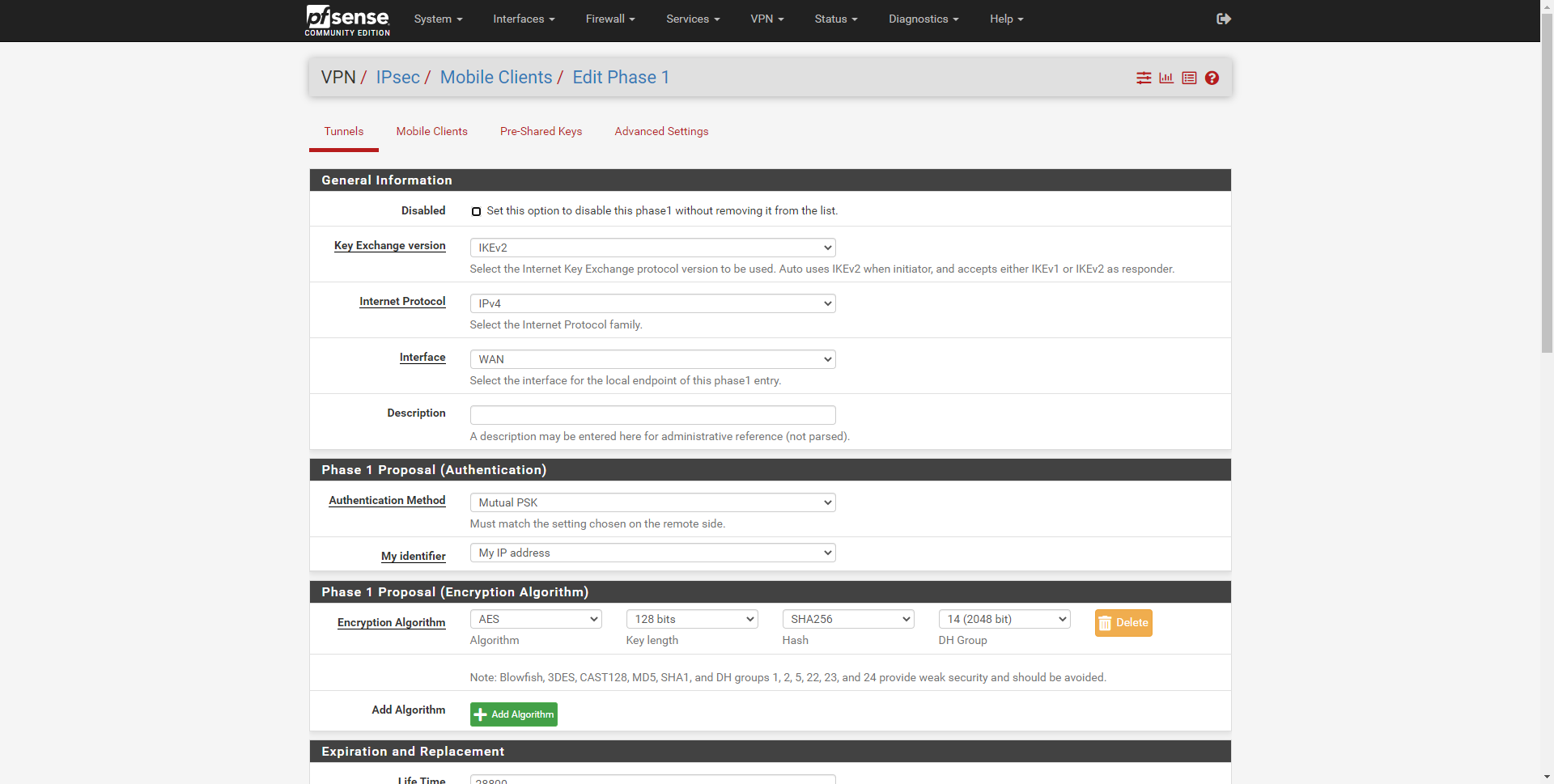
The options that we must configure for it to work correctly are the following:
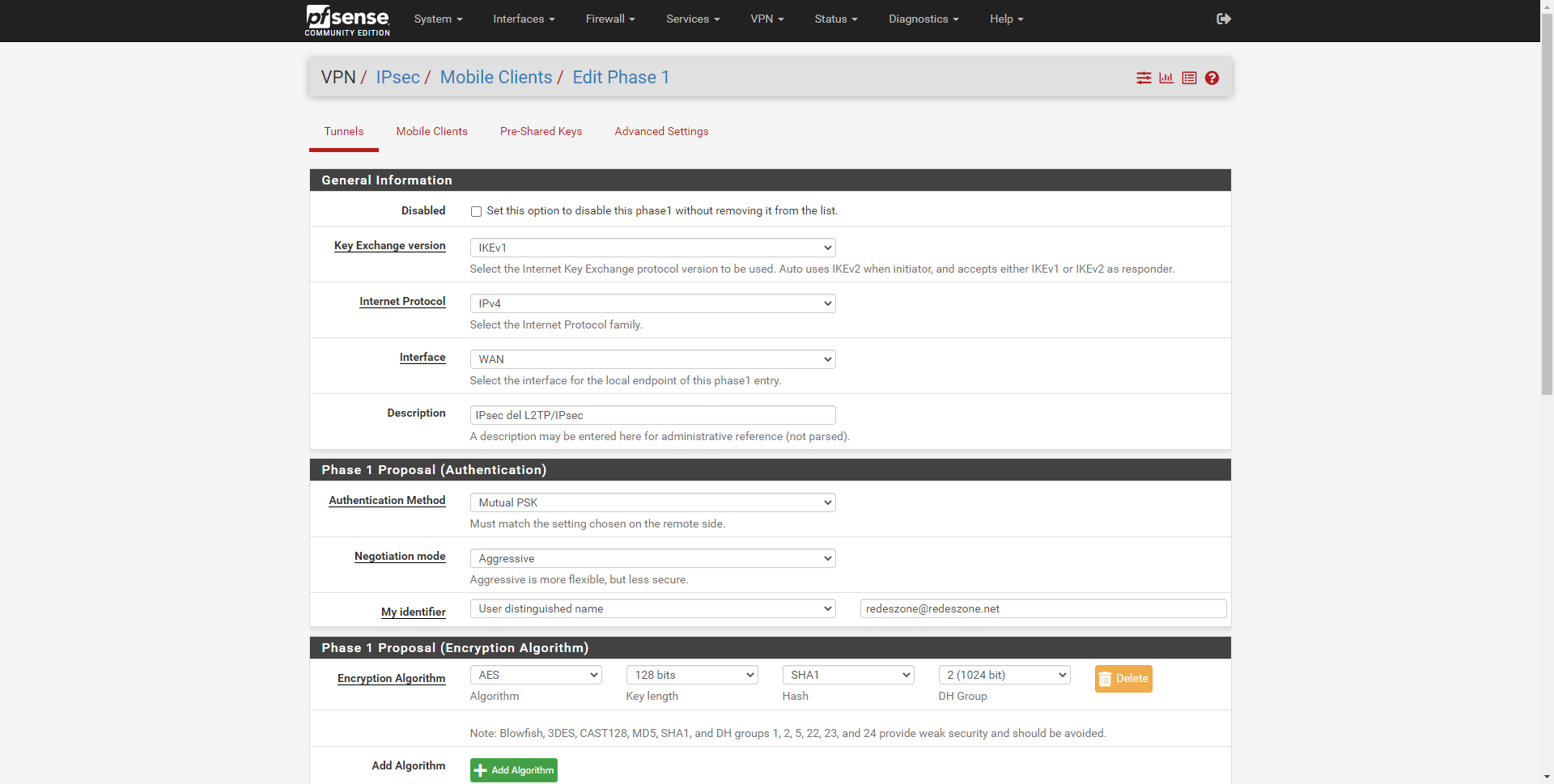
- General Information
- Key Exchange version: IKEv1, if we select any other it will not work.
- Internet Protocol: IPv4 or IPv6
- Interface: Internet WAN
- Description: we put a description.
- Phase 1 Proposal (Authentication)
- Authentication Method: Mutual PSK
- Negotiation Mode: Aggresive; if we select “Main” it is more secure, but it is less flexible, and we could prevent the VPN client from connecting correctly. Later if everything works with «Aggresive» we can test if with «Main» it works too.
