The DHCP protocol is one of the most used by routers, both domestic and professional, in addition, by default any wired or WiFi client is configured to obtain an IP address by DHCP. Although we are continuously using DHCP, surely you do not know exactly what it is for, its functionalities and also how it works and what messages are exchanged between the server and the clients. Today in this article we are going to explain everything you need to know about the DHCP protocol.
What is this protocol and what is it for?

The DHCP protocol (Dynamic Host Configuration Protocol ) or also known as “Dynamic Host Configuration Protocol”, is a network protocol that uses a client-server architecture. Therefore, we will have one or more DHCP servers and also one or more clients, which must communicate with each other correctly so that the DHCP server provides information to the different connected clients. This protocol is responsible for dynamically and automatically assigning an IP address, either a private IP address from the router to the computers on the local network, or also a public IP by an operator that uses this type of protocol for the connection establishment.
When we have a DHCP server running, all the IP addresses that it has provided to different clients are stored in a list where the IP that has been provided (logical address) and the MAC address (physical address of the network card) are listed. . Thanks to this listing, the DHCP server makes sure not to provide two different computers with the same IP address, which causes chaos on the local network. As the server assigns IP addresses, it also takes into account when a certain time passes and they expire, leaving it free for another client to obtain this same IP address. The DHCP server will know at all times who has been in possession of an IP address, how long it has been, and when it has been assigned to another client.
The DHCP protocol includes several forms of assigning IP addresses, depending on the configuration we make and the scenario, we can use one form of assignment or another:
- Manual or static : the DHCP server will allow us to configure a list of IP-MAC pairs in order that a specific IP address is always provided to a client, and that this address never changes.
- Automatic : The DHCP server is responsible for providing an IP address to the client making the request, and it will be available to this client until it is released. There are routers that are internally configured to provide private IP addresses sequentially, however, there are firmwares that are designed to provide a specific IP address within the range and that is not sequential, based on an internal algorithm and the MAC address that is used. have connected.
- Dynamic : This method allows dynamic reuse of IP addresses.
Although the DHCP protocol is well known for providing the IP address, subnet mask and gateway, three basic and fundamental parameters, it is also capable of providing other information for clients, such as the following parameters that are configurable and optional :
- Primary and secondary DNS server.
- DNS name.
- MTU for the interface.
- NIS domain and server.
- NTP servers.
- WINS name server for Windows.
- Other advanced options, all this is in RFC2132 .
A very important aspect is that, if a Windows system is not able to obtain an IP address through the DHCP client on a network, a process called APIPA (Automatic Private Internet Protocol Addressing) is started. This APIPA process used by operating systems when an IP address cannot be obtained by DHCP, this protocol is in charge of assigning a class B private IP address in the 169.254.0.0/16 range with its corresponding subnet mask 255.255.0.0. This addressing block is known as “link-local” for IPv4 networks. Although the operating systems self-configure this private IP address, every 5 minutes they will check again if there is a DHCP server on the network to provide them with a typical class A, B or C private IP address. When the DHCP server does not work or we do not have it configured, you can check the IP address that is automatically configured if we consult the private IP that we have on our computer.
Once we know what the DHCP protocol is and its main characteristics, we are going to see how it works and what messages are exchanged.
Operation and exchange messages
The communication between the DHCP server and the DHCP clients that we have connected to the network is done through the UDP protocol, a protocol that we already know from other articles and that is a non-connection-oriented protocol. In the case of the DHCP server we use the UDP protocol on port 67, in the case of clients we use the UDP protocol on port 68. If we have a firewall blocking these ports, either on the server or on the client, we must review it and add a rule to accept these ports for origin and / or destination, otherwise the service will not work, and we will not be able to obtain the IP addresses automatically.
