The pfSense operating system oriented to firewalls and to function as a router, allows capturing all the network traffic in a certain interface that we have configured, both from the WAN and the LAN, and, of course, it also allows capturing the traffic of a certain VLAN if we have them configured on the computer. We will be able to capture traffic in both directions, both in download and upload, and it also allows limiting by IP addresses and even TCP / UDP ports. Today in this article we are going to show you how to capture network traffic to carry out a thorough analysis and see if there is any kind of problem.
Why do I want to capture network traffic?
Taking a network traffic capture is very important to detect possible communication problems. Let’s imagine that a specific computer must send or receive a certain traffic and does not receive it, it is possible that a rule in the firewall is preventing it, or that the problem is not in the firewall but in the switches that we have connected. It is very normal to have the switches configured with certain ACLs to further protect the network, and we could even activate different types of countermeasures for DoS attacks that could occur in the local network. In the event that the traffic is not reaching the pfSense, it is possible that the problem is in the “middle”, that is, in the switches, therefore, it will help us to rule out configuration problems and see all the traffic flow .

If we have some type of communication problem, and we cannot find where the problem may be, we must rule out that it is a problem with the firewall / router itself with pfSense, and then go to review the different switches that we have in between. This is where the «Packet capture» of pfSense comes in, which will allow us to capture all the traffic of a certain network interface.
How “packet capture” works in pfSense
The traffic capture device is installed by default in the pfSense operating system, we will not have to install it through the list of available software that we have the possibility to install. We must go to the ” Diagnostics / Packet Capture ” section to see the available configuration options.
In this section we will have different configuration options, to “fine tune” the packet capturer, something fundamental to not capture absolutely all the network traffic, but only the traffic that we specifically select.
The first thing we must do is the « Interface «, here we must choose the physical or logical interface (if you use VLANs) to use in capturing the packets.
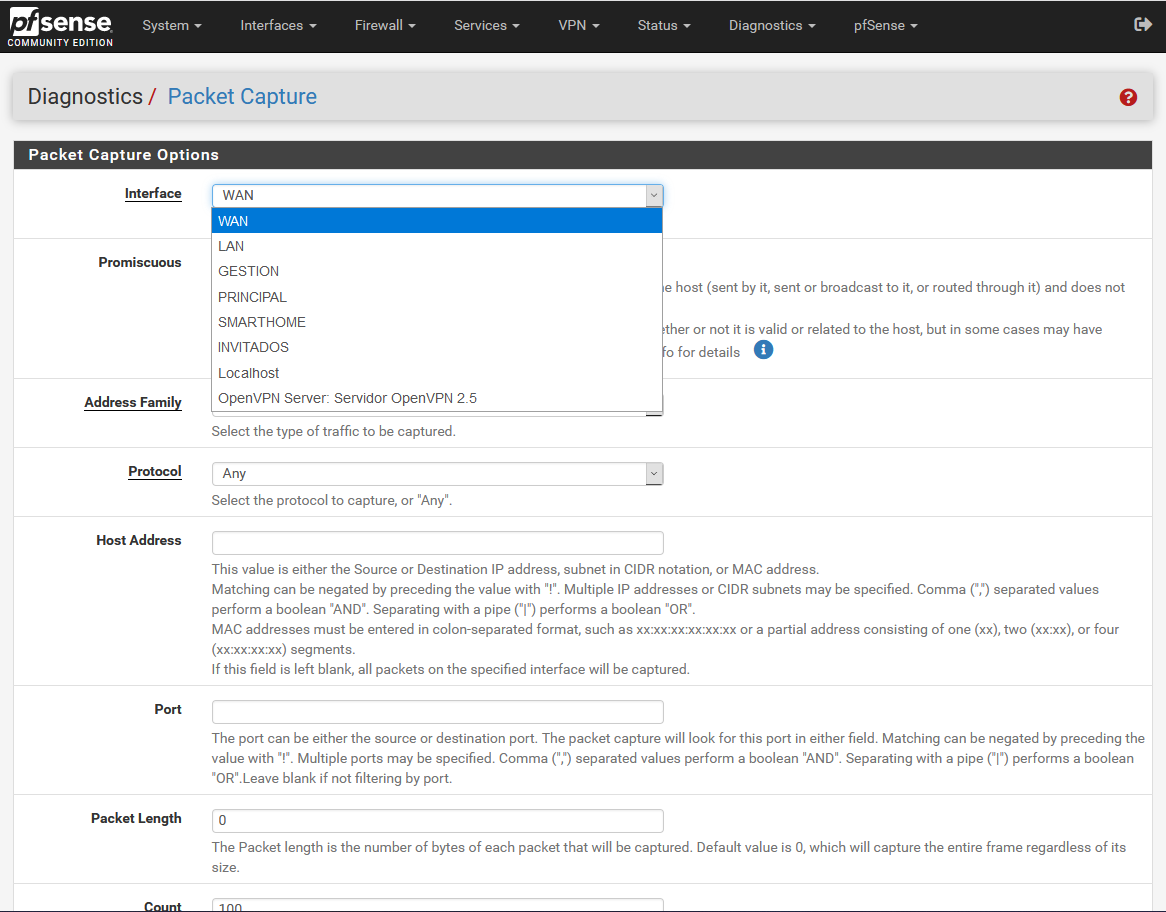
The pfSense operating system allows us to enable “promiscuous mode”. In “non-promiscuous mode” the system will capture only traffic direct to the host that passes through a given interface. In the “promiscuous mode” we will enable the sniffing mode, and it will capture all the information that the network adapter sees, however, it is possible that the hardware you use in pfSense does not support this functionality.