- My identifier: User distinguished name – redeszone@redeszone.net or whatever you want.
- Phase 1 Proposal (Encryption)
- Encryption Algorithm: AES 128-bit, SHA1, DH Group 2 (1024-bit).
pfSense supports stronger encryption than this one that we have configured, but the problem is the VPN clients that are going to connect, which do not support greater security. To configure it with the best security, we can go testing based on the IPsec “proposals received” that we receive from the client, in this way, we will choose the most secure of all.
The rest of the configuration options can be left as they are, with the default options.
Once finished, we click on «Save», and now it will take us to the main menu where we have all the VPN tunnels with IPsec, we will have to click on the only one created and on «Show Phase 2 Entries» and then on «Create Phase 2» to continue .
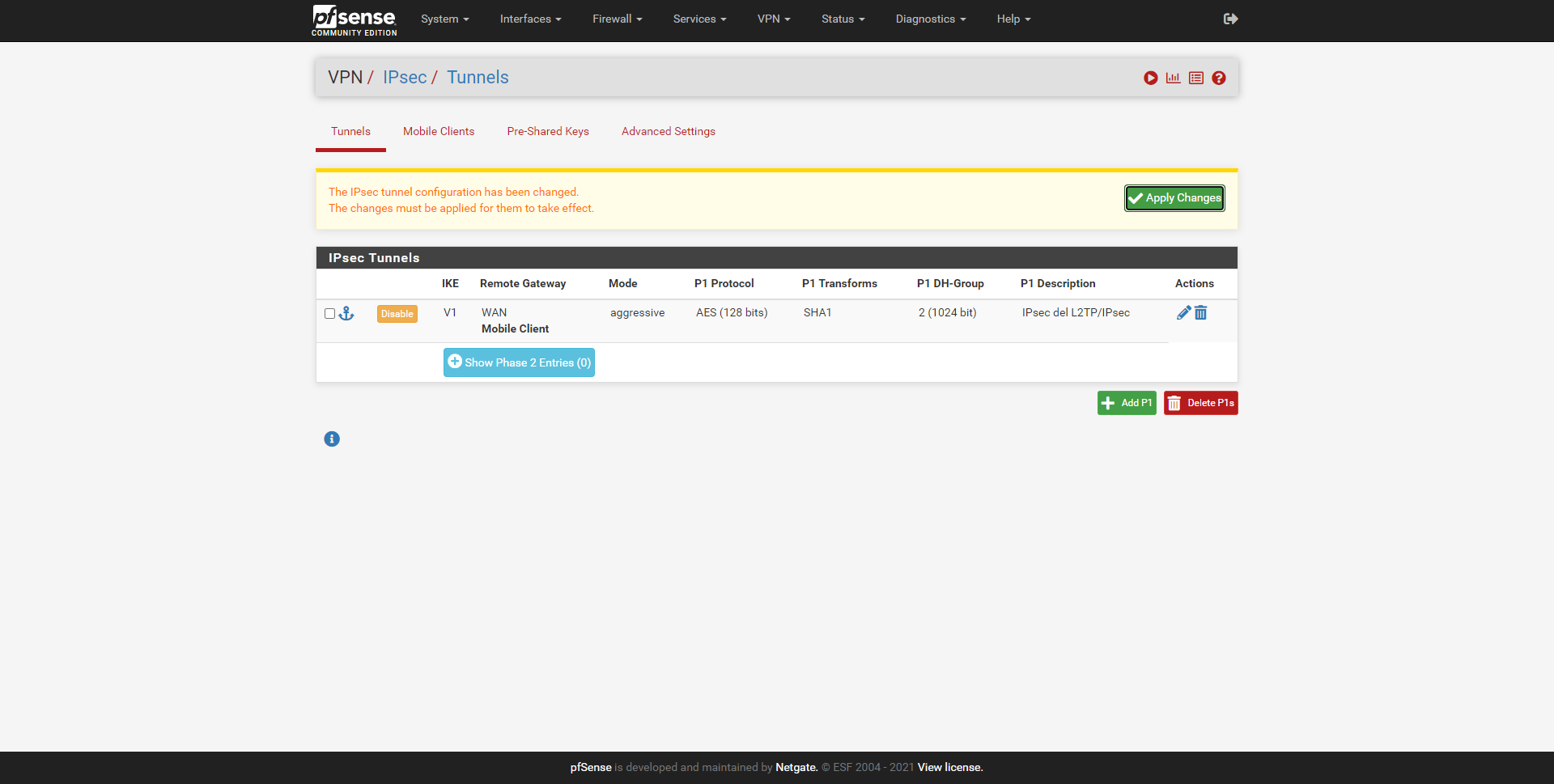
Configure IPsec Phase 2
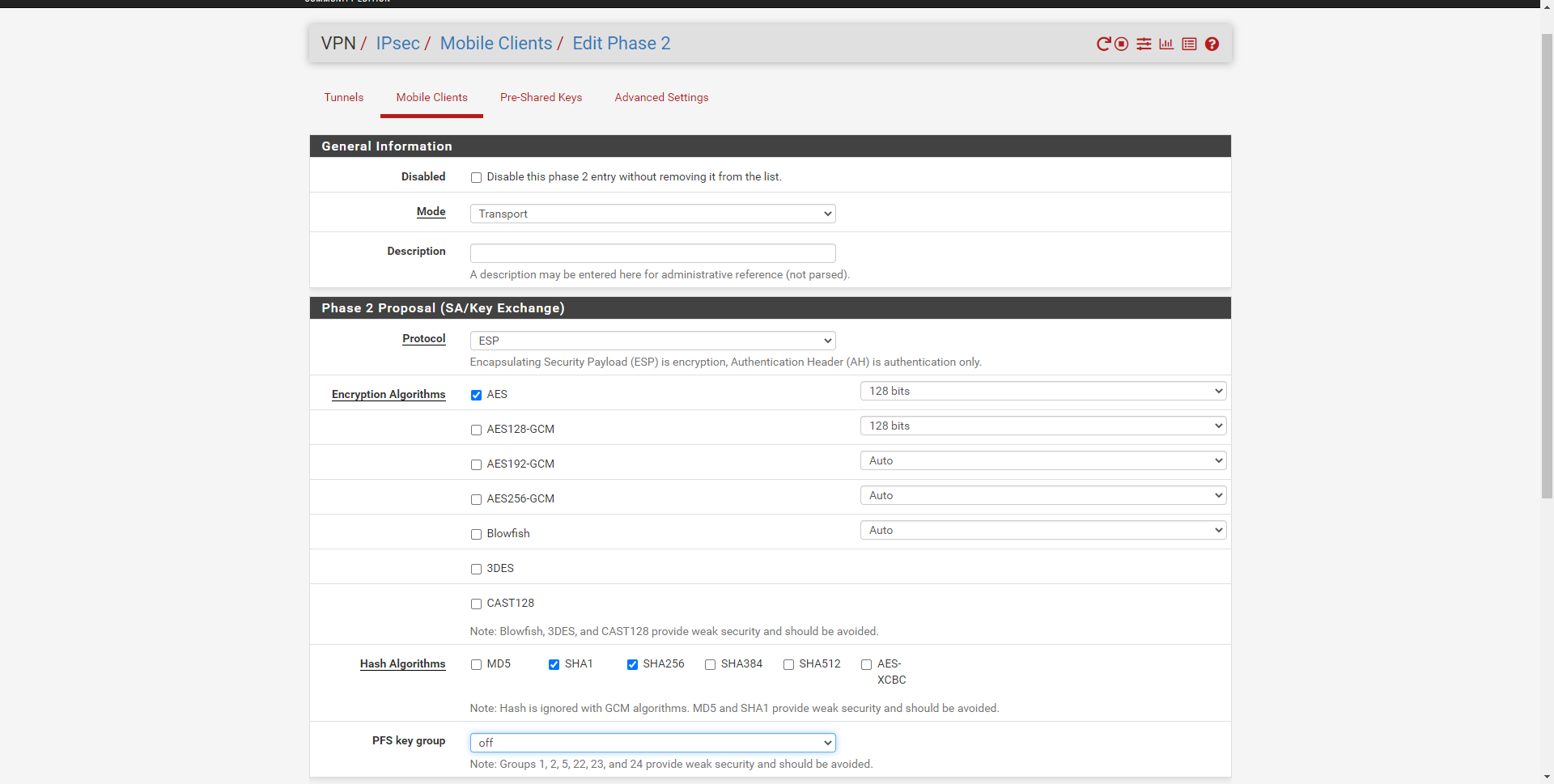
In this configuration menu we must put the following:
- General Information
- Mode: transport
- Description: a description that we want.
