Cryptography was born from the need to make a data transmission private, so on the basis, cryptography is the method that is applied to a message to encrypt and decrypt it in such a way that only the plaintext is visible to the sender and the receiver of said message, that it is totally unreadable for anyone who intercepts it in the middle of the transmission, and in turn, that it is safe enough to withstand any attack that could compromise the information that is being transmitted. There are two types of encryption depending on the type of your keys. Cryptography whose algorithms use only one key, or symmetric cryptography , and the cryptography of two-key algorithms, asymmetric cryptography . Here we will be able to see how each one works and what their properties and differences are.
Symmetric cryptography or one-key cryptography
Symmetric cryptography is the oldest cryptographic technique out there, but it still offers a high level of security. It is based on the use of a single secret key that will be in charge of encrypting and decrypting the information, whether it is information in transit with protocols such as TLS, or information on a removable storage device. Symmetric cryptography was the first method used to encrypt the information, it is based on the fact that the same password will be used for both encryption and decryption, therefore, it is essential that all users who want to encrypt or decrypt the message, have this secret key, otherwise they won’t be able to. Thanks to symmetric cryptography, we can make communications or store files safely.

Encryption using a symmetric key means that at least two users must have the secret key. Using this key, all messages transmitted through the insecure channel, such as the Internet, will be encrypted and decrypted, hence we need data encryption to maintain confidentiality. Any user who wants to access the encrypted message must have this decryption password, otherwise it will be unreadable.
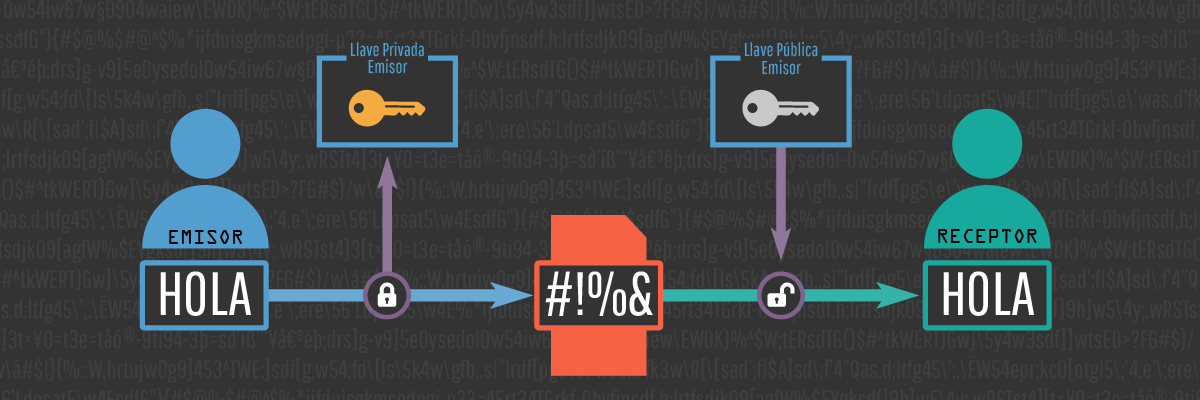
The method to encrypt the data is based on the fact that the sender will encrypt the message with his private key, he will send it through the insecure channel, and the recipient will have to decrypt it with the same password or private key that the sender has used.
There are several points that a symmetric key algorithm must meet in order to be secure in use:
- Once the message is encrypted, neither the encryption key nor the clear message can be obtained by any method.
- If we know the clear message and the encryption, more time and money should be spent in obtaining the key to access the clear message, than the possible value of the information that is stolen.
Brute force attacks are the real enemy of symmetric cryptography algorithms , it must be borne in mind that these algorithms are public and that their strength depends directly on how complex the algorithm is internally, and also on the length of the key used to prevent these attacks.
The most important thing in symmetric cryptography is to protect the private key or password. The main problem that arises is the distribution of this private key or password to all users, both senders and receivers of the information, to encrypt and decrypt the information in the message. It is essential that all users of the system protect the private key or password as best as possible, because if it falls into the wrong hands, the entire system would be compromised, having to generate a new key and redistribute the private key to the different participants.
One of the differences we have between symmetric and asymmetric cryptography is that in symmetric all users have the same encryption / decryption key, if we have more than one communication channel, we will have as many private keys as parallel communication channels. However, in the asymmetric ones, each user will have a pair of keys (public and private) for all communication channels, no matter the number of secure channels to maintain, we only have to protect the private key.
