Safety is one thing we must take very seriously. It is not something as simple as having a strong password and that’s it. There are also many other aspects that we must take care of if we want to keep our computers and devices safe. In that regard, security may seem like a complex and difficult task to tackle. However, it is not so complex if we set ourselves a series of tasks that we know how to perform. In this regard, we can make a series of reviews that, in a matter of minutes, will improve our cybersecurity. In this article we are going to talk about the security checks that you should do regularly.
If we do these security checks we will be more calm and secure. By simply doing these things that we mention below, you will be more secure and protected.

What tasks should I do regularly?
There are several tasks that we should perform regularly, some of them weekly and others monthly, but we must not get lost and meet the recommended deadlines to check that everything is working perfectly and without security incidents.
The update policy
The moment an update arrives for our operating system Windows, Linux, Android, iOS and more, we must apply it as soon as possible. Sometimes, when an update arrives , what you don’t have to do is leave it pending for a long time . If we want to have good security controls, we should apply them on the same day that we already have them downloaded.
When developers find a security flaw in their software, the solution they apply is to release a security patch that solves the problem. If we ignore updates and put them off too long, it opens the way to security vulnerabilities and we could end up with our PC infected by malware.
On many occasions the victims of historical security attacks have been because they were using outdated operating systems. That is why you should not use unsupported operating systems such as Windows XP or Windows 7 among others. By not receiving updates, the security flaws that appear are not corrected and therefore we are exposed to them. Another way to gain security is to keep our network devices up to date.
Password security controls
The use of strong passwords is essential to keep our passwords safe. One of this type should contain minimum:
- 12 characters.
- Capital letters.
- Lowercase.
- Numbers.
- Symbols such as &.
Short passwords that don’t follow the guidelines we mentioned earlier are easy to guess. In this regard, one of the security controls that could help us the most would be to have a password manager. In that regard, a free, secure one that also has two-factor authentication would be Passwarden. This password manager could work perfectly in the private cloud, using Docker to host all your information.
To do this you have to take your time since today we have many accounts. We must start with the most important ones such as Google and other emails, bank accounts and social networks. Also note that we can use tools like Have I Been Pwned to check if our passwords have been leaked.
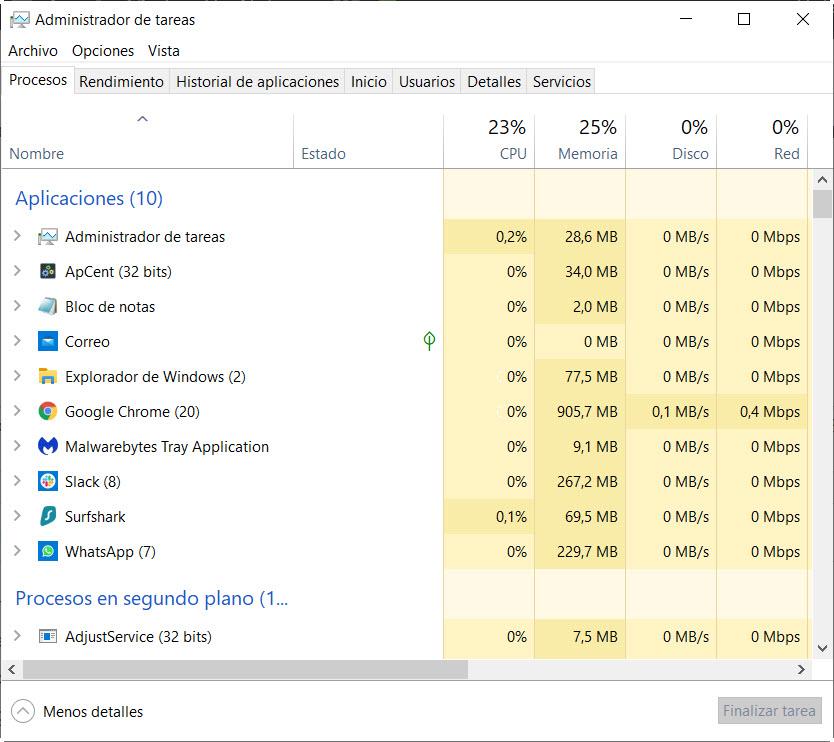
Check your computer’s running processes
It is a good idea to review the programs that are running on our computer to find out what programs are being used. It can help us when we carry out security controls to:
- Detect suspicious programs.
- Find out what background programs are running and consuming resources. On computers that are fair in terms of hardware power, if you disable them at Windows startup, it can be of great help.
To do this, in the Windows Start Menu , we write Task Manager and press enter. In the processes tab we can see it:
Analyze equipment, verify permissions, and more
On some occasions we may see signs that we have some type of malware. However, in many cases it is silent and we may not realize that we have a problem. For this reason we must have an antivirus such as Windows Defender installed or activated on our computer, and periodically analyze our computer . Regarding Android and iOS, a good practice would be that from time to time we review the permissions that we have granted to the applications . Sometimes they include something that is not necessary.
Finally, regarding security controls, we must review the connections of our account . Some web pages allow us to log in with the credentials of another account such as Facebook, Google or Apple. This is not always convenient and sometimes for privacy reasons, for example, it would be convenient to register manually using another email.