We can also choose and filter if we want IPv4, IPv6 or both network protocols.
Next, we must choose which protocol we want to capture, we can capture any protocol (Any), or filter by ICMP, TCP, UDP and much more.
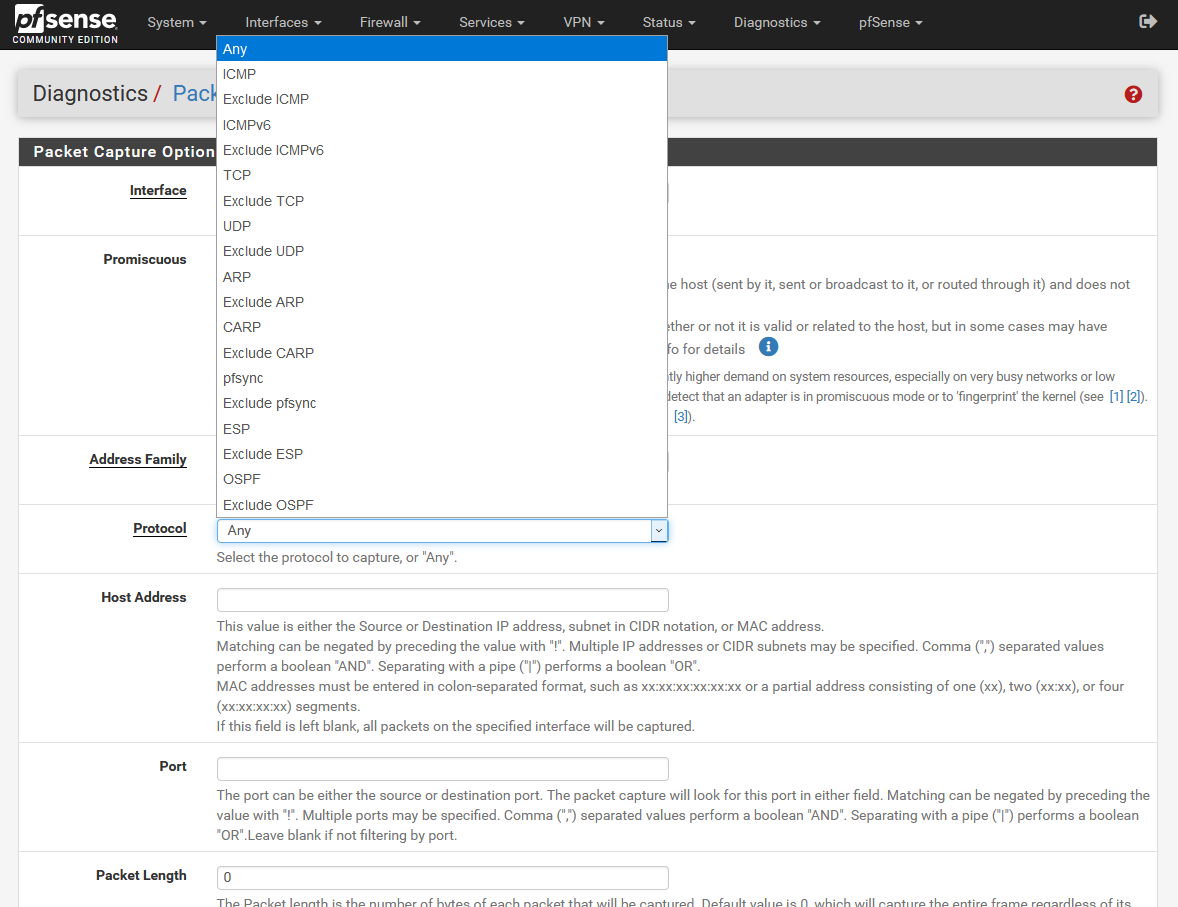
Other available options are the possibility of choosing the “Host address” option. This option allows us to only capture the traffic that has as its origin or destination a specific IP address or MAC address (if it is directly connected to the same subnet). If we do not put anything, it will capture all the packets that travel through the interface, without filtering by IP or MAC at all.