The advantage of symmetric cryptography algorithms is that they are fast, very fast, in addition, in recent years, hardware encryption acceleration has been incorporated into computer processors, servers, routers and other devices, in this way , we can transfer data via VPN really fast. The speed also depends on the symmetric encryption algorithm to be used, for example, AES and ChaCha20 are two of the fastest and most secure that we have today, but the hardware of the equipment influences a lot.
Now we are going to talk in detail about two symmetric algorithms that are used continuously today, either in HTTPS connections with TLS 1.2 and TLS 1.3, in virtual private networks with IPsec, OpenVPN or WireGuard, and also in other areas where data encryption is used, as in VeraCrypt.
AES (Advanced Encryption Standard)
The symmetric AES algorithm was in charge of replacing DES , and is currently used in all secure channels and protocols such as TLS, FTPES, virtual private networks and much more. AES encryption can be used in both software and hardware, AES is a block encryption algorithm, the fixed block size is 128 bits . The length of the key can be chosen, and we have 128, 192 and 256 bits available , being the length of 128 bits the standard, but 256 bits are also widely used.
A very important aspect is that AES is responsible for generating a 4 × 4 matrix, and then a series of encryption rounds are applied to it. For a 128-bit key 10 rounds of encryption are applied, for a 192-bit key 12 rounds are applied, and for a 256-bit key the rounds applied are 14. From the beginning, many cryptographers doubt its security, and it is that attacks have been recorded on a number of rounds close to the final round, specifically 7 rounds for 128-bit keys, 8 rounds for 192-bit keys and 9 rounds for 256-bit keys have been decrypted.
Encryption mode is the way the AES-encrypted message blocks are handled, there are different types, and each of them works in a different way. For example, there is AES-CBC, AES-CFB and AES-OFB , we are going to explain what exactly this is that appears in cryptographic libraries such as OpenSSL and LibreSSL.
- CBC (Cipher-block chaining) – This encryption mode has been widely used in conjunction with a hash function to verify the authenticity of data, and is still used today. This encryption mode consists of XORing each block of plaintext with the previous encryption block. Each encrypted block depends on the previous processed up to that point. To perform this XOR option with the first block of text, an initialization vector IV is used. This encryption mode is performed sequentially, it cannot be treated in parallel to increase performance in data encryption / decryption.
- OFB (Output feedback) : in this mode the secret key is used to create a pseudo-random block to which the XOR operation with the plaintext is applied to create the ciphertext. In this case, an initialization vector is also required, which must be unique for each encrypted message. If a different IV is not used, the security of the system is compromised. It also cannot be parelized.
- CFB (Cipher feedback) : it is done the same as in OFB, but to produce the keystream it encrypts the last block of encryption, instead of the last block of the keystream as OFB does. Encryption cannot be parallelized, however decryption can.
- GCM ( Galois / Counter Mode) : This encryption mode is one of the best in terms of security and speed, GCM allows parallel processing and is compatible with AES-NI processors to accelerate data encryption / decryption performance. This encryption mode is AEAD, in addition to encrypting the data, it is also capable of authenticating it and verifying the integrity of the data, to ensure that it has not been modified. GCM can also accept random initialization vectors.
As you have seen, AES is currently one of the most important and widely used symmetric encryption algorithms in the world, however, the most recommended encryption mode is AES-GCM since it incorporates AEAD.
ChaCha20
The ChaCha20 algorithm is a symmetric encryption algorithm that supports 128-bit and 256-bit and high-speed keys, unlike AES which is a block cipher, ChaCha20 is a stream cipher. It has similar characteristics to its predecessor Salsa20 but with a primitive function of 12 or 20 different rounds. Its code was published, standardized by the IETF in RFC 7539 and in software implementations, it is much more efficient and faster than AES, so it has quickly made a place within the most used algorithms today.
To find out why it has become so famous, we are going to put Google in the middle so that everything can be understood much faster. HTPPS connections are focused on offering maximum security on the websites that we visit every day, it was the next step of the HTTP protocol which had no protection whatsoever. Encryption, however, varies from browser to browser. Until a few years ago, Chrome for Android has been using AES-GCM as its symmetric encryption algorithm, however, Google has been working on more current, secure and faster encryption for many years.