- Phase 2 Proposal (SA / Key Exchange)
- Protocol: ESP
- Encryption Algoritms: 128-bit AES
- Hash algorithms: we select SHA-1 and SHA-256
- PFS Key group: off, not supported by the protocol.
The rest of the configuration options can be left by default.
In the main menu of “IPsec / Tunnels” we can see a summary of everything we have configured.
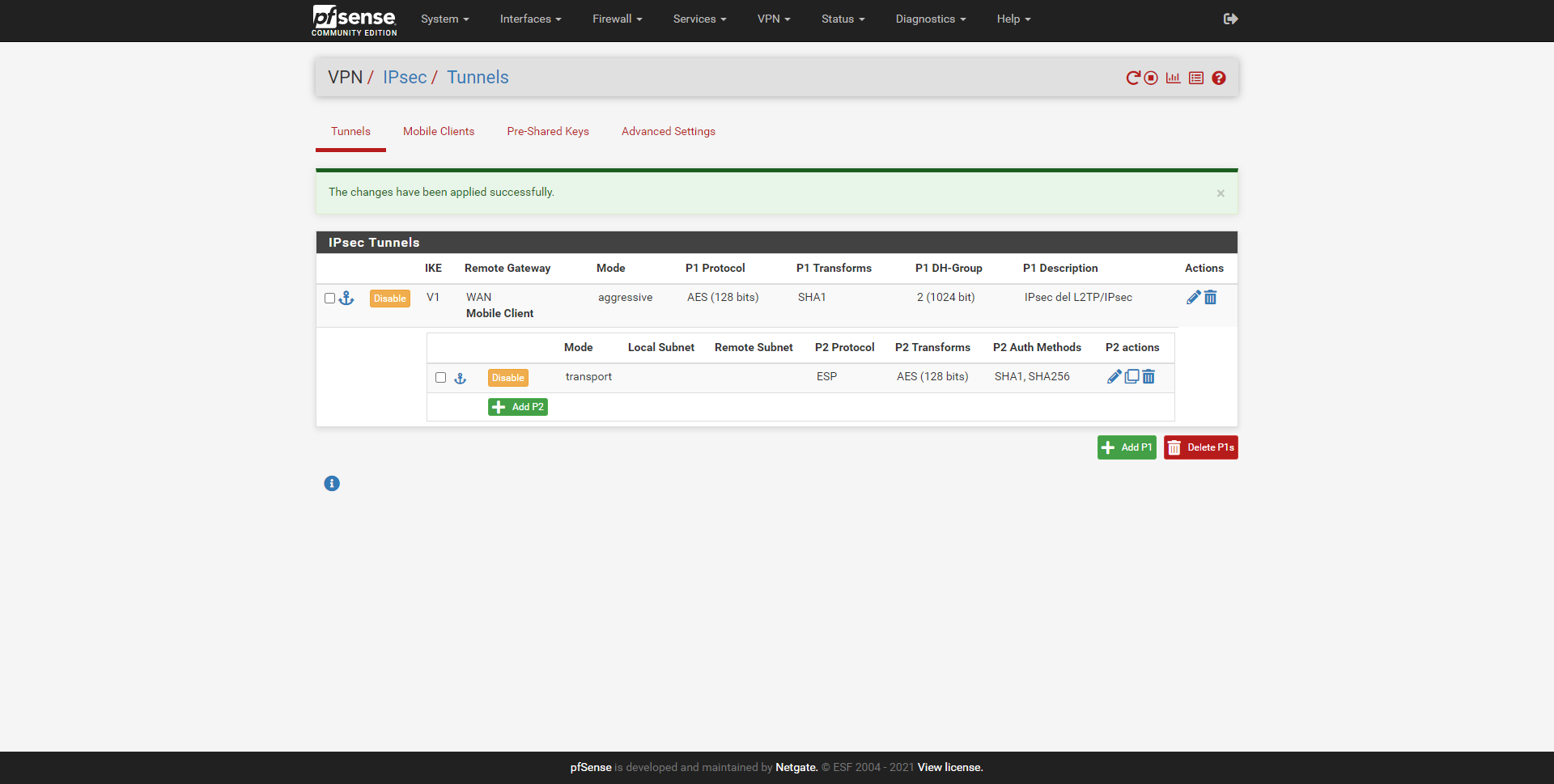
Now we will have to go to the “IPsec / Pre-Shared Keys” section and add a new identifier.
