The security of wireless networks is crucial in a future (and a present) in which they have more and more specific weight among home users, but also in business environments. Both WiFi and Bluetooth have become the star technologies when it comes to connecting wirelessly to both the Internet and other devices. For that reason, any discovery of security breaches or similar problems can be very dangerous and that is what just happened. In fact, researchers at the Technical University of Darmstadt discover how to steal the WiFi password of millions of devices.
Today we know that these researchers, together with those from the University of Brescia, the CNIT and the Secure Mobile Networking Lab, have published a complete investigation that shows that it is possible to “extract” passwords and manipulate traffic on a WiFi chip by attacking Bluetooth components. of a device. At this point one could wonder about the relationship between both technologies and that is precisely what they explain in their research.

Possible large-scale problem in WiFi networks
First of all, we must be clear that modern devices such as smartphones have separate components for Bluetooth, WiFi and mobile connections, each with its own security implementation. However, these components share resources on many occasions , such as antennas or wireless spectrum. This seeks to make the SoCs more efficient for communications and power consumption.
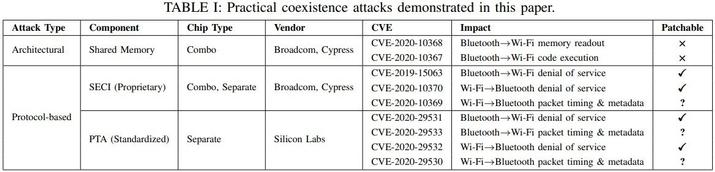
The problem is that these security researchers have managed to take advantage of these shared resources as “bridges” to launch attacks of the type of lateral escalation of privilege to exceed the limits of these wireless chips. This includes remote code execution, denial of service, and other implications.
All exploited vulnerabilities have already been cataloged and manufacturers will have to put the batteries to launch new firmwares . However, some will even need hardware revisions, leaving many devices with security concerns until they are retired:
- CVE-2020-10368: WiFi unencrypted data leak (architectural)
- CVE-2020-10367: Wi-Fi code execution (architectural)
- CVE- 2019-15063: Wi-Fi denial of service (protocol)
- CVE-2020-10370: Bluetooth denial of service (protocol)
- CVE-2020-10369: Bluetooth data leak (protocol)
- CVE-2020-29531: WiFi denial of service (protocol)
- CVE-2020-29533: WiFi data leak (protocol)
- CVE-2020-29532: Bluetooth denial of service (protocol)
- CVE-2020-29530: Bluetooth data leak (protocol)
Among the affected devices, which mount chips from Broadcom, Silicon Labs and Cypress , we have the Nexus 5, iPhone 6, Raspberry Pi 3, Samsung Galaxy S6, iPhone 7, Samsung Galaxy S8, Samsung Galaxy S10, iPhone X, MacBook Pro of 2019 o iPhone 11 and 12. Each device allows one or more types of attacks.