The jump in popularity occurs when, after its launch in the desktop version of Chrome, the new ChaCha20 for encryption and Poly1305 for authentication arrives on Android. A titanic job that translates into a symmetric algorithm that offers more security, and that is immune to various types of attacks. However, the most remarkable thing is that it achieves a performance three times higher than somewhat older protocols such as AES, in this way, the capabilities of the CPU are also better used and a reduction of 16% in the width of the band used, which makes it possible to take advantage of the connection even more.
ChaCha20 is widely used in HTTPS connections, in SSH connections to manage servers, and even the popular WireGuard VPN protocol uses only ChaCha20 for symmetric data encryption. It is very possible that soon we will also see ChaCha20 in IPsec connections, in the meantime, you should use AES-GCM whenever possible.
So far the explanation of symmetric cryptography, we have commented on the two algorithms that are frequently used today, there are many more that in the past were very relevant, especially for the development of current ones, since the bases of the new ones are they settled on the experience of the old, their mistakes and their advantages. Algorithms such as DES, 3DES, RC5 or IDEA paved the way for the new ones so that today we have really strong encryption algorithms with the capacity to withstand attacks and protect all our information from unwanted and malicious hands.
Asymmetric cryptography or public key cryptography
Asymmetric key cryptography is also known as a public key, it uses two different keys at each end of the communication to encrypt and decrypt it . Each user of the communication will have a public and a private key. The private key will have to be protected and kept by the user himself, it will be secret and must not be known by absolutely anyone, nor should it be sent to anyone. The public key will be accessible by all users of the system who want to communicate.
The strength of the system by which this type of asymmetric algorithm is safe is that it is based on mathematical functions which are easy to solve in one sense , but whose resolution in the opposite direction is extremely complicated , unless the key is known. . Public and private keys are generated simultaneously and are tied to each other. The relationship between the two must be very complex, so that it is very difficult for us to obtain a key from the other, in this case, to obtain the private key since the public key is known by everyone connected to the system.
The pairs of keys have several and very important functions, among which we highlight:
- Encrypt the information.
- Ensure the integrity of the transmitted data.
- Guarantee the authenticity of the issuer.
Asymmetric key encryption
If a person with a key pair encrypts a message with the recipient’s public key, that message can only be decrypted with the associated private key. If we encrypt a message with the private key, we will not be able to decrypt it with the private key itself, we must use the public one (in this case it is not considered encryption, but the authenticity of the sender is checked, with this we will verify that the sender is who really says be).
The mathematical structure of how asymmetric encryption works is this:
- Message + public key = Encrypted message
- Encrypted message + private key = Decrypted message
- Message + private key = Signed message
- Signed message + public key = Authentication

As we have commented before when talking about symmetric key cryptography, symmetric encryption provides confidentiality (only the recipient can read the message). Asymmetric cryptography provides other properties: authenticity, integrity, and non-repudiation. For an algorithm to be considered safe, it must comply with the following:
- If the ciphertext is known, it must be very difficult or nearly impossible to extract the plaintext and private key by any method.
- If the plaintext and the encryption are known, it should be more expensive to obtain the private key than the plaintext .
- If the data has been encrypted with the public key, there should only be a private key capable of decrypting it , and vice versa.
The advantage of asymmetric encryption over symmetric encryption is that the public key can be known by all users of the system, however, this does not happen with the private key, and as a result of symmetric encryption, both users must know the same key. (and the password must be sent to each of the different users through the established communication channel).
Operation of the symmetric and asymmetric system
The main drawback of this type of encryption is its slowness , the use of this type of keys slows down the encryption process of communication. The solution to this is to use both asymmetric and symmetric encryption (as protocols such as IPSec or OpenVPN do for virtual private networks, HTTPS for secure web connections, or in SFTP / FTPES connections).
This combination of ciphers happens as follows. We create the symmetric algorithm key, encrypt it with the recipient’s public key, send the encrypted data over the insecure communication channel, and then the recipient will decrypt the data using their private key. With the symmetric algorithm key in the colon, this is when communication using symmetric encryption can begin, which makes communication much faster than if we used only asymmetric cryptography in all communication.
The clear example of where this type of combined method is used are VPNs, such as OpenVPN or IPsec, in which the session key that is known to users is regenerated every so often to further increase communication security, without entailing a significant delay in data transfer.