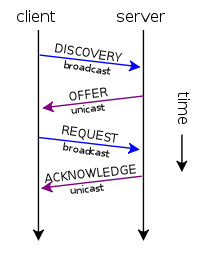
When we connect a computer for the first time to the network, it does not have IP addressing, therefore, we will have to “search” for the DHCP server throughout the network, since we do not have information about the ARP protocol at first. For this reason, the first thing the client will do is send a DHCP DISCOVERY with source IP address 0.0.0.0 and destination IP address 255.255.255.255, which is the global broadcast IP. Of course, a UDP datagram is sent, with source port 68 (client) and destination port 67 (server). This communication is broadcast in the network, and internally it can be configured to receive the OFFER by broadcast or unicast, although it is generally unicast in the OFFER.
If a server exists and is working properly, it will send you a response called DHCP OFFER . This is the response datagram from the server to the client before the request to obtain parameters through the protocol. In this case, the source IP address will be that of the server itself, which generally also acts as a router, the destination IP will also be 255.255.255.255, the source port 67 and the destination port 68. In this package we will have the private IP address that can be provided and is linked to the MAC address of the computer. This communication is generally unicast, although it can optionally be broadcast.
Once the client receives the OFFER, it will send a DHCP REQUEST back. In this case the client selects the configuration received by the OFFER and once again the client requests the IP that the server previously indicated. This communication is also broadcast, because it does not yet have a valid private IP address.
Lastly, the server will send a DHCP ACK to the client, telling it that it has received it correctly and includes all the information that we have configured on the server, such as the duration of the connection, information about the DNS servers and more. With this last process, all the steps of the process are completed, the protocol will also wait a certain time until the DHCP client configures its interface correctly with the negotiated parameters. Once the client obtains the IP address, the client will begin to receive information from the ARP protocol with all the computers on the local network, in order to prevent possible IP address conflicts or overlapping of groups of addresses from DHCP servers. In case of encountering a problem, the client will send the server a DHCPDECLINE message indicating that the address is already in use.
Once we have seen how the DHCP protocol works, we are going to explain what attacks exist and how to avoid them.
Attacks that exist on DHCP
The DHCP protocol does not use any type of authentication, for this reason it is very vulnerable to attacks and there are different types of attacks that we will be able to carry out.
A very common attack is to configure a rogue DHCP server to provide “false” or “malicious” information to clients. When we connect a rogue DHCP server on a local network that already has a legitimate DHCP server, clients will get the IP address, DNS, and other information the first time they respond. For this reason, a malicious user could set up a ” Rogue DHCP Server ” on the network, to gain control of the addresses of various clients. When a cybercriminal installs Rogue DHCP, they do so for several reasons:
- Perform a denial of service attack on the network : If the client or clients obtain this address, they can “cut off” the Internet connection. In this way, clients will not have access to the Internet or to the local network.
- Man in the Middle attack : having total control over the addressing and DNS servers, it is not even necessary to do an ARP Spoofing attack because we will have total control of the entire network, and we will be able to forward clients to malicious websites by modifying the servers DNS from our own DHCP server that we just installed. An illegitimate DHCP server can provide false DNS server information to different clients. Of course, they will not only access malicious websites, but you can also easily spy on connections because we will be the gateway.