This new identifier must be:
- Identifier: allusers (must be like this, without capital letters and without any other name)
- Secret Type: PSK
- Pre-Shared Key: the password that we want, is shared with all the users who are going to connect.
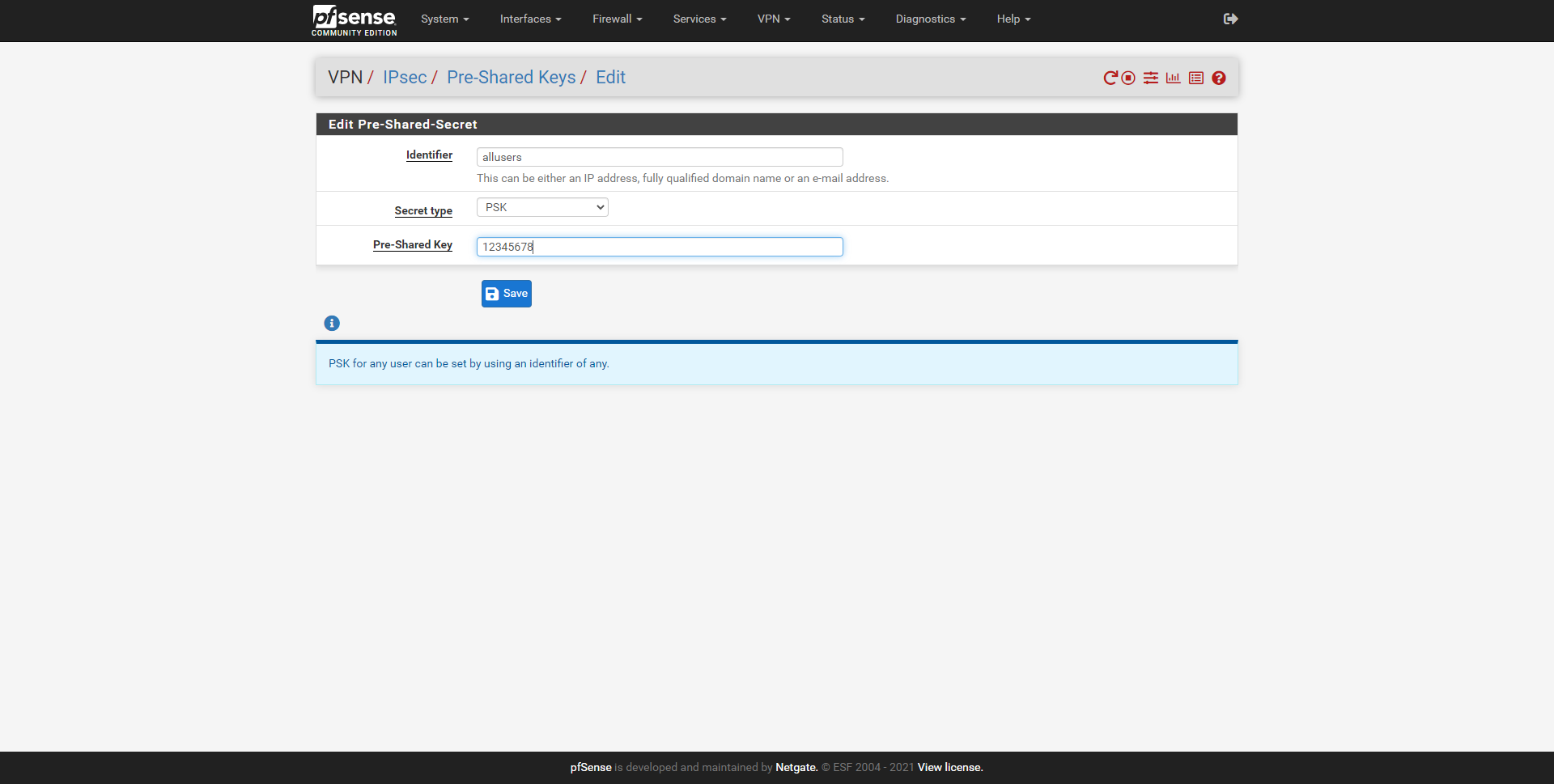
Once this is done, we will have the L2TP / IPsec server ready to accept connections, but first, we must create the corresponding rules in the firewall.