Challenge-Response
To increase security, this method verifies that the sender is really who he claims to be , for this a text is sent to the sender and he will encrypt it with his private key (what he is really doing is signing it), the sender will send us the encrypted text (signed) and we will decrypt the key (we will verify the signature) taking advantage of the fact that we have the public key of the issuer, and finally, we will compare that the message obtained is the same that we sent previously.
If a user impersonates the real issuer, they would not have the private key, so the “challenge” would not have been successful and the data would not be communicated.

Digital signature
The digital signature allows the recipient of a message that the origin is authentic , we can also check if the message has been modified. Falsifying a digital signature is almost impossible unless they know the private key of the person signing (and we have already said before that the private key must be saved, and that no one should know it). Here are the two phases for the realization of the digital signature:
- Signature process: the sender encrypts the data with the private key and sends it to the receiver.
- Verify the signature: the receiver decrypts the data using the sender’s public key and verifies that the information matches the original data (if it matches, it has not been modified).
In digital signatures, hash functions such as SHA2-256 and SHA2-512 are used since, as we have explained previously, asymmetric encryption is slow. The sender of the communication will apply the HASH function to the original message to obtain the fingerprint. The fingerprint will then be encrypted with the private key and sent to the recipient over the insecure channel for decryption. The recipient will also hash your data and compare the results (the one they got and the one they received). If the result of comparing these data is negative, that is, there are differences between what was obtained and what was received, the information has been altered and the fingerprint data will have changed. If the result is the same, communication will take place without problems.
With all this we have fulfilled:
- Authenticity, the issuer is who they say they are . The signature at origin and destination is the same.
- Integrity, the message has not been modified . What is obtained and what is received is the same.
- No repudiation, the sender cannot deny having sent the message to the receiver . The digital signature does not change.
If we want to introduce confidentiality to the communication, all we have to do is have the sender encrypt the original message with the public key of the receiver.
Asymmetric key encryption algorithms
Now we will list the two main asymmetric algorithms that are used today and we will explain how they work.
Diffie-Hellman
It is not an asymmetric algorithm itself, it is a key establishment protocol, it is used to generate a private key at both ends of an insecure communication channel . It is used to obtain the private key with which the information will later be encrypted together with a symmetric encryption algorithm. The strength of the Diffie-Hellman is that its security lies in the difficulty of calculating the discrete logarithm of large numbers (Diffie-Hellmann also allows the use of elliptical curves).
The problem with this algorithm is that it does not provide authentication, it cannot validate the identity of the users, therefore, if a third user gets in the middle of the communication, they would also be provided with the keys and, therefore, could establish communications with the sender and the receiver impersonating identities. To avoid this, there are several solutions that mitigate and solve the problem, such as making use of digital certificates.
RSA
The asymmetric algorithm par excellence, this algorithm is based on the pair of keys , the public and the private one that we have already talked about previously. The security of this algorithm lies in the problem of factoring very large integers, and in the RSA problem, because fully decrypting a ciphertext with RSA is currently not possible, although partial decryption is possible. Some very important characteristics of RSA is the key length, currently at least a length of 2048 bits should be used, although it is recommended that it be 4096 bits or higher for greater security.
Advantage:
- The problem of the distribution of symmetric keys (symmetric encryption) is solved.
- It can be used to be used in digital signatures.
Disadvantages:
- Security depends on the efficiency of computers.
- It is slower than symmetric key algorithms.
- The private key must be encrypted by some symmetric algorithm.
DSA
This algorithm is also purely asymmetric, a disadvantage of DSA is that it wants much more compute time than RSA for hardware equality. DSA is widely used as a digital signature algorithm, it is currently a standard, but DSA is not used to encrypt data, only as a digital signature. This algorithm is widely used in SSH connections to verify the digital signature of clients, in addition, there is a variant of DSA based on elliptic curves (ECDSA), and it is available in all current cryptographic libraries such as OpenSSL, GnuTLS or LibreSSL. Another feature of DSA is the key length, the minimum key length is 512 bits, although the most common is to use 1024 bits.
Now you know the two types of cryptography and the properties of each one, with this you will know where it is worth using one type and where the other . Over time, these methods will vary or will be updated to more secure ones, since with the growth of computer performance, attacks on this type of security method are enhanced, but right now, those that are in force and continue to be used for not having been ousted yet, they are the ones we have just explained to you.