We can also configure the source or destination port if we use TCP and / or UDP, ideal for only capturing the traffic that interests us. All application layer protocols make use of specific source and destination ports, for example, if we want to capture HTTP traffic, we will put port 80 and filter by TCP, since it is what the HTTP application layer protocol uses .
In “Packet Length” we will have to put 0 to capture all the frames and not limit by frame size, and in “Count” it is advisable to put 0 to capture all the traffic until we stop it manually, by default it is the value of 100 which could be very little depending on the equipment in question.
In the “Level of detail” section we can make the network capture shown in the lower part with more or less detail, but in most cases what we will do is download the data capture and examine it carefully in programs like Wireshark.

In our case, we are going to capture the traffic of our smartphone to check what data we are sending to the Internet, we will filter by “Any” protocol and any port, that is, we will capture all the traffic that goes to or comes from 10.11.1.4.
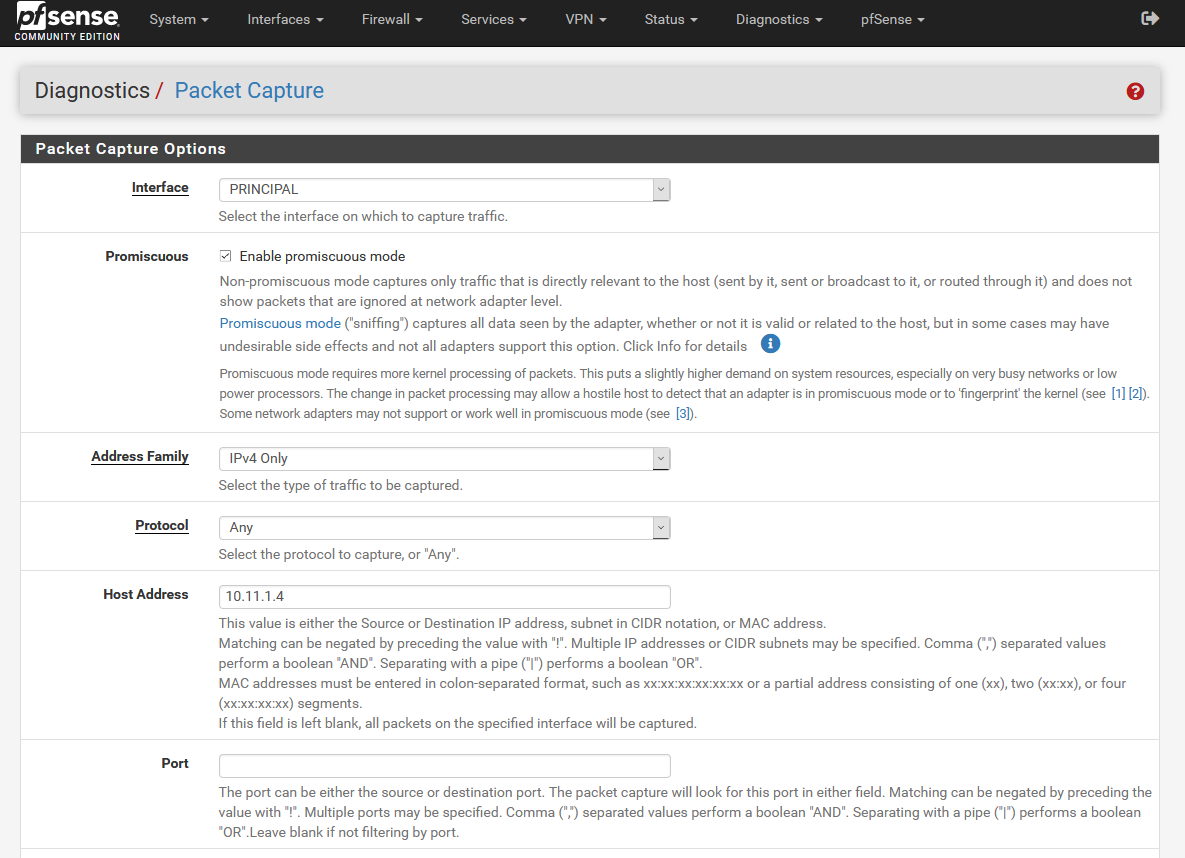
In this example, we will capture with any packet length, but with a maximum of 100 packets. The level of detail is “normal”, and we click on “Start” to begin data capture.