Open ports in the pfSense firewall
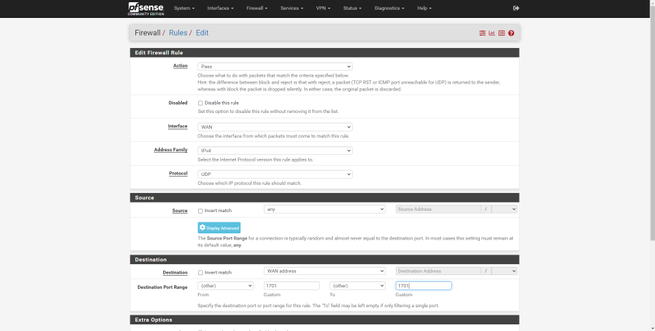
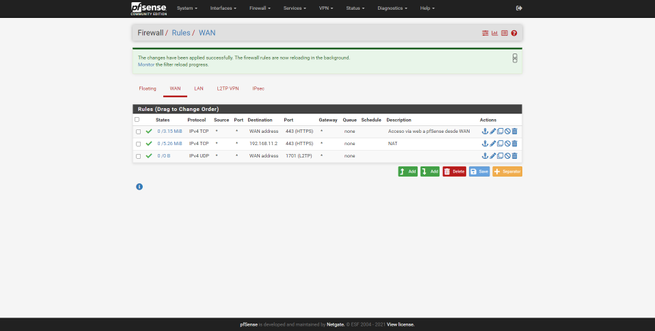
We will have to create a rule in the “Firewall / Rules / WAN” section with the following information:
- Action: Pass
- Interface: WAN
- Address Family: IPv4
- Protocol: UDP
- Source: any
- Destination: WAN Address on port 1701 which is L2TP.
We save and apply changes, ensuring that this rule will be followed.
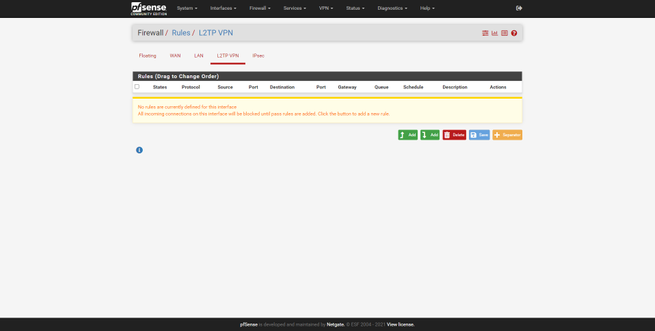
When we create an L2TP / IPsec type VPN server, we will have two additional tabs in “Firewall / Rules”, here we can allow or deny traffic to certain subnets, define different advanced rules, etc. For a first connection and to avoid possible configuration failures at the firewall level, we recommend that you create a “pass any any any” rule and apply changes. Later when communication has been established, if you need to define different rules, then you can edit more specific rules to meet all your requirements.