To mitigate this attack, it must be ensured that there is no Rogue DHCP in our local network, and that is where the “DHCP Snooping” built into the switches comes into play. This technology allows blocking DHCP Offer and DHCP Ack messages from ports where it is not allowed, that is, where the legitimate server is not. This way, even if the fake DHCP server gets the messages, it will never be able to reply and the clients on the local network will remain safe. In the following diagram you can see how DHCP Snooping works:
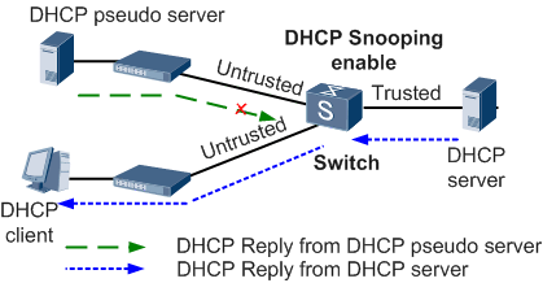
Another very common attack on DHCP servers, due to the fact that we do not have any type of client authentication mechanism, is to make dozens of requests for IP addresses, in order to exhaust the server’s IP address storage, by presenting new customer identifiers each time a request is made. This would cause the server to “crash” and be unable to provide further addressing. There are some mitigation mechanisms, especially at the level of Internet operators that make use of DHCP, such as RFC3046 using tags which is used as an authorization token, we also have RFC3118 which is to authenticate messages but has not been widely used. With the release of the 802.1X protocol to authenticate wired clients, these RFCs were pushed into the background.