While the packet capturer is running, we will see that it will show us a “Stop” button and just below it we will see “Packet capture is running”.
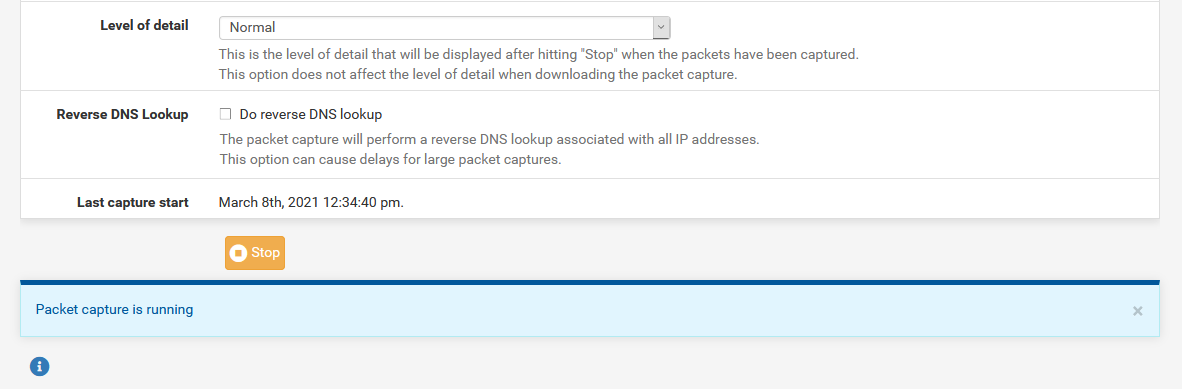
When we click on «Stop», it will show us when the capture has started and when it has stopped. We can see the screenshot just below, but we have very little information because the level of detail was “normal”. In the vast majority of cases, it is best to click on “Download Capture” and download the data capture for further analysis.
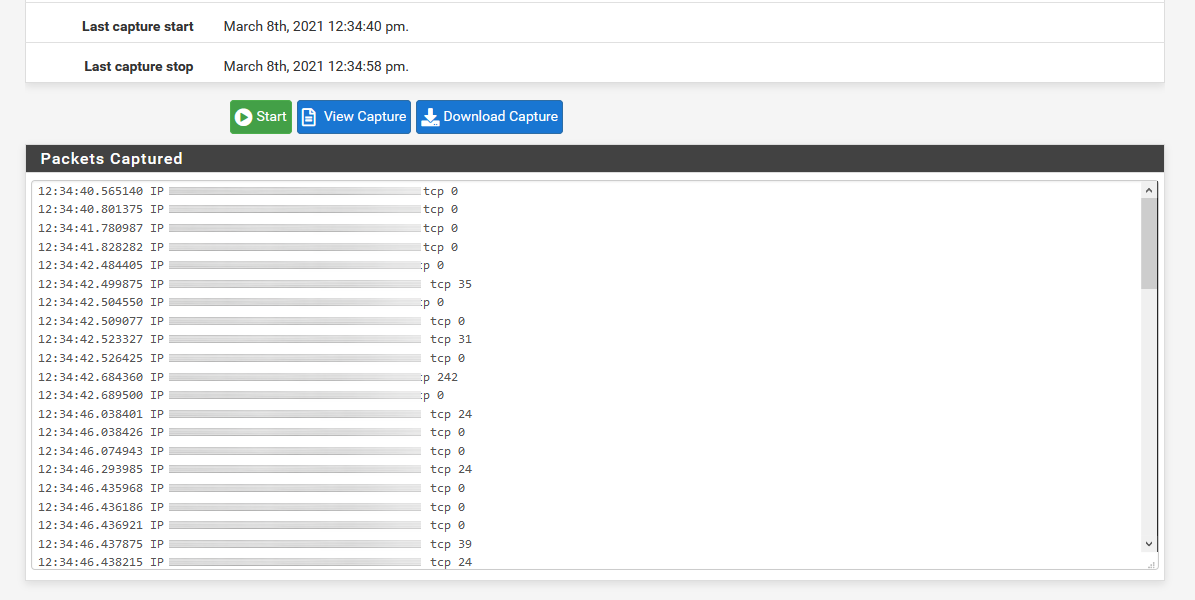
As we have the Wireshark program installed, what we will be able to do is open this capture directly to examine the capture in detail.