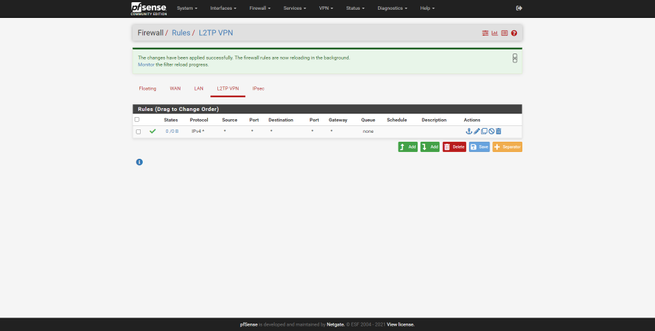
Once we have successfully configured the firewall, we will have to configure the VPN client to test the connection.
Connection test
In our case, we have established a VPN connection with an Android smartphone, specifically the Huawei P30 that incorporates an L2TP / IPsec PSK client. The configuration that we must carry out is the following (we cannot put capture because the operating system detects it as private content).
- Name: we give the VPN a name
- Type: L2TP / IPsec PSK
- Server: IP or DDNS domain of your VPN server
- L2TP Secret: 1234clavel2tp; the key that we put in the L2TP section that is shared with all clients.
- IPsec identifier: redeszone@redeszone.net
- Initial IPsec Shared Key: 12345678; the key we put for the identifier «allusers» in the IPsec / Pre-Shares Key section.
We click on save, and connect. When connecting, it will ask us for a username and password, these credentials are the ones we put in “L2TP Users”. Once done, it will connect us without problems to the VPN server and we will have access to the pfSense administration and any network.
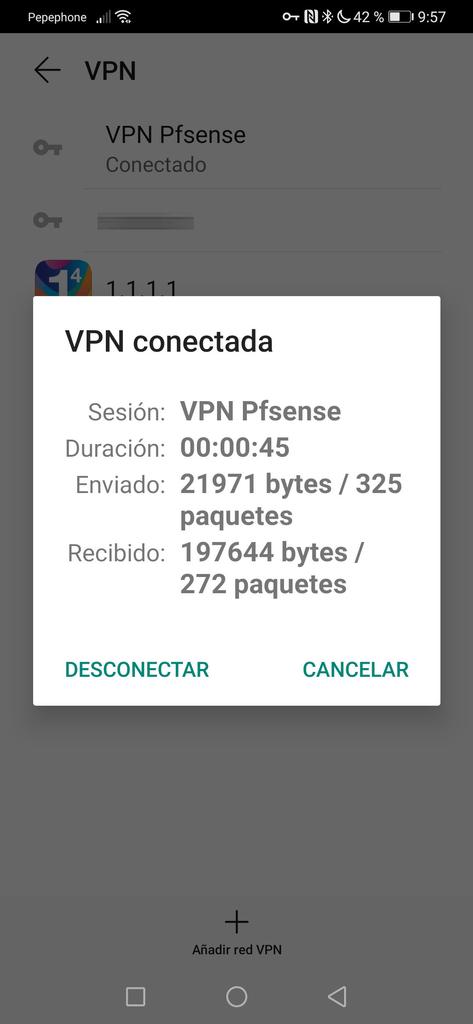
As you have seen, the connection has been successfully established, and there have been no problems.
Recommendations and advice
Depending on the VPN client you use, the server configuration may vary. For security, it is always advisable to use the best cryptographic algorithms, for this reason, we recommend modifying the security options and forcing customers to always choose the best ones, however, we must look at the IPsec records to see what « proposal »sent by different clients when connecting. Some smartphones use an L2TP / IPsec VPN client with support for the latest ciphers, however, other models do not. We will have to try and choose the safest possible globally, balancing between security and usability.
Another tip if you are going to use L2TP / IPsec for the first time, is to know in advance which clients you are going to connect, Android, iOS, Windows computer, etc., since the configuration could be different depending on how the client is internally configured. It is possible that they cannot all live together at the same time, for this reason you could use other VPNs such as OpenVPN or IPsec xAuth among others.
With this same tutorial, you will be able to configure the L2TP / IPsec RSA, modifying the «Mutual PSK» by «Mutual RSA» and configuring the corresponding server and client certificates. We will show you how to do it soon. This also brings complications, because if we create a CA with a client certificate that makes use of the latest algorithms, it is possible that it will return an error when we connect because they are not recognized.