Regarding the local network, the most important thing is to have DHCP Snooping well configured to avoid Rogue DHCP, in this way, we will be protected.
What is static DHCP or “Static DHCP”
The static DHCP functionality, also known as “Static DHCP” or “Static Mapping”, is the possibility of specifically configuring a certain client, based on its MAC address or its “Client identifier”. Thanks to this function, we can set specific parameters for this specific client, such as, for example, the same private IP address always so that it never changes. Other options that we can configure are the host name, configure the DNS and WINS servers, the domain name, the NTP, TFTP, LDAP servers and other information that the DHCP servers can also provide.
The operation of the Static DHCP is very simple, we must put the MAC or client identifier in the corresponding section, then we will configure a specific IP address and the rest of the parameters that we want the client to have. Below, you can see all the configuration options available in a pfSense operating system.
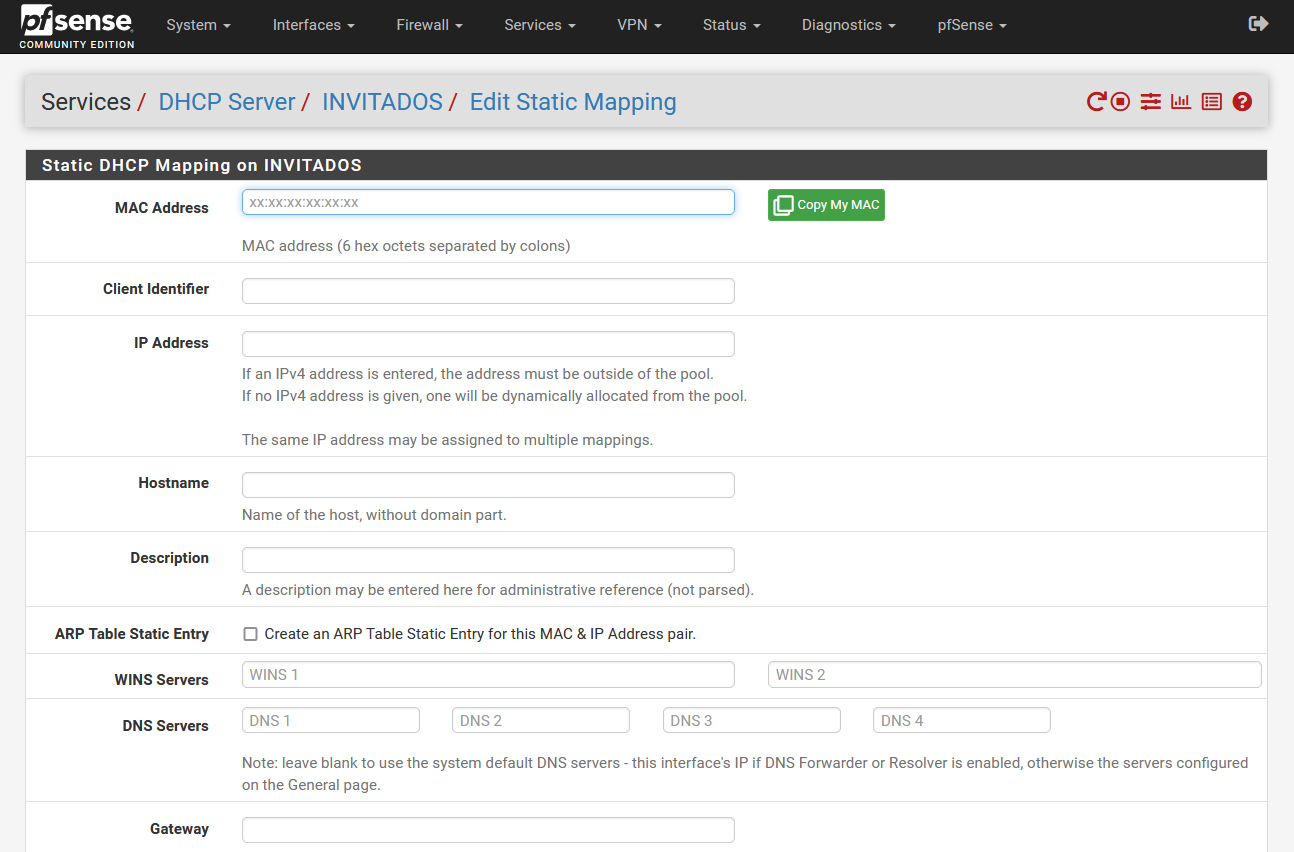
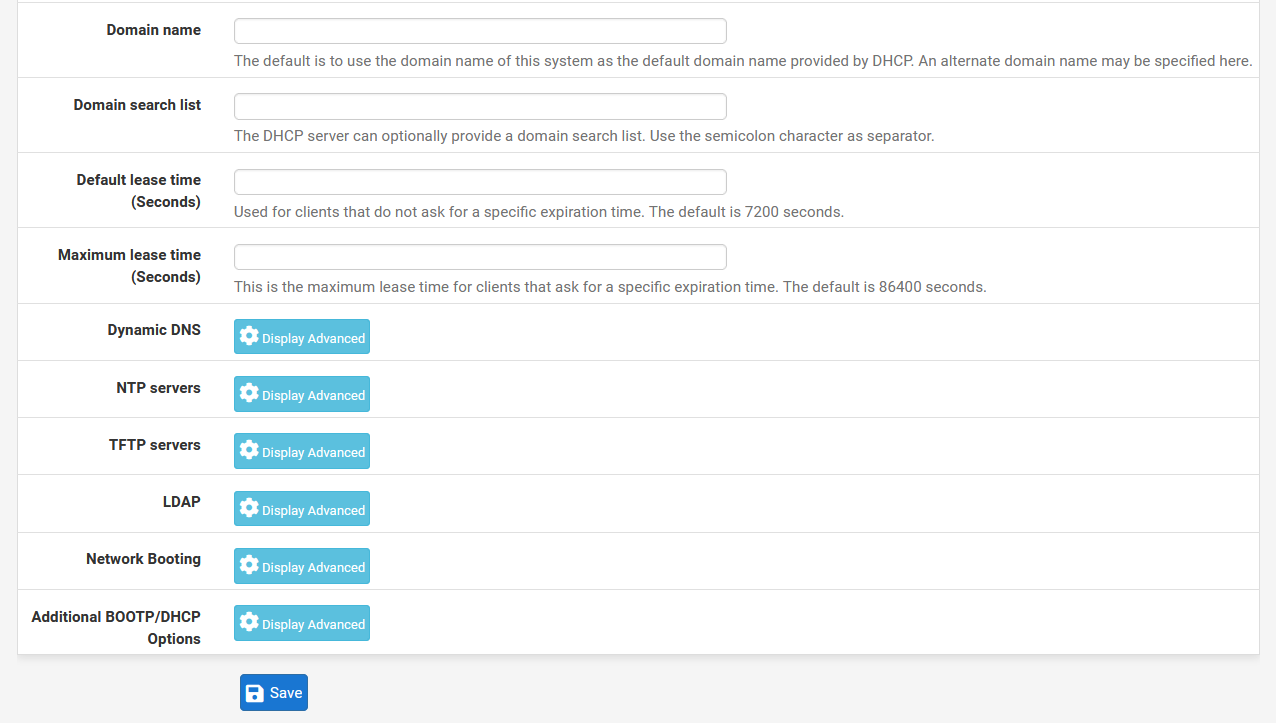
Once we have seen how Static DHCP can be configured, we are going to see the global configuration of a DHCP server.
