Cybercriminals seek to act on the types of accounts we use the most. Their intention is none other than to obtain stolen data from the accounts they are attacking. Thus, a cyber espionage group known as “Molerats” has created a new malware that affects Google and Facebook. This group has been using campaigns of a new spear-phishing malware that relies on Dropbox, Google Drive and Facebook for command and control communication, and also to store stolen data. Thus, a new malware has been born that affects Google and Facebook.
These cybercriminals have been active since at least 2012, and are considered to be a division of a larger group known as the Gaza Cybergang.

SharpStage and DropBook rear doors
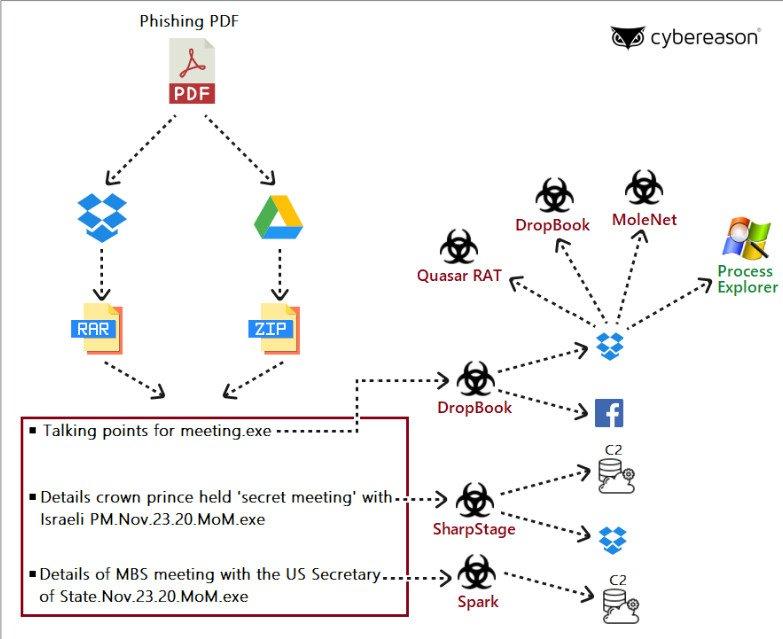
The Molerats group in their new attacks , is using two new back doors , one is SharpStage and the other DropBook . To these we have to add a malware downloader that we did not know before, and that has the name MoleNet . This malware aims to avoid detection and removal efforts by using the Dropbox and Facebook services to steal data and receive instructions from operators. These two back doors then run Dropbox to extract stolen data.
It was first tested with an email that attracted the attention of political figures and government officials in the Middle East. The deception culminated when they ended up downloading that malicious document. In this case, it was a PDF with alleged conversations between the Israeli prime minister and the crown prince of Saudi Arabia.
The operation of the hoax was based on a document that offered a summary of the content, and induced the victim to enter the password to obtain all the information and that was stored in Dropbox or Google Drive. The attack uses three files, two of them are the back doors of SharpStage and DropBook that end up calling the Dropbox storage, controlled by the attacker to download other malware. A third was another backdoor called Spark, which they had used in previous campaigns.
Here you have a diagram that shows that everything begins with the PDF document that we mentioned earlier.
The Cybereason Report and Facebook Commands
Cybereason’s report highlights how the Python-based DropBook backdoor is used. In this case, it differs from other tools from the Molerats group in that it only receives instructions through fake accounts on Facebook and Simplenote (an IOS app for taking notes). The attackers are going to control the back door through some commands published in a Facebook post. Also, they use the same procedure to provide the necessary token to connect to the Dropbox account. Then we have Simplenote that acts as a backup if the situation occurs that the malware cannot retrieve the Facebook token.
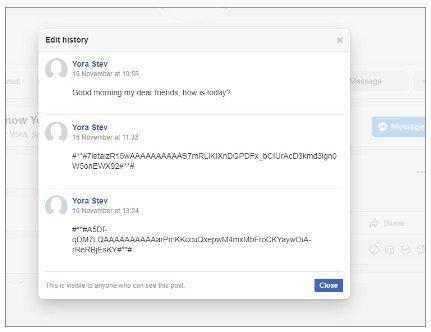
It should be noted that since legitimate commands are being used, eliminating the attacker’s communication with the malware becomes a more difficult challenge.
SharpStage tailgate and more
Now we are going to continue talking about the malware that affects Google and Facebook. DropBook that we talked about earlier was based on Python. However, the SharpStage backdoor is written in .NET and relies on a traditional command and control (C2) server. In that sense, Cybereason discovered three variants of this malware that were in constant development. Thus, all these variants of SharpStage share these functionalities such as:
- Taking screenshots.
- Running arbitrary commands to run PowerShell and WMI commands.
- Unzip the data received from C2 (payload, persistence module).
- A Dropbox API for data downloading and exfiltration.
One point to highlight is that it uses a code that verifies if the compromised machine has the Arabic language installed. Thus, the cybercriminal bypasses computers that belong to unimportant people and the majority of sandboxes.
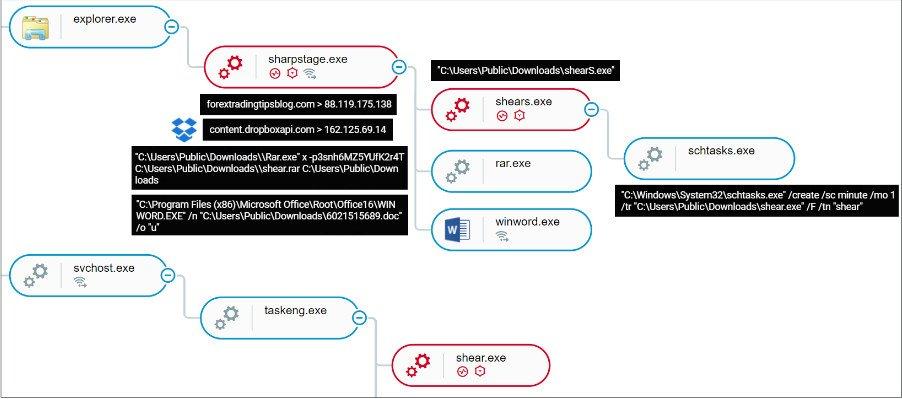
Lastly, we have the third malware that Cybereason discovered called MoleNet. It can use WMI commands to profile the operating system, check for debuggers, reboot the machine from the command line, and load details about the operating system.