As you can see below, we have all the data capture in Wireshark and we can see all the incoming and outgoing traffic to our smartphone.
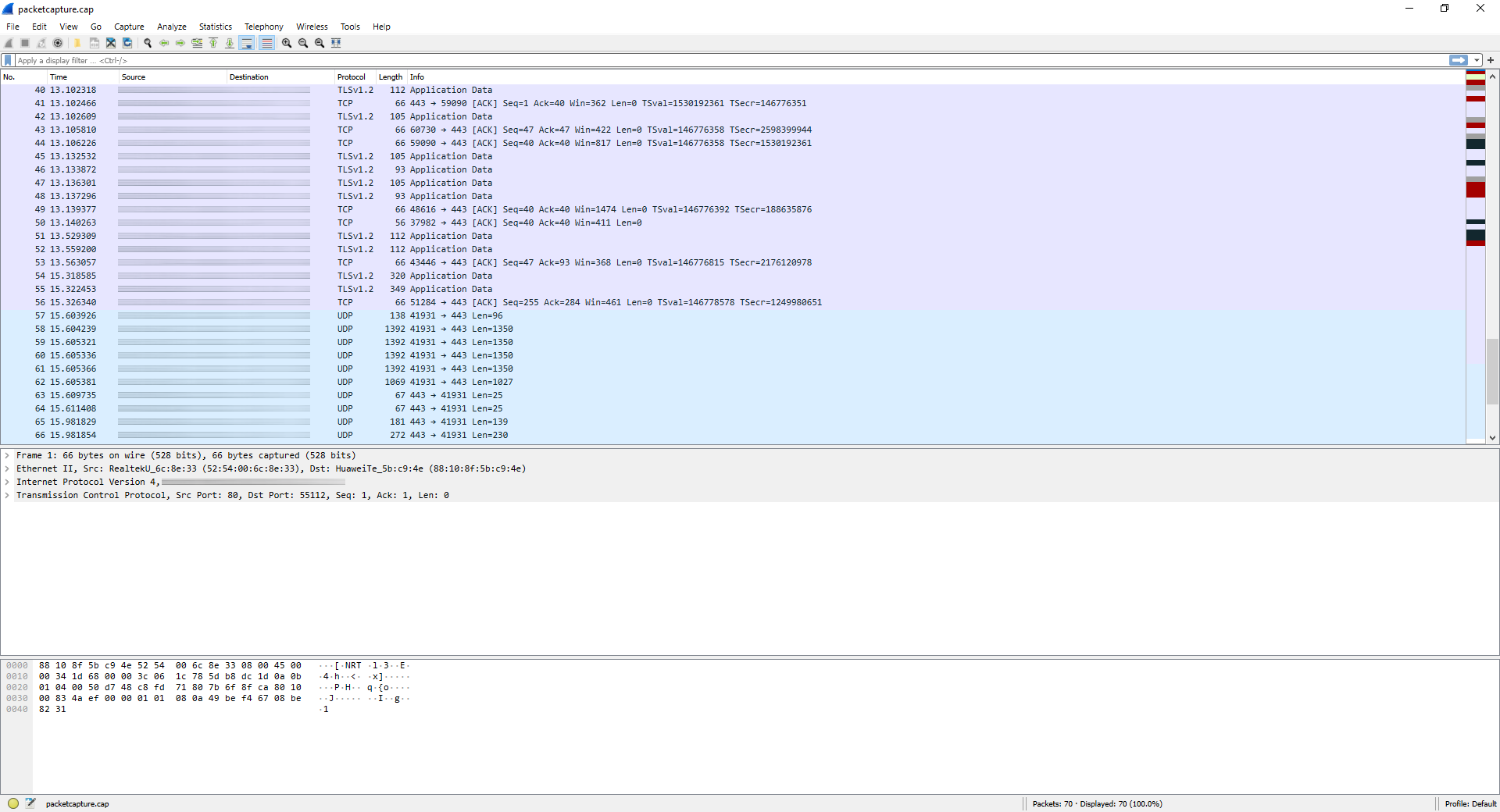
As you have seen, capturing the traffic with pfSense is really easy and simple, and it will allow us to detect possible communication problems of the different equipment, and rule out configuration problems of the switches, the pfSense or directly in the PCs.