DHCP server global settings
Let’s take the DHCP server of the pfSense operating system as an example. This operating system and also many routers, allow us to set up a DHCP server for each subnet that we have configured. Depending on the firmware, we will have more configuration options or fewer configuration options, so we must take it into account.
In the case of pfSense, we can enable or disable the DHCP server, ignore or not the requests of the BOOTP protocol, we can also make an access control list so that clients can or cannot obtain addresses, we can also configure the range of IP addressing Within the subnet that we have configured, in fact, we will have the possibility of creating additional “pools” without any problem. Of course, we will also have to fill in the information for the DNS and WINS servers, as well as the other advanced options if we need it.
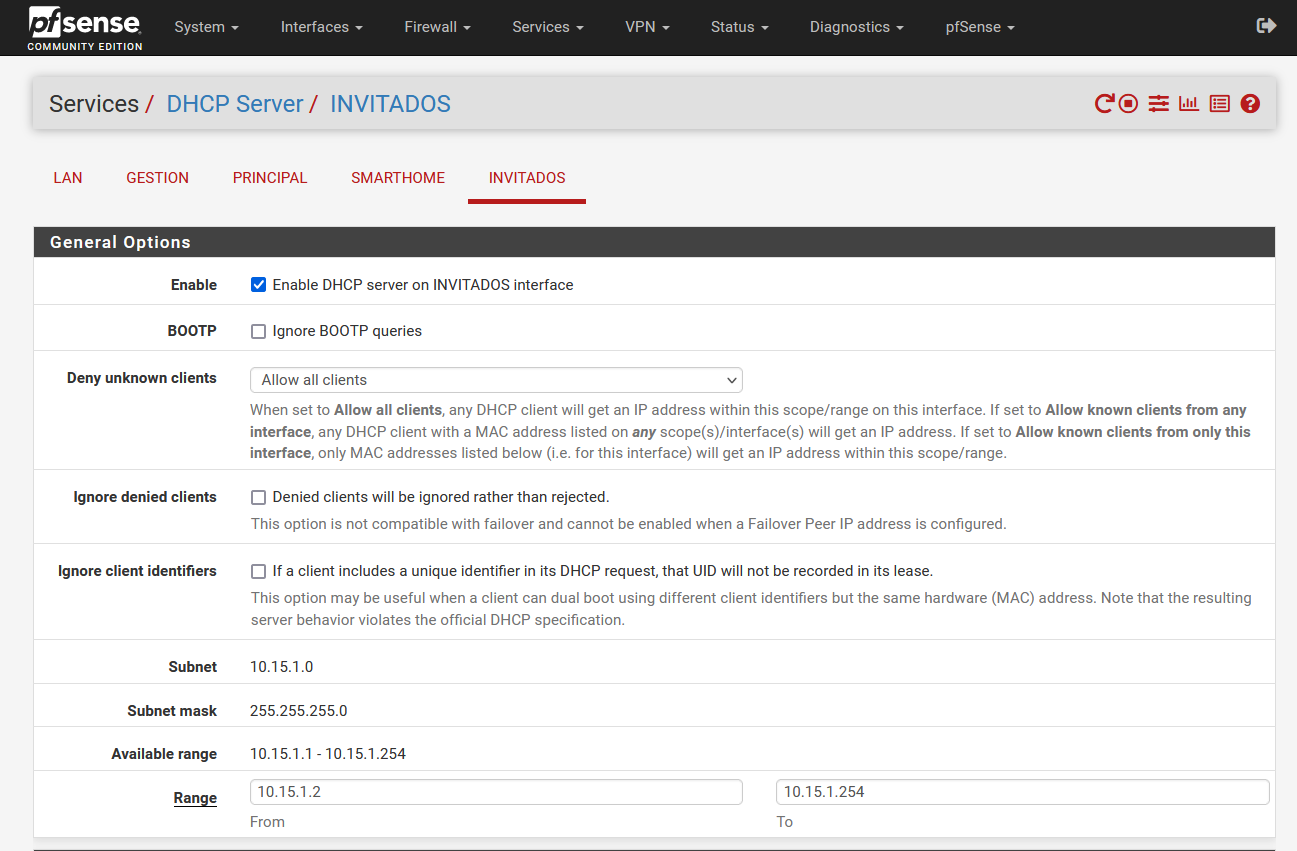
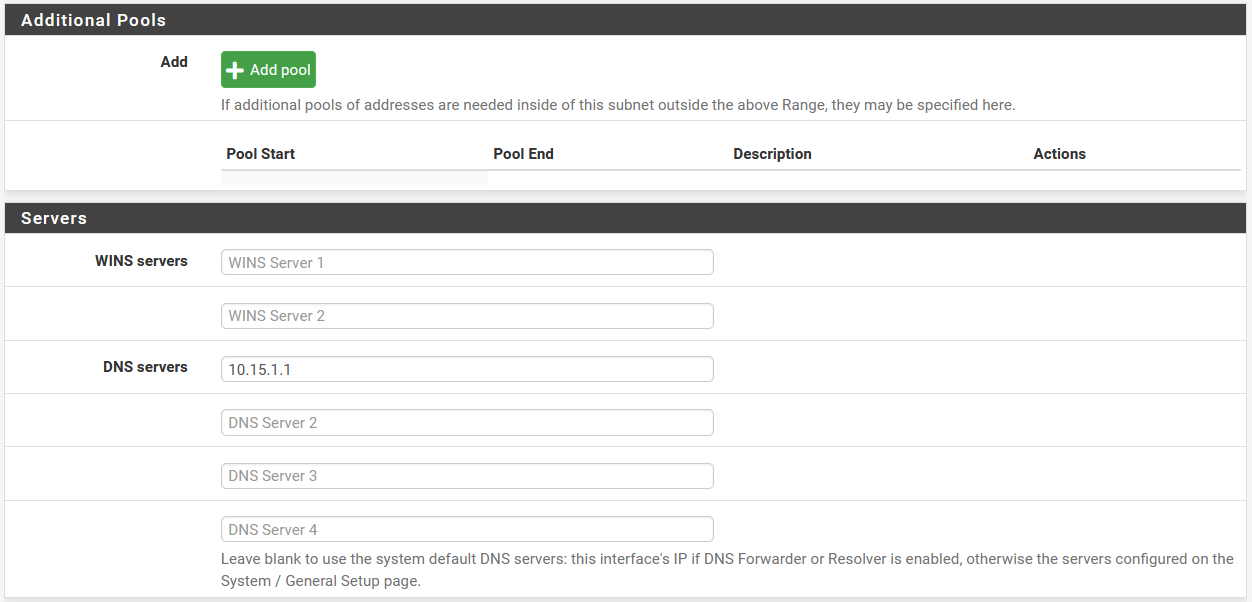
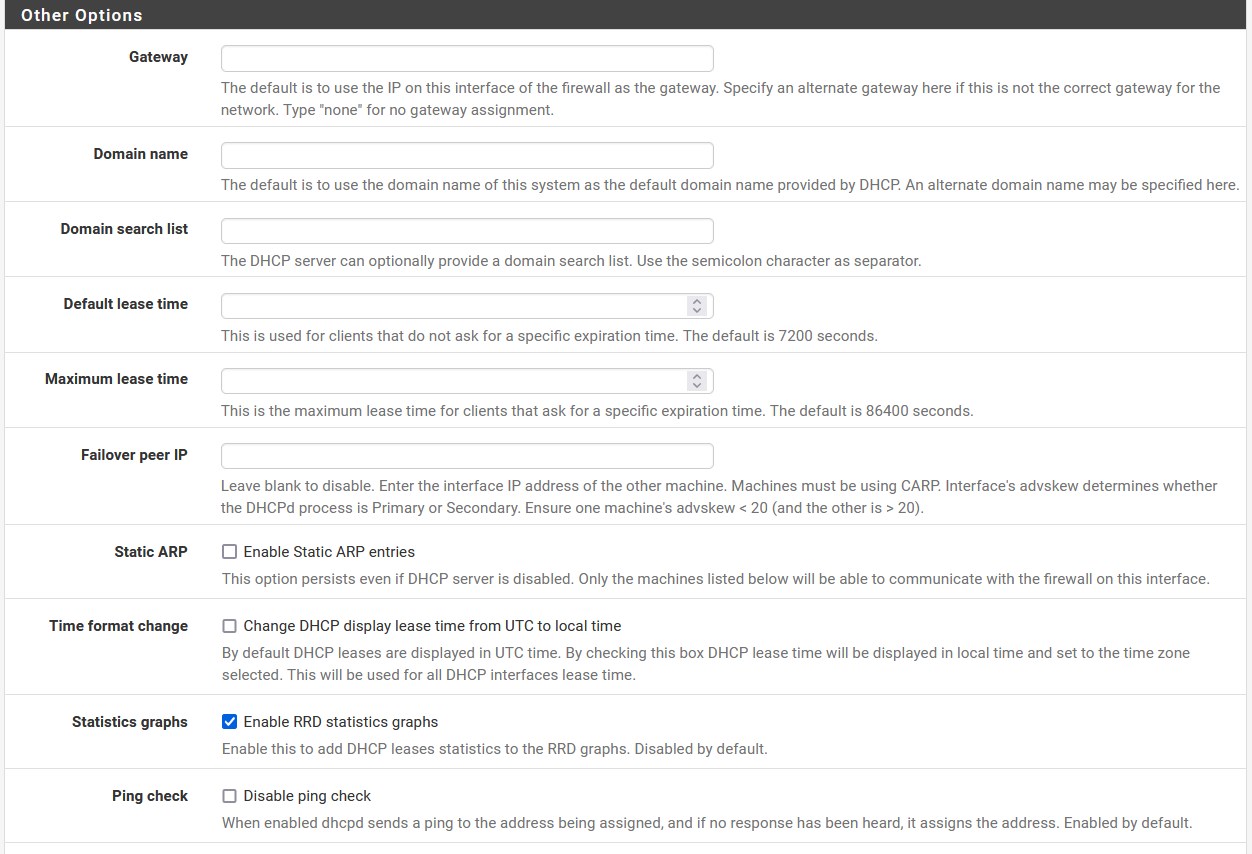
In the previous screenshots you can see that we have the possibility to configure the DHCP server in a pfSense in a very advanced way, generally professional routers have all these configuration options, unlike home routers that are much more basic and do not have so many configuration options. For example, we can configure the NTP, TFTP and even the LDAP if we want, in addition, we will also have the possibility of displaying these options to configure it in detail.
As you have seen, the DHCP protocol is widely used by all of us to obtain the IP addressing and other information necessary for the proper functioning of the local network, in addition, we must not forget the attacks and how we can protect ourselves from them, finally, remember We have the Static DHCP functionality so that the server always provides us with the